- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE and pfSense - Captive Portal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 09:15 AM
Hi. I was wondering if anyone has been able to get the captive portal functioning with ISE. We would like to use the ISE portals in this scenario. If anyone has, is there a step by step out there somewhere to follow? I'm running into some issues and need to demonstrate this ability. Thanks in advance!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 11:05 AM
this is a rather general comment is there a specific use case or flow you're asking for?, there are many docs on how to get started under the communities.
Identity Services Engine (ISE)
Look under guest
ISE Guest & Web Authentication
under documentation there is
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 10:17 AM
You can find a really good step-by-step here:
http://www.network-node.com/blog/2016/1/2/ise-20-guest-wireless-policy
It is for a sponsored guest portal but you can tweak it if you want to only do a hotspot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 11:05 AM
this is a rather general comment is there a specific use case or flow you're asking for?, there are many docs on how to get started under the communities.
Identity Services Engine (ISE)
Look under guest
ISE Guest & Web Authentication
under documentation there is
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 11:37 AM
pfSense is an open source firewall, so my guess is that you are trying to use ISE Guest Portal as a way to webauth firewall users. ISE is not a general purpose web server and web auth via ISE assumes specific capabilities on the access device (the firewall in this example). I would not say impossible, but will say integration may be difficult as would require understanding of how LWA flow works (whereby ISE returns credentials to NAD via POST command) which we don't document. Typical web auth is performed via CWA (a different mechanism whereby ISE never returns credentials to NAD).
/Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 12:14 PM
Thanks folks. I appreciate the feedback. The guides are definitely a help. Right now I'm just trying to authorize with the built-in portal and it's getting failed. I have searched quite a bit and can't find anyone who has done this with ISE (or ACS for the matter), so I guess my first issue is getting the right attributes to pfSense. Like chyps says, it is open source and I know that there is going to be some work need put in to make it all run with a portal, but I wouldn't think it would be an issue just to get a RADIUS accept. So I was hoping that someone had this working and could point me in the right direction as to what to send back in the authorization profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 12:26 PM
Per previous, this is not something we expect to work out of the box, and may not even with some special coding on pfSense side. Access-Accept is tied to a RADIUS session, not a simple web page login. With legacy LWA flow, the user is sent to a web page by NAD and ISE captures and returns the credentials submitted by user back to the NAD which in turn sends to ISE in a separate RADIUS request. I am not aware of any documentation that details the requirements on NAD to allow this flow with 3rd-party. The CWA flow relies on support for URL redirection and CoA, and I highly doubt the firewall is capable of processing this flow without a high amount of customization.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 12:40 PM
So, I guess to be more specific, pfSense has a built-in portal and can simply send out a RADIUS query without engaging the ISE captive portal mechanism. I've been able to get access-accepts from other devices use ISE and RADIUS, but for some reason this device is giving me problems.So I'm not sure if it's getting what it needs from ISE or if there is another issue.
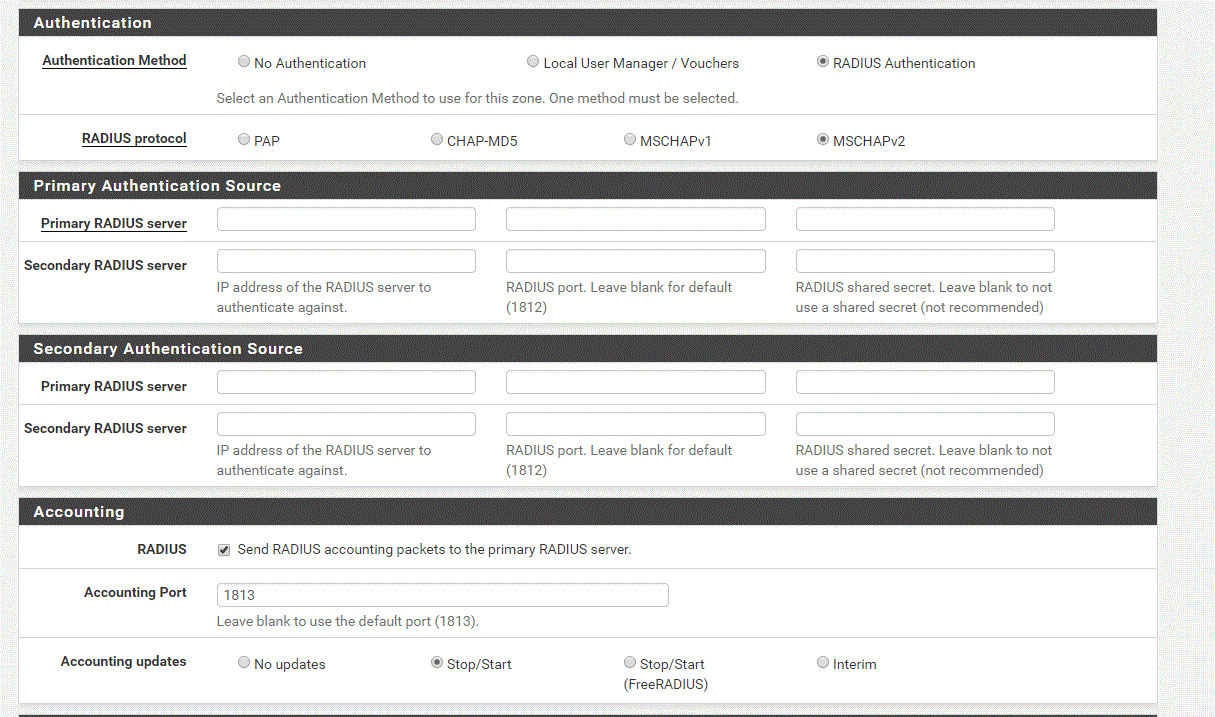
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2017 01:24 PM
Christopher,
Your initial query was specific to portal integration so now sounds like you are reverting the conversation to be about pure RADIUS auth without any integration of ISE portal.
"I was wondering if anyone has been able to get the captive portal functioning with ISE. We would like to use the ISE portals in this scenario." => "pfSense has a built-in portal and can simply send out a RADIUS query without engaging the ISE captive portal mechanism"
For starters, make sure you enter IP address of PSN or LB VIP into RADIUS server address in your form! :-)
Next, you need to enable MSCHAPv2 under the Allowed Protocols for Default Network Access, or create custom Allowed Protocols entry which include MSCHAPv2 to match your auth protocol selection. As a quick test, you can select PAP instead which is enabled by default.
/'Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2017 07:57 AM
Actually, it is about both ![]() I wanted to start out with the internal portal and make sure it works and then work in the custom portal. I just posted the pic to show what was available, but I did set up the items as you lay out above. I know pfSense can recognize the wispr attributes, I'm just not sure if anything other than an accept or reject is needed to be returned from ISE to get a good authorization.
I wanted to start out with the internal portal and make sure it works and then work in the custom portal. I just posted the pic to show what was available, but I did set up the items as you lay out above. I know pfSense can recognize the wispr attributes, I'm just not sure if anything other than an accept or reject is needed to be returned from ISE to get a good authorization.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

