- Cisco Community
- Technology and Support
- Security
- Network Access Control
- [CISCO ISE][12935 ] Supplicant stopped responding to ISE during EAP-TL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
[CISCO ISE][12935 ] Supplicant stopped responding to ISE during EAP-TL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 07:04 AM - edited 04-25-2024 07:06 AM
Hello Everyone,
I am contacting you all because i don't seem to find the needed information to resolve my issues, even though there are many similar topic as mine with the same error.
We have an infrastructure using FTD ASA5506 with switch CISCO WS-C2960S-48TS-L, everything was working fine.
We have recently replace our firewall (since it's not upgradable anymore) with a FortiGate 60F.
Everything is working fine except for the user's devices that can't authenticate on the switch and receive the correct VLAN ID.
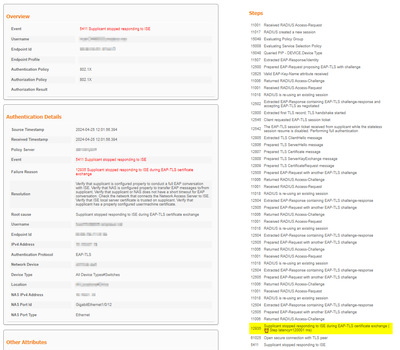
For some reason we get the following error on the CISCO ISE :
I hope you can help us on this matter
Let me know what information i can give you to help us resolve this problem.
Thank you all for your time and help.
Best regard
- Labels:
-
AAA
-
Identity Services Engine (ISE)
-
Wired
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 04:47 PM
Hello @Shabin ASOKAN
I have a suspicion that this is related to incorrect MTU size, since the EAP failure mentions there is a breakdown during cert exchange. In a typical EAP cert exchange (client or server) the total size of all certs (Root, Intermediate) tends to be larger than 1500 bytes.
If the FW was acting as a default gateway for the VLAN that ISE is using for its Gig0 interface, then I am pretty sure that the MTU on that Fortigate interface is greater than 1500 bytes. There is a requirement to ensure that the L3 on the ISE Management VLAN is using an MTU of 1500. Anything bigger than that and the cert exchange will fail, because ISE does not support jumbo frames for its management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 02:40 AM - edited 04-26-2024 02:48 AM
Hello @Arne Bier,
Thank you for your reply.
I had read about that and checked the switch MTU which was fine, but did not think of checking the MTU on the firewall.
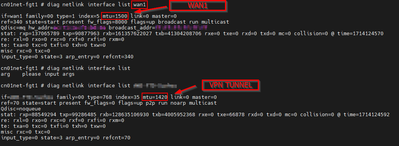
In our infrastructure context, the ISE is behind an IPsec tunnel, therefore, should it be the WAN interface's MTU that could be the problem ?
So far, here is what i found, WAN has an MTU of 1500 and VPN tunnel has an MTU of 1420 (see SC attached) :
If the MTU is smaller than 1500, could it also be a problem ?
Have a nice day.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 06:10 AM - edited 04-26-2024 06:14 AM
Hello @Arne Bier,
Turns out i have found another article in which you explained a few things in the link below :
What was interesting is the way to figure out the maximum MTU size accepted by the CISCO ISE, you propose to ping the cisco ISE, specifying the MTU size, in my case, the higher i can go is 1470, though my ipsec tunnel interface's MTU is 1420.
Just in case, i brought the MTU size down to 1300 for now, will test it next week since in can't access the remote device at the moment.
Should i maybe change the WAN interface MTU ?
I will keep you updated on the results next Monday, if this works, it will be a nice win for this end of week after a lot of research.
Thank you for your time and help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 02:17 AM
Hello @Arne Bier,
It would seem the change we've done last week hasn't resolved our issue.
I will investigate some more, i only changed the MTU on the IPsec tunnel interface, should I maybe do it as well on the ISP interface ?
I thank you for your help.
Have a nice day.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 11:30 PM
I hate messing around with MTU sizes ... mostly because I don't know the best way to solve this (i.e. if, and what value to set the MTU, and in which places in the network). Is the Fortigate configured to drop UDP fragments? I don't see how else ISE (whose GigE interface has MTU=1500) is supposed to handle a large certificate exchange greater than1500 bytes without fragmentation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2024 03:49 AM
Thank you @Arne Bier for your help and time on this.
I have engaged a discussion with FortiGate, i hope they will help us resolve this issue.
I'll let you know our find in case it can help someone else.
Best regards.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide