Attacks such as the one from WannaCry are a prime example of why companies need to complement traditional security approaches such as IDS/IPS systems and firewall appliances with Defense-In-Depth principles around Network Segmentation and Network Behavior Analysis (NBA).
WannaCry probably the most visible and dramatic, but certainly not the first or last of Day0 malware i.e. a new malware which due to the fact of not resembling any of the known malware families goes undetected by traditional IDS/IPS systems that rely on signature matching to detect malware. Sophisticated attackers are increasingly relying on such customized Day0 Malware to be able to bypass traditional security measures and exploit vulnerabilities in endpoints. Furthermore, attacks like the WannaCry ransomware are simply one of the many that have happened in the past and yet to come, given the explosion in number of connected devices and things that are vulnerable to attack, including the opportunity to exploit them for a financial benefit, as well as the easy accessibility of reference malware that have been leaked by previous attackers on the internet.
Through the use of algorithms that rely on "behavior" rather than signatures, solutions around Network Behavior Analysis are able to alert you on potentially suspect activities without relying on a malware signature match, and thereby provide a layer of visibility for day0 attacks. A fantastic write-up on how StealthWatch (from Cisco's Lancope acquisition) enables you to discover and detect instances of malware such as WannaCry is something I highly recommend you read to better understand specific functionality of Lancope StealthWatch in relation to WannaCry.
While there are quite a few solutions in the market that offer NBA capabilities, StealthWatch is one of the few that leverages NetFlow as the source of data to analyze on and detect threats; versus most of the other approaches that rely on the full network traffic replicated through an independent traffic mirroring infrastructure or happen to have to be installed inline to the traffic at various critical inspection points in the network.
The choice of using NetFlow as the source of data to derive security insights from has some profound implications.
For starters, this certainly lowers the cost and complexity of the deployment, since NetFlow can be derived directly from the network infrastructure itself and does not need a separate network traffic capture infrastructure. Telemetry from NetFlow is a highly summarized representation of the actual traffic itself, while at the same time providing you rich information about the flows, including application-ID, user-id, path information, QoS metadata, etc. This allows the limited network bandwidth to be maximized to carry the actual traffic itself and not multiple replicas of the same traffic for different services such as security analytics, application visibility, performance monitoring, etc.
From a security perspective, however, NetFlow being summarized information from the source, can be captured and analyzed at scale compared to solutions that rely on traffic replication. And when it comes to the efficacy of a security analytics solution, or analytics solution for that matter, there is a direct correlation between the volume & variety of data, and the insights that can be derived out of it. Which is again where using NetFlow as a source of data for security analytics really shines through.
The breadth of portfolio that supports NetFlow spanning network switching, routing, wireless, firewalls, endpoint and application agents enable the capture of traffic telemetry from a variety of points, that can then be correlated to present a detailed picture of all activity on the network, and alarm on the suspect activity on the network. For instance, in the case of the WannaCry malware, connections to a Tor network and an unusually high number of peer-to-peer SMB flow initiations from a host that also had a Tor connection established, would be tell-tale signs of potential malware activity that would trigger a security alert.
