- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- D289: Release Notes for Apr 26, 2024
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-26-2024 08:02 AM - edited 04-29-2024 08:07 AM
- New features, enhancements, and other improvements
- Now in public preview: Risk-Based Factor Selection Preview Mode
- Duo Single Sign-On OpenID Connect (OIDC) applications now support refresh tokens
- Now generally available: Verified Duo Push in the Duo Auth API
- Now generally available: Duo Universal Prompt support forDevice Management Portal
- Clearer language for blocked authentications in Authentication Logs
- Updates to the Universal Prompt Progress report
- Less secure authentication methods disabled by default for new Duo customers’ administrators
- Subaccount reparenting process streamlined
- New and updated applications
- Four new named SAML applications with Duo SSO
- Duo Network Gateway version 3.1.0 released
- Duo Desktop for Linux version 3.0.0 released
- Duo Mobile for Android version 4.63.0 released
- Duo Mobile for iOS version 4.63.0 released
- Bug fixes
Hello everyone! Here are the release notes for our most recent updates to Duo.
Public release notes are published on the Customer Community every other Friday, the day after the D-release is completely rolled out. You can subscribe to notifications for new release notes by following the process described here. If you have any questions about these changes, please comment below.
Check out the Guide to Duo End-of-Life and End-of-Support Plans. This guide provides an up-to-date list of current and past end-of-life plans for Duo products.
New features, enhancements, and other improvements
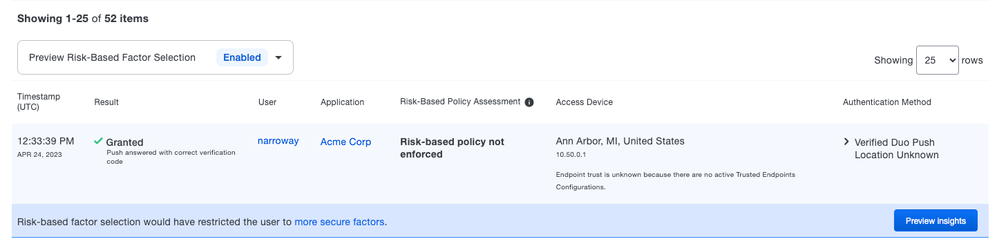
Now in public preview: Risk-Based Factor Selection Preview Mode
- To enable preview mode for Risk-Based Factor Selection, navigate to the Authentication Log in the Duo Admin Panel, select the Preview Risk-Based Factor Selection drop-down, and then click the Show preview mode UI elements toggle switch.
- Once enabled, administrators will see the "Risk-Based Policy Assessment" column and a banner in the Authentication Log on authentications that would have required a step-up authentication.
- Administrators can click on the Preview Insights button next to an authentication to see more information about the potential impact of the Risk-Based Factor Selection policy.
Duo Single Sign-On OpenID Connect (OIDC) applications now support refresh tokens
- OpenID Connect (OIDC) applications for Duo Single Sign-On can now be configured to issue and consume refresh tokens to allow users to keep their sessions active in supported applications longer without having to authenticate as frequently.
Now generally available: Verified Duo Push in the Duo Auth API
- Website or application clients using Duo’s Auth API will now be able to require Verified Duo Push from both regular authentications and authentications that have been restricted by Risk-Based Factor Selection.
- In order to use Verified Push, the client must be updated to use the following API endpoints:
- When the user begins an authentication that requires a Verified Duo Push:
- /preauth must be called first, with the additional parameter client_supports_verified_push with a value of 1.
- The response from Duo’s Auth API will include txid, verification_code, and expiration.
- The client must display the verification code to the user.
- The verification code is valid for 60 seconds.
- When the user completes the Verified Duo Push authentication:
- The post response to the /auth endpoint must include the txid parameter included in the response to /preauth. The factor parameter must be push or auto in order to prompt a Verified Duo Push.
- If user authentication is asynchronous, the /auth_status response will include the verification code in the status_msg field.
Now generally available: Duo Universal Prompt support for Device Management Portal
- Administrators using an on-premises Device Management Portal application can now migrate to the Universal Prompt.
- An existing Device Management Portal application requires Duo Web SDK 4 or the Duo OIDC Auth API.
Clearer language for blocked authentications in Authentication Logs
- If a user’s authentication is blocked due to their Duo Mobile app version, the Result column in Reports > Authentication Logs will now specify “Duo Mobile version restricted” instead of the broader “Version restricted.”
 The Authentication Log displays the message "Duo Mobile version restricted" in the Result column.
The Authentication Log displays the message "Duo Mobile version restricted" in the Result column.
Updates to the Universal Prompt Progress report
- Out-of-scope applications are now categorized as No action required by default. They also contain a Universal Prompt section on their individual application details page.
- The new Remediate filter under Action required shows applications that still have Traditional Prompt usage despite being out of scope or having Universal Prompt already active. Administrators can download a CSV of Traditional Prompt authentications on these applications from the past 30 days.
