- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE RADIUS VSA question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2018 11:20 AM
I am trying to integrate an APC PDU to authenticate with RADIUS on ISE. This requires a vendor-specific attribute to be set. I created an APC dictionary with the attributes, and an APC profile that uses the APC dictionary. The PDU network device is set to use the APC profile. On ACS, there was a spot to set the attribute, but I haven't figured out how on ISE. Can anyone tell me what steps I am missing?
The RADIUS LiveLog shows the login successful, but the PDU doesn't allow the login.
Thanks
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2018 12:39 PM
I used How do I configure my RADIUS server to authenticate my APC Network Enabled device? to come up with the attached dictionary file, which you may import to ISE per RADIUS-Vendor Dictionaries
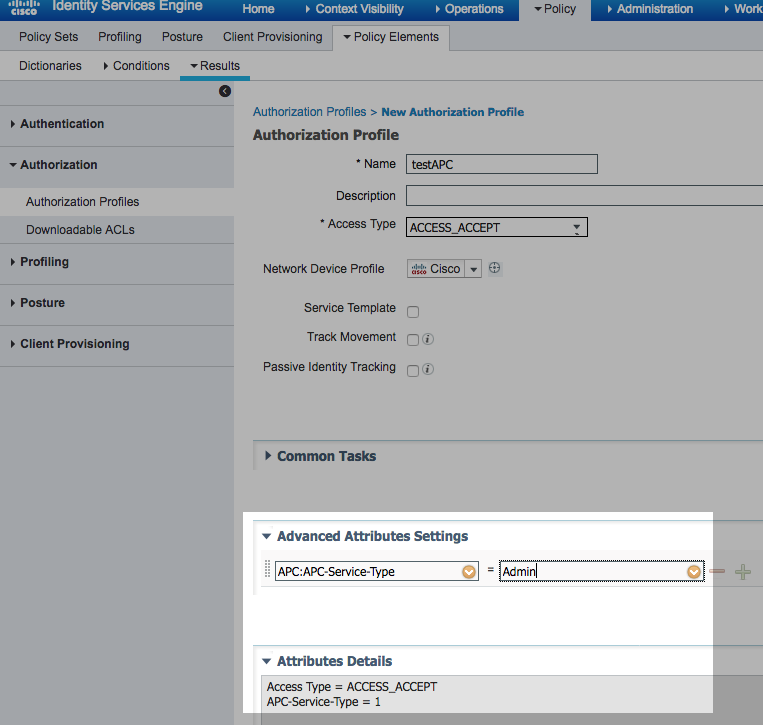
Then, use it in an AuthZ profile using the advanced attribute settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2018 12:39 PM
I used How do I configure my RADIUS server to authenticate my APC Network Enabled device? to come up with the attached dictionary file, which you may import to ISE per RADIUS-Vendor Dictionaries

Then, use it in an AuthZ profile using the advanced attribute settings.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2019 02:17 PM - edited 01-31-2019 02:26 PM
Hello thanks for your post I was able to follow the APC guide to set up radius authentication to the web management. I am now trying to integrate the Netbotz Card access to ISE as well. Has anyone had any success. I have imported the dictionary file from APC and have the attributes set in my authorization profile (AuthZ-APC-Admin)
Access Type = ACCESS_ACCEPT
APC-ACCPX-Doors = BothDoors
APC-Username = User1
APC-ACCPX-Access4 = Wed,00:00,23:59
APC-ACCPX-Access1 = Sun,00:00,23:59
APC-Service-Type = 1
APC-ACCPX-Access3 = Tue,00:00,23:59
APC-ACCPX-Status = Enabled
APC-ACCPX-Access2 = Mon,00:00,23:59
I create the a new use using the local identity store with card number as the user and the password that was setup in the radius config on the netbotz. What I am not sure of is how to apply the APC attributes to each of the new cards(users) I set up.
Her is the APC site is used for reference.
https://www.apc.com/us/en/faqs/FA156100/
Any help would be greatly appreciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2019 08:39 AM
This is very useful. It worked perfectly. Thank you for posting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2020 06:34 PM
Can someone assist with ISE radius authentication for APC
This is what I have so far
- Imported the dictionary for APC
- created a Authorization Profile
- Added APC as a network device on ISE
- made sure secret key is the same thing on both APC and ISE Box
still not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 05:42 AM
Can someone assist with ISE radius authentication for APC
This is what I have so far
- Imported the dictionary for APC
- created a Authorization Profile
- Added APC as a network device on ISE
- made sure secret key is the same thing on both APC and ISE Box
still not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2018 12:44 PM
You would need to...
1) Configure ISE as the RADIUS server in APC with specific secret key.
2) Configure the APC device as a NAD in ISE with correct IP address and matching RADIUS key.
