While you are working on the Panoptica UI, have you noticed there are Panoptica CLIs?
The URL for the CLI documentation is here.
Panoptica CLI can do things like:
• Scans Docker images for Known vulnerabilities
• CIS Benchmarks
• Detect exposed keys/passwords/secrets
• And more
The scan result will also show up in Panoptica UI.
The documentation has all the detail you need, including what are supported platforms, installation steps and CLI usage.
Here is an example of how to use the CLI.
Step 1. Get your login for panoptica.app site if you haven’t done so
You will need to access the GUI to get the necessary keys for authentication.
It’s free to sign up
Step 2. Create a user with the Service role and obtain Access Key and Secret Key for executing CLI commands.
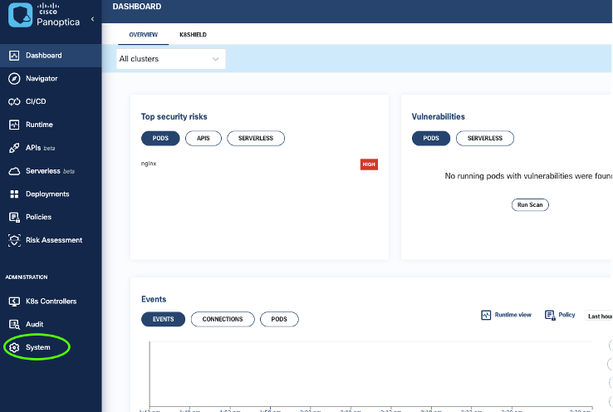
After logging into the panoptica.app site you should see the following screen (below).
Click on System to go to System page.
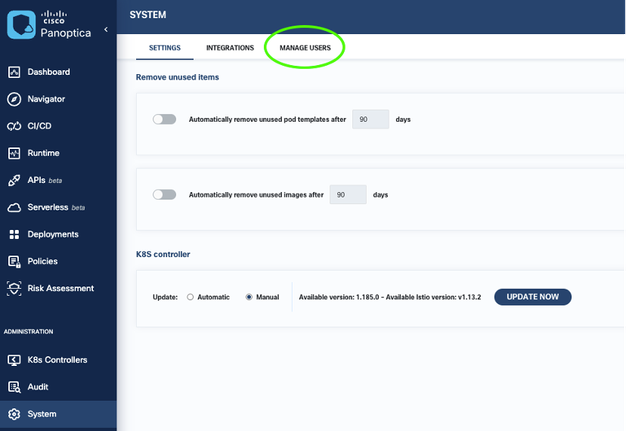
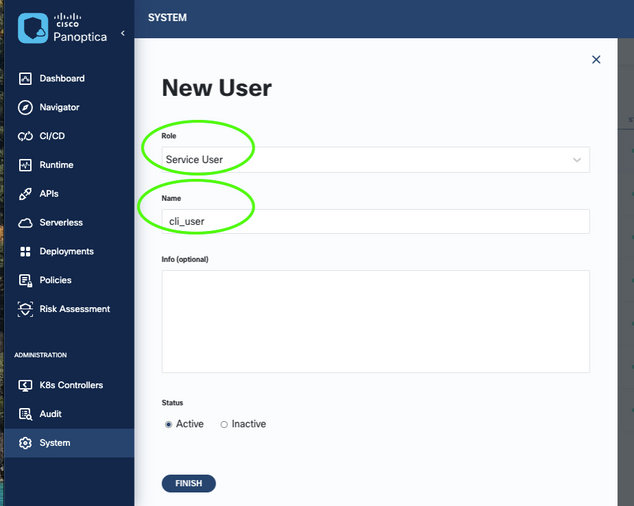
Click on MANAGE USERS then click on “+ New User”
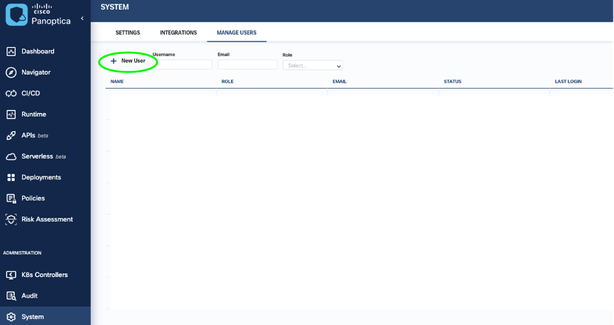
Once New User window pop up select role as “Service User” then provide a name, for example “clii_user”, then click the FINISH button.