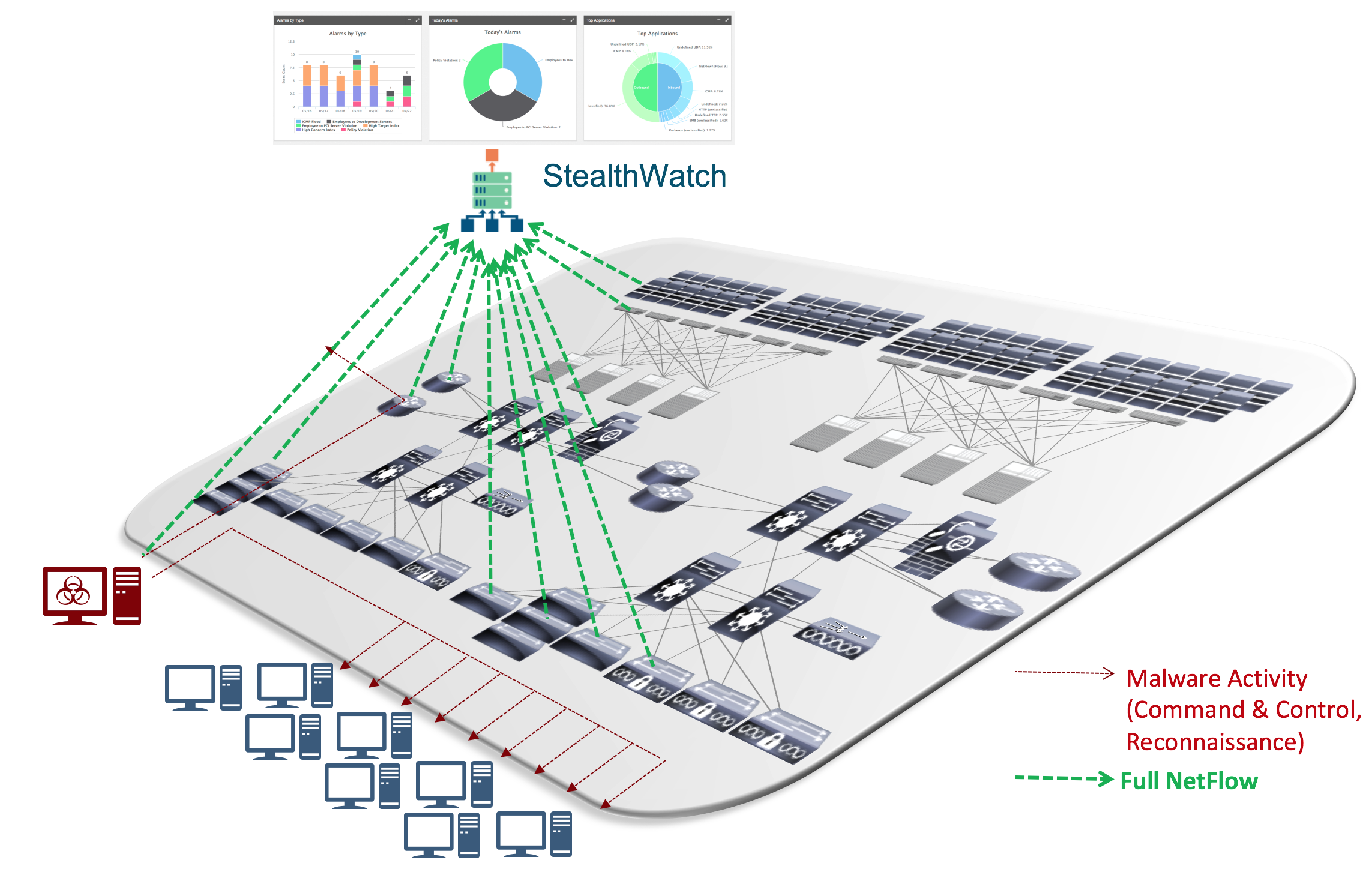
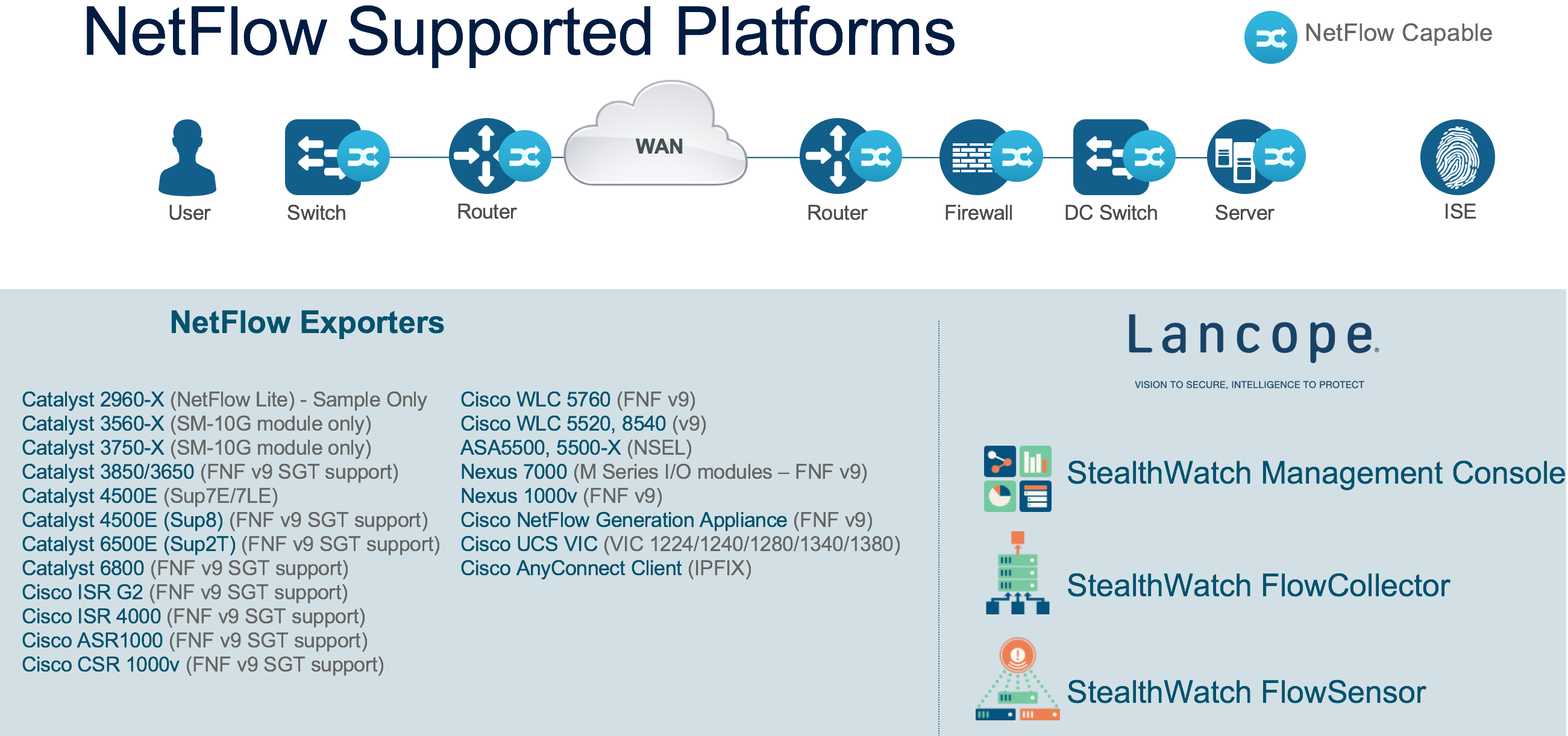
Especially when it comes to detecting network reconnaissance activity i.e. an infected endpoint that trying to discover other devices on the network to attack, capturing NetFlow from the access layer of the network is critical obtain a full picture of the endpoint activity. The network access layer is the first hop where users, devices (and things!) connect, and the network access infrastructure by capturing the full endpoint activity maximizes the efficacy of security threats in your environment. Network access infrastructure which effectively provides this includes Catalyst 3850, 3650 and 4500 series switches; and Wireless LAN Controllers 8540, 5520 and 3504. A more comprehensive listing of all the various platforms supporting Full NetFlow is below:
Lastly, using NetFlow along with a StealthWatch can provide a "time-machine" view of your network upto one year of all network activity, that lets you to replay and analyze user and application activity, providing you valuable visibility and insights to improve your security controls and defend against future attacks.
Security analysts have long been preaching demise of a "perimeter-based" security architecture and urging the community to implement and practice defense-in-depth principles also quite popularly known as a Zero-Trust Security Architecture where everything is untrusted by default and continually inspected for threats. Attacks like WannaCry are a wake-up call to review readiness and controls in place to be able to quickly detect, contain and defend against an ever-changing threat landscape. Ensure Network Behavior Analytics is a critical capability you are leveraging towards this, and are effectively incorporating the broad visibility provided by network data into your security operations.
To learn more about securing your environment using Lancope StealthWatch and NetFlow for network behavior analysis, refer:
http://video.cisco.com/detail/videos/security/video/5315592839001/digital-network-architecture-security
http://www.cisco.com/c/en/us/solutions/enterprise-networks/enterprise-network-security/index.html
http://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/enterprise-network-security/white-paper-c11-736595.html
http://www.cisco.com/c/dam/en/us/solutions/enterprise-networks/stealthwatch-netflow-ise-infographic-en.pdf
http://www.cisco.com/c/dam/en/us/solutions/enterprise-networks/stealth-watch-infographic-en.pdf
