This blog extends information from Cognitive Threat Analytics (CTA) Release Notes.
October 2017 Updates
- Advanced Stealthwatch flow record classification capability and lateral services monitoring
- Enhanced anomaly detection: Cognitive Analytics added a new set of anomaly detectors for Stealthwatch flow records based on global reputation and TLS features. This enhancement improves contextual information of individual incidents and increases the efficacy of the detection engine.
- New types of incidents: Cognitive Analytics added a new set of classifiers for detecting:
- Stealthy Command and Control communication channels by analyzing long-term behavior of users and devices.
- Unexpected DNS usage caused by DGA-based malware or data tunneling.
- Malicious SMB service discovery typical for fast-spreading malware such as WannaCry.
Following is an example screen shot of a malicious SMB service discovery incident; note that the infected user is contacting unexpected server IP addresses and countries with SMB service protocol:
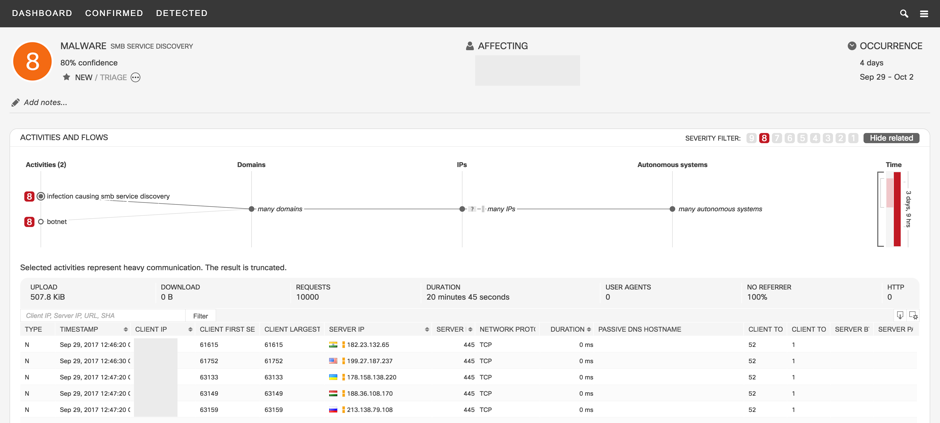
Note: You must have Cisco Cognitive Analytics configured on your Stealthwatch System to use these features. Cognitive Analytics quickly detects suspicious web traffic and/or Stealthwatch flow records and responds to attempts to establish a presence in your environment and to attacks that are already under way. For more information, go to the Cognitive Analytics website or the Cognitive Analytics documentation.
Following is an example screen shot of unexpected DNS usage, caused by DGA-based malware or data tunneling; note that the user has abnormally high number of DNS requests, valid or invalid, and transfers large amount of data in both directions:

The new detection mechanism is able to detect BitTorrent clients in the network. The detection is independent of used ports and transferred data, as well as any other network flow statistics. Therefore, the detector is able to detect active BitTorrent clients in the network that use non- standards (randomized) ports and do not actively participate in file sharing activity. Following is an example screen shot of a torrent incident; note that the user is contacting 972 server IP addresses:

The data sent to the Cognitive Analytics engine is filtered so that only flow records that cross the network perimeter are sent to the cloud. This filter is based on the Host Groups configuration – the flows that are going from the inside to outside host groups are sent for analysis (+DNS requests flows which are sent even for internal DNS servers). The enhancement in v6.10 adds the possibility for the user to modify the data that is sent by adding internal host groups to be monitored by the Cognitive Analytics engine. By configuring an internal host group to send Stealthwatch flow records, the user adds additional data to be sent to the cloud for analysis. Adding specific host groups to Cognitive Analytic monitoring is especially useful for company internal servers – adding traffic from the end users to those servers can improve a visibility of the exposure of the data that can be potentially misused by malware running on the affected devices.
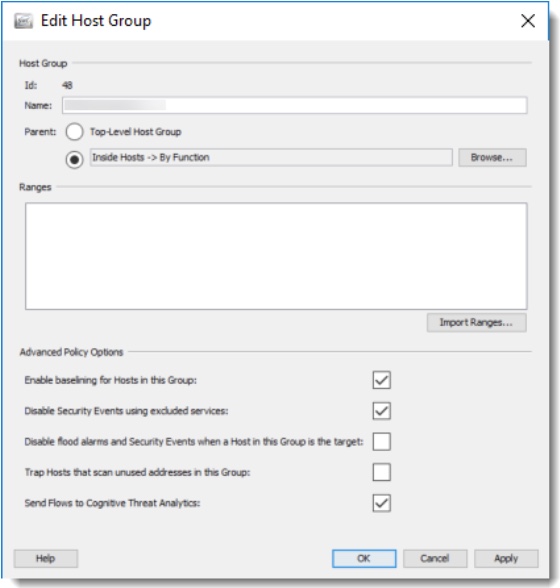
Following is a telemetry processing diagram for Lateral Services Stealthwatch flows from selected host groups:
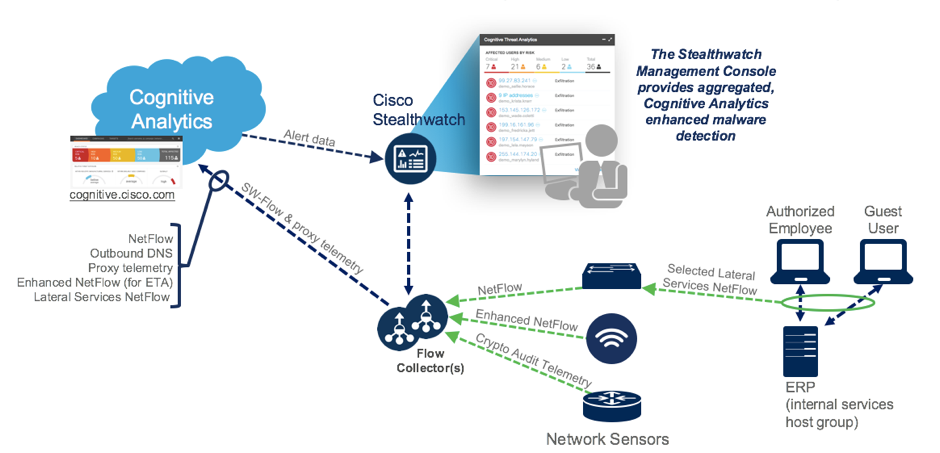
There is a new pivot point from within the CTA portal over to Stealthwatch Management Console (SMC) to further investigate an activity of a particular remote IP. There are new links next to the remote IP addresses that will open up the Stealthwatch Management Console (SMC) Host Reports for that particular IP.