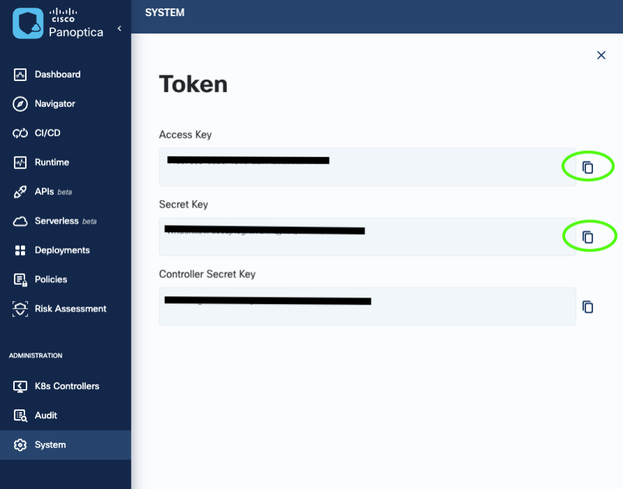
You should see a Token window pop up. Copy the Access Key and Secret Key and keep them in a safe place. These will be the keys you’ll need for CLI command input.
Step 3 . Download and Install CLI
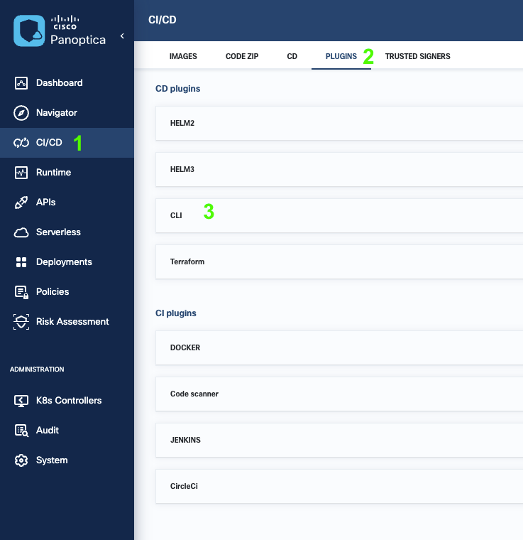
1. Navigate to the CI/CD page
2. Select the PLUGINS tab.
3. Scroll down to the CD Plugins section and select CLI.
4. Download the CLI using the link on the page, move the CLI file to the platform you want to execute the command if needed.
5. Verify the CLI file - securecn_deployment_cli – is executable
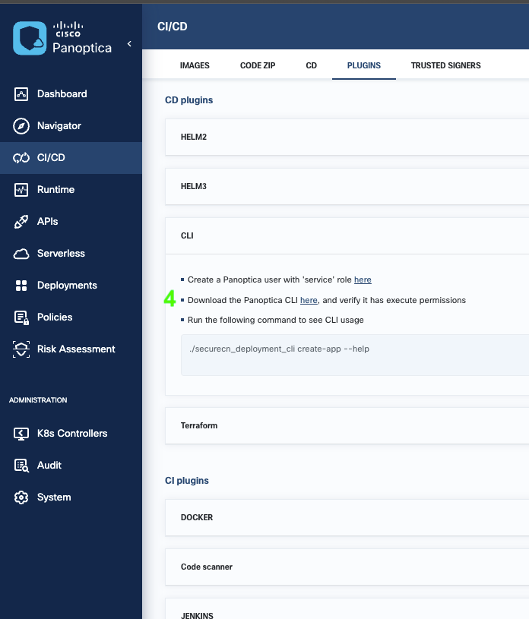
Now we have prepared everything we need. We can start using CLI.
