- Cisco Community
- Technology and Support
- Security
- Email Security
- Re: Connection to Url retrospective service failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Connection to Url retrospective service failed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2023 10:28 AM
Hi Team,
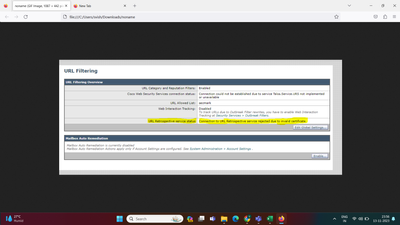
I have done an upgradation from 14.2.1-020 to 15.0.0 build 104 and after that facing an Error "Connection to Url retrospective service failure due to invalid certificate". Please find attached snap and let me know how can i resolve this.
- Labels:
-
Email Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2023 09:34 PM
If you are not using a proxy, ensure ESA can resolve and connect to these URL(s) on port 443.
-
prod-register-api.uce.cmd.cisco.com
-
prodap-retro-api.uce.cmd.cisco.com
-
prodeu-retro-api.uce.cmd.cisco.com
-
produs-retro-api.uce.cmd.cisco.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2023 09:00 PM
We are using proxy. How should we test connectivity to above url in that case ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2023 12:32 AM
If so, you either need to exempt the ESA from being decrypted, or add the root that the proxy uses for generating its certs to the ESA, just like you had to do for workstations (and that still might not work)
W used to use WSA, and we put the ESA in bypass.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2023 09:09 PM
I have checked and able to connect all 4 Url's, but still getting the Error of invalid certificate as per prevoius attachment. What could be the next i can do to resolve this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2024 04:45 AM
Just had a chat with TAC about this. A fix for this is scheduled for release 15.0.2 and 15.5.1. The Defect CSCwi59220 will soon be updated and the fixed releases will be out at the end of April.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2024 03:34 PM
@sv7 does issue still persist and do you need assistance or it has been resolved?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2024 02:13 AM
I'm still facing tje issue. I check and version 15.0.2 or 15.5.1 are not available yet. Latest version I can see is:
1. AsyncOS 15.0.1 build 030 upgrade For Email, 2023-11-22, This release is a
Maintenance Deployment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2024 04:51 PM
Did you upgrade yet?
15.5.1-055 ESA was released Tuesday 2 May.
We’re curious if your alerts stopped.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2024 12:23 AM
@sv7 , as mentioned by @Ken Stieers , probably session hits SSL Decryption policy in your proxy server.
you can do a packet capture on ESA (navigate to 'help and support' -> 'Packet Capture' page, set relevant filters [f.e. server IP address]), take capture, analyze it by wireshark and here try to find out relevant session, find and check certificate details provided by server during TLS handshake process to figure out by whom provided certificate. you can also share pcap file or some screenshots here.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide