Threat Actors are constantly on the prowl for new vulnerabilities that they can exploit to launch attacks, that affect not only organizations but impact the lives of hundreds of thousands of people across continents. Such attacks typically target enterprises which host mission-critical data, necessary to maintain day-to-day operations. Encrypting this data and rendering it useless ensures that organizations have an adequate incentive to pay ransom in the cryptocurrency demanded by the hackers for its release.
For example, the ongoing WannaCry ransomware attack impacted computer systems all over the world, that included health care providers causing widespread havoc, slowing down patient processing and care. A detailed analysis of WannaCry is provided by Talos (Cisco’s security research group).
Ransomware attacks have been around for a while and are well studied but recently, attacks against Internet of things (IoT) devices like smart watches, home appliances, CCTV cameras, cars and more, all susceptible to exploitable connectivity, have started to proliferate. These devices are vulnerable because they are manufactured without security in mind! Most have been shipped with hard-coded default credentials for login/telnet/ssh access making them inherently unsecure, hard to patch and ripe for exploitation.
For example, the Mirai botnet attack on Dyn used over 600,000 IoT devices and took down the network of major companies. KrebsOnSecurity lists a set of devices that were targeted by Mirai. As it stands today, attackers are using IoT devices found in home networks as botnet infrastructure but the lack of stability and predictability of these devices and the networks they are in pose serious challenges to a successful outcome for attackers. Threat actors are therefore actively trying to infect IoT devices in enterprise networks in addition to home networks posing serious problems for security practitioners in enterprise businesses.
The deployment of IoT devices, virulent threats like WannaCry, and the ever-evolving threat landscape pose a significant challenge to enterprise network security. Security providers constantly analyze, publish and update indicators of compromise (IOCs) for emerging threats, making it tough for enterprise security groups to not only keep track and ingest threat intelligence from the many diverse and ever growing sources but also keep the myriad of security devices deployed in their network up to date with the ingested security intelligence.
Another challenge faced by security practitioners is keeping up with the large volume of events detected by security devices and correlating across multiple independent events to quickly identify an attack in progress and the prioritization of the detected incidents so that they can be quickly acted upon.
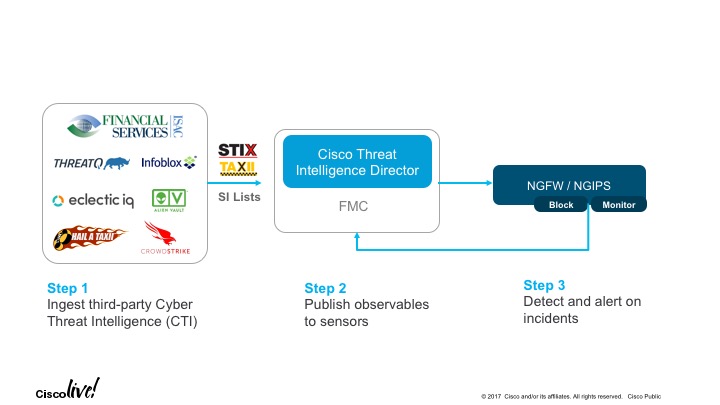
At the upcoming Cisco Live USA 2017 conference, please stop by my session where we will showcase Cisco Threat Intelligence Director (TID), an exciting new upcoming feature on Cisco’s Firepower Management Center (FMC) product offering that automates the operationalization of threat intelligence. TID has the ability to consume STIX over TAXII, simple blacklist intelligence and allows uploads/downloads of STIX and simple blacklist intelligence. All the imported intelligence is automatically operationalized and distributed to Cisco’s Next Generation Firewall (NGFW) product allowing the customer to configure defensive actions. A detection of the ingested intelligence on the network automatically generates incidents in real time that can be analyzed by customers. TID also has a rich set of APIs which can be leveraged to automate ingestion of intelligence, its management and the retrieval of incidents using 3rd party applications.
Course Session ID: DEVNET-1774
Speaker: Pramod Chandrashekar, Sr. Manager, Engineering, Cisco
Blog post by Pramod Chandrashekar and Yatish Joshi, Cisco
See you in Las Vegas! We have limited edition Snortinator Stickers!!!