Step 4 . Start Using CLI
As you can see, I have 2 images in Docker remote repositories.
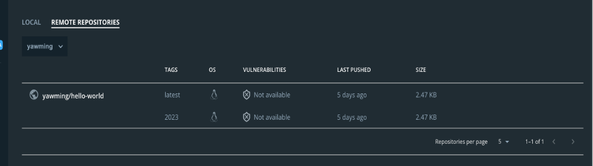
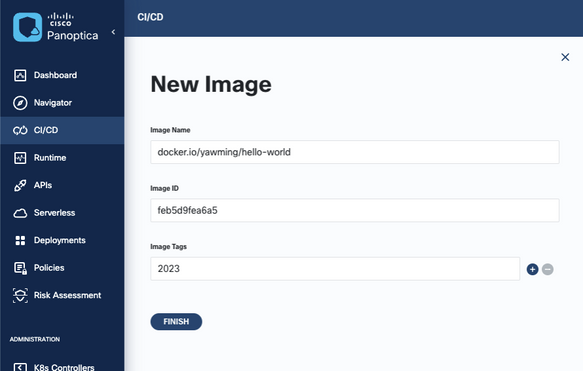
Now I will add “hello_world:2023” to Panoptica:

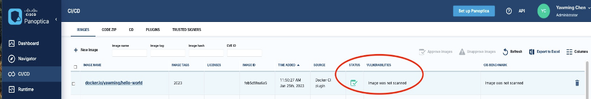
After clicking “FINISH” , the image is added but it’s not scanned (see the picture below). The only way to scan it is by using a CLI command.
So, let’s use CLI command to scan it. The CLI executable file is called securecn_deployment_cli and the scan command is called run-vulnerability-scan. You can use securecn_deployment_cli --help to list all available commands.
./securecn_deployment_cli run-vulnerability-scan --access-key <your access-key> --secret-key <your secret-key> --image-name=docker.io/yawming/hello-world:2023
(access-key and secret-key from Step 2)
And this is the output:
SKIP - DKL-LI-0001: Avoid empty password
* failed to detect etc/shadow,etc/master.passwd
SKIP - DKL-LI-0002: Be unique UID/GROUP
* failed to detect etc/passwd
* failed to detect etc/group
WARN - CIS-DI-0001: Create a user for the container
* Last user should not be root
INFO - CIS-DI-0005: Enable Content trust for Docker
* export DOCKER_CONTENT_TRUST=1 before docker pull/build
INFO - CIS-DI-0006: Add HEALTHCHECK instruction to the container image
* not found HEALTHCHECK statement
If we refresh the UI page, we can see the image is showing scanned.

Another example is to scan an image directly (not adding new image from UI).
./securecn_deployment_cli run-vulnerability-scan --access-key <your access-key> --secret-key <your secret-key> --image-name=docker.io/yawming/hello-world:latest
If we refresh the UI page after executing the CLI we can see the image is added and showing that it is being scanned.

We can scan locally as well (instead of pulling it from a remote registry)
./securecn_deployment_cli run-vulnerability-scan --access-key <your access-key> --secret-key <your secret-key> --image-name=hello-world --local
The “run-code-vulnerability-scan” just one of Panoptica CLI commands. You can do “./securecn_deployment_cli –help” to list all available commands to explore more.
./securecn_deployment_cli --help
NAME:
SecureCN cli
USAGE:
securecn_deployment_cli [global options] command [command options] [arguments...]
VERSION:
0.4.0
COMMANDS:
create-app Create an app
run-docker Docker integration with SecureCN
run-vulnerability-scan Docker image scanning integration with SecureCN
run-security-check SecureCN security check tool for kubernetes resources
sign-image Sign image
run-code-vulnerability-scan Source code scanning integration with SecureCN
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
--help, -h show help
--version, -v print the version
For more code vulnerability scan information please refer to Panoptica Documentation Code vulnerability scanner.