Overview
This demonstration for Android and Apple devices allows Cisco Field and Channel Partners to show how integration between Cisco Identity Services Engine (ISE) and Mobile Device Management (MDM) platforms provides necessary insight into the posture of mobile devices to enforce network access policies. MobileIron is a leading provider of MDM software used to establish and enforce device policy on hand-held endpoints. This could include corporate- or employee-owned phones and tablets.
Check it out here: Cisco ISE 1.3 for Mobile Device Management with MobileIron 7.5 v1.
What's New
- Upgraded MobileIron to 7.5
- Upgraded Cisco ISE to 1.3
- Updated vertical web landing portals
Scenarios
- Device Compliance
- Device Restrictions
- Application Distribution
Requirements
| Required | Optional |
|---|
- Preferred Endpoint Router
- 819W router, registered and configured for Cisco dCloud
- Monitoring Workstation
- Laptop with AnyConnect client
- User Devices
| Supported Endpoint Router/AP - Router, registered and configured for Cisco dCloud
- Cisco Aironet Series Access Point (3000, 2000, 1000 or 600 series)
|
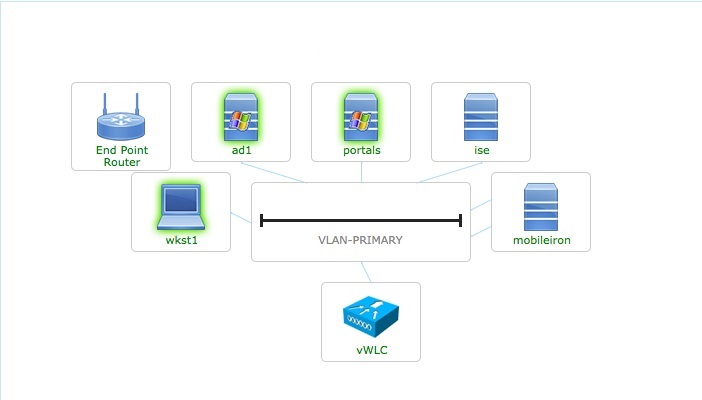
Components
- Cisco Virtual Wireless Controller (vWLC) 8.0
- Cisco Identity Services Engine (ISE) 1.3
- Microsoft Active Directory-Windows 2008 R2
- MobileIron 7.5
Features
| Device Restrictions | - There are two common types of restrictions. Either some feature of the device is disabled, such as the camera, or there are additional requirements for basic usage.
- When a restriction is in place, the user is not offered the choice of non-compliance. Restrictions are used to reduce security risks to the enterprise.
|
| Device Compliance | - MobileIron can check the attributes of the device against a list of acceptable operational conditions.
- Compliance can be used to increase security or reduce operational costs.
|
|---|
| Application Distribution | - The MDM can offer a company catalog of available software or install required software. The software can come from public repositories or can be corporate developed applications.
- Security is enhanced because any software distributed by the MDM, including local storage associated to the software, is removed as part of a corporate wipe. This is not true if the user installs the same software from the Apple App Store.
|
|---|
Topology