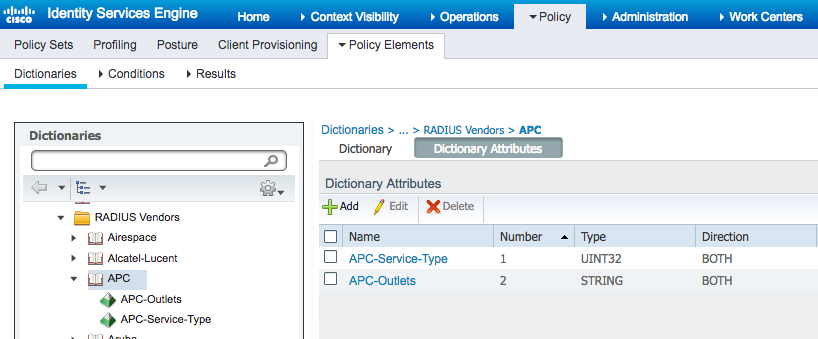
3) Create APC dictionary file - copy the following into text file with .dict extension:
VENDOR APC 318
BEGIN-VENDOR APC
ATTRIBUTE APC-Service-Type 1 integer APC
ATTRIBUTE APC-Outlets 2 string APC
VALUE APC-Service-Type Admin 1
VALUE APC-Service-Type Device 2
VALUE APC-Service-Type ReadOnly 3
VALUE APC-Service-Type Outlet 4
4) Import dictionary into ISE under Policy > Policy Elements > Dictionary > Radius > Radius Vendors
5) As an authorization to access APC, return the desired permission in the Authorization Profile under Advanced Attributes:
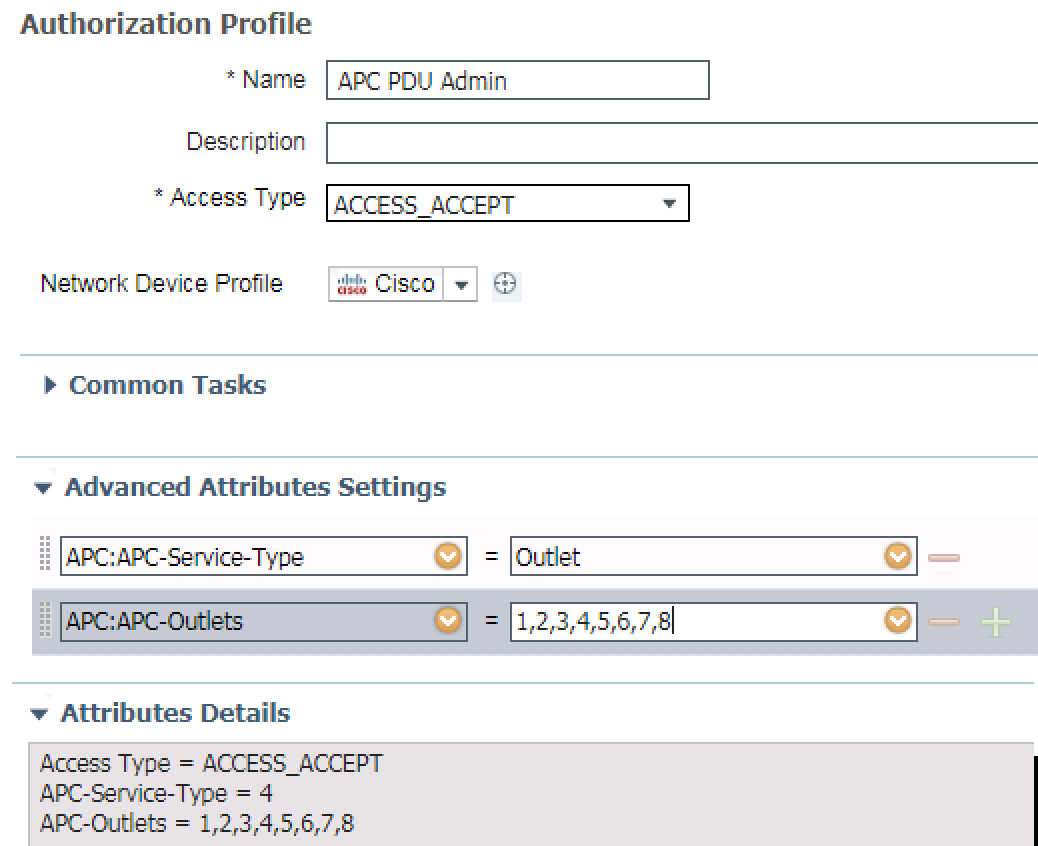
More info at How do I configure my RADIUS server to authenticate my APC Network Enabled device?
/Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2018 04:16 PM
Thanks for the answers. I finally got it to work. ISE 2.3 is picky about for Auth. profiles; I had to try several different things several times before it didn't give me a Auth. Profile not found when trying to authenticate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2018 12:15 PM
Cory,
Is there any way you can post a screen shot of your Advanced Attribute settings for the APC Authorization Profile? I imported the above VSA file and have tried the above settings and several others with no luck. Depending on my advanced attribute settings sometimes I get Authorized but still can't login in to the PDU.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2018 08:02 AM
I am trying to move from ACS to ISE and my ACS has the same settings as the example above but authentication doesn't work on ISE even though the dictionary and policies are the same on ISE as ACS. Does anyone know if there is something else in ISE that needs to be enabled for this authentication to work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2018 07:52 AM
Hi
Would it be possible to share the Policy set for this?
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-16-2018 01:53 PM
Just in case anyone is interested, I too had a problem with "15019 Could not find selected Authorization Profiles". I had to delete the Auth(Z) result, and then recreate it. Once I did that it worked. ISE seems to be finicky about the order policies are implemented.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2018 04:27 PM
Thanks a lot for contributing this info. If you have a specific sequence to recreate this issue and if you have a TAC case open on it, please ask TAC to open a bug. Otherwise, please let me know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-14-2023 12:18 AM
Maybe it is interessting, that it seems this bug CSCvs61423 is still not solved in version 3.1 patch 3.
But the workaround to delete and re-create the authorization result again is working.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