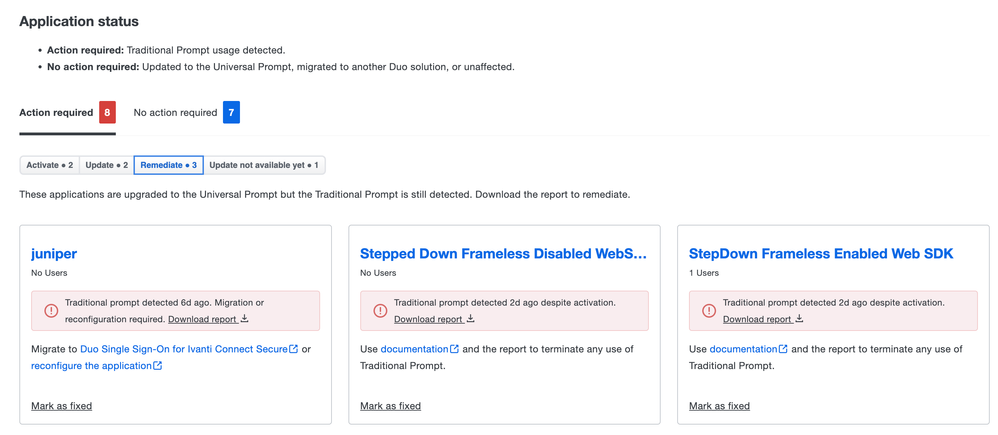 The Universal Prompt Progress report now has a Remediate filter.
The Universal Prompt Progress report now has a Remediate filter.
- Both in-scope and out-of-scope applications that fall under the Remediate filter due to Traditional Prompt usage also show an alert banner in the Universal Prompt section on their individual application details page.
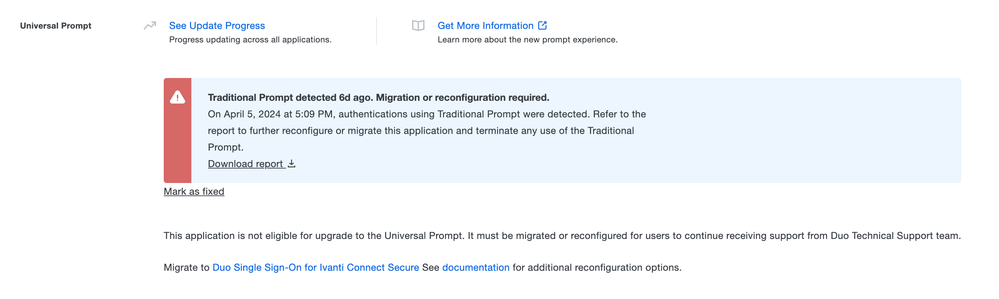 Applications in the Remediate filter will show an alert banner in the Universal Prompt section on their individual application details page.
Applications in the Remediate filter will show an alert banner in the Universal Prompt section on their individual application details page.
- Administrators can select Mark as fixed on an application under the Remediate filter to indicate an application’s remediation is complete. This will move the application back to the appropriate status.
Less secure authentication methods disabled by default for new Duo customers’ administrators
- For customers who signed up before April 2024, the default is set to allow all authentication methods. For customers who signed up during or after April 2024, the default is set to allow passkeys, Yubikey AES, Duo Push, and hardware tokens.
Subaccount reparenting process streamlined
- Subaccount reparenting can now be completed once owner administrators on both parent accounts approve the request, instead of first requiring de-parenting the subaccount from its original parent.
New and updated applications
Four new named SAML applications with Duo SSO
- There are now named SAML applications to protect Miro, Ping Identity, Nutanix and Bitdefender with Duo Single Sign-On (SSO), our cloud identity provider.
- Temporary attribute transformations for generic SAML service providers and temporary claim transformations for generic OIDC relying parties are now generally available.
- Reminder: Duo Access Gateway reached the last date of support on October 26, 2023. The DAG end-of-life milestone scheduled for March 30, 2024 was canceled. At this time, existing DAG applications will continue to work after March 30, 2024. Please see the Guide to Duo Access Gateway end of life for more details.
Duo Network Gateway version 3.1.0 released
- New web application setting to configure Proxy buffer size.
- New feature flag to enable worker thread shutdown timer in DNG scripted configurations.
- Updated lxml to 5.2.1 to address CVE-2022-1873.
- Updated golang.org/x/text to 0.14.0 address CVE-2022-32149.
- Updated Python to 3.10.13 to address CVE-2022-2464, CVE-2022-4568, CVE-2015-0814, CVE-2018-2503.
- Updated Dependencies: Rust to 1.76.0, Openresty to 1.25.3, isodate to 0.6.1, pbr to 6.0.0, Node to 20.11.1, and Go to 1.22.0.
Duo Desktop for Linux version 3.0.0 released
- Duo Desktop device registration is now supported on Linux.
Duo Mobile for Android version 4.63.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
Duo Mobile for iOS version 4.63.0 released
- Third-party accounts are more clearly indicated in the app, with the addition of "- Third-Party" after the account type. This will take affect for all existing third-party accounts, and will have no effect on Duo-Protected accounts. This will make it easier for end-users and those assisting them to determine whether an account talks to Duo's services or not.
Bug fixes
- The current Duo Single Sign-On for Cisco ISE SSO was reimplemented to support Multiple ACS URLs.
- Fixed a bug for passwordless mobile trusted endpoints to show “Device not allowed” language when a user’s device is not managed instead of "Duo Mobile required.”
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
4/29/24 edited to add "Now generally available: Duo Universal Prompt support for Device Management Portal"
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: