- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Allow ISE captive portal DNS entry on outside DNS.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Allow ISE captive portal DNS entry on outside DNS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2023 10:19 AM
Hello,
We are having ISE for EAP/TACACS authentication and, hosted internally in our datacenter.
Now we have configured BYOD captive portal that tied to AZURE SAML authentication, the current captive portal redirect URL from ISE has prepended the node name of ISE server within the URL. However, our requirements are to use external DNS servers for this particular scenario in which captive portal URL resolve to internal IP by external DNS server as well the captive portal will use different hostname and domain name. I would like to know what steps we need to follow to achieve the same goal.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2023 12:00 PM
Hello @kshah2589
It's permitted to assign a private IPv4 address (which I assume you're using on your ISE Eth interfaces) to a public DNS A record.
I assume your BYOD clients are also getting a private IPv4 address when on-prem?
If so, then this allows the DNS A record to be in the public DNS domain, and when resolved, allow the client to establish the TCP connection to the ISE's web server.
The ISE Authorization Profile for the portal redirection should then set your desired static FQDN instead of using the FQDN assigned to the node when it was built.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2023 01:42 PM
Thanks, Arne Bier, for your suggestion.
1). We have assigned Private IP addresses from 10.x.x.x range to our ISE nodes. we have also separate VLAN for BYOD devices which using private IP addresses from 10.x.x.x range when on prem connect to SSID.
2). Do you want me to set desired FQDN as below in authorization profile, am I correct?
3). We have 2 ISE nodes in our environment Primary/Secondary and want to make sure do we need to make any additional changes once we put static FQDN? Also, FQDN will be resolve to what IP addresses, [Primary, Secondary, Both] by DNS?
4). Currently, the user has to manually trust the cert because we are using self-signed certificate but in future, we want use public cert issued by certificate authority so user don't have to manually trust the cert, what details should we include creating Certificate Signing Request - static FQDN or both ISE node name?
Let me know if you have any additional suggestions.
Regards,
Kunal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2023 02:30 PM
Yes - you set the static FQDN where you indicated. ISE will then insert that FQDN in the https URL redirection string.
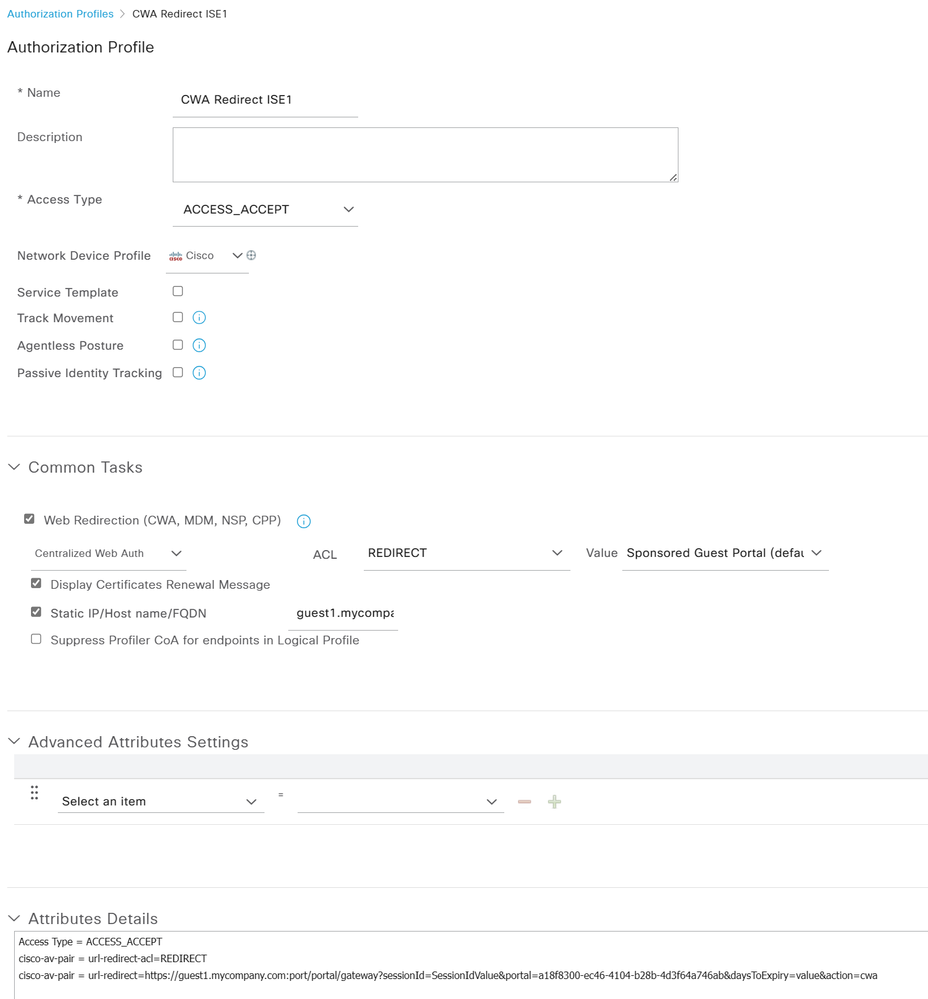
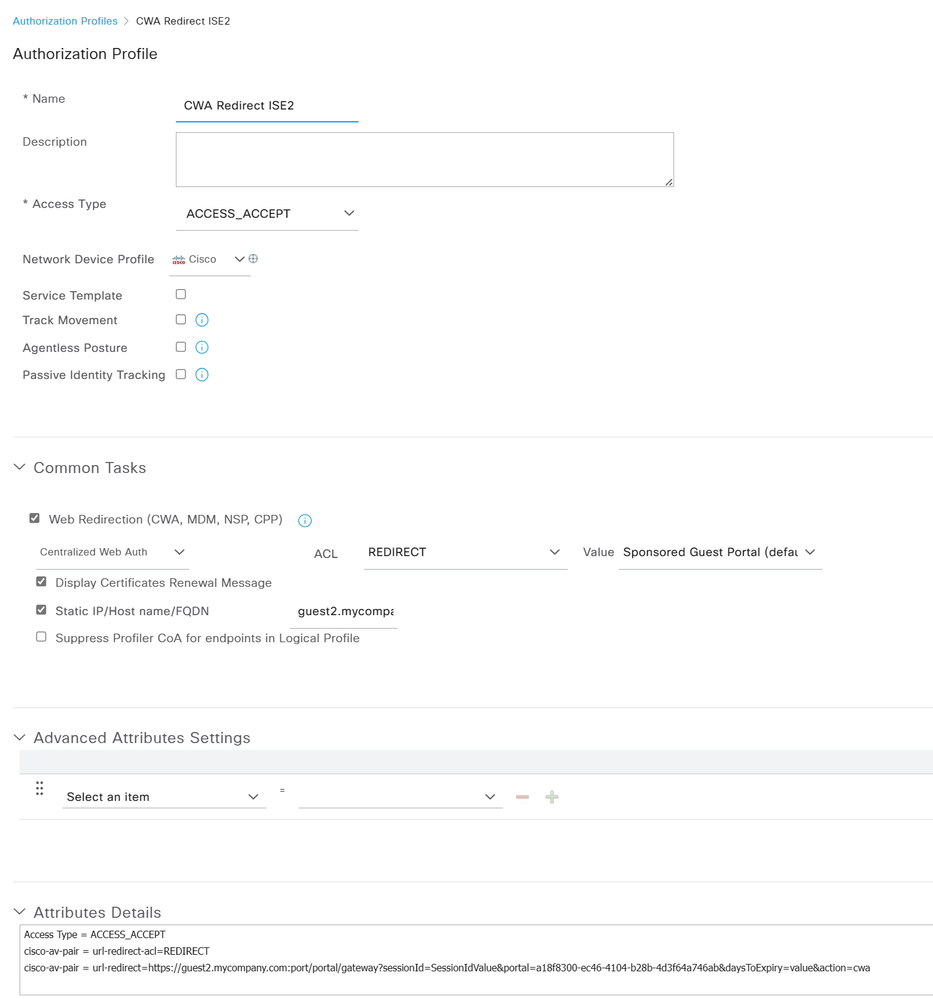
Which brings us to your HA question. The solution is surprisingly simple (it's been discussed a few times in the Community with screenshots too). You will need two Result Authorization Profiles
- AuthZ_1 = where the Static FQDN is portal1.mycompany.com
- AuthZ_2 = where the Static FQDN is portal2.mycompany.com
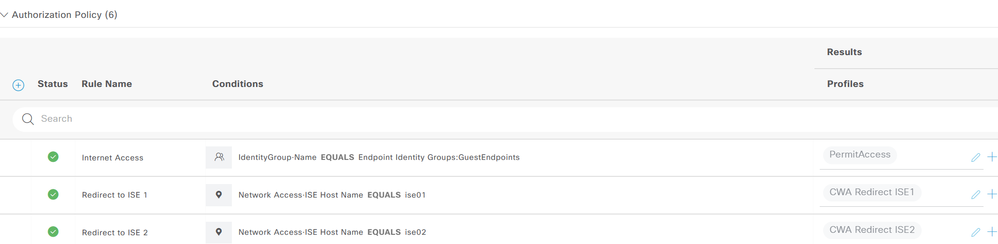
In the RADIUS Policy Set, during MAB Authorization, you have two Rules - each one checks the ISE Hostname and then returns the corresponding AuthZ above.
Let's assume your ISE nodes are called
- ise1.network.local
- ise2.network.local
then the Authorization Rule would check for Hostname EQUALS "ise1" then return AuthZ_1, etc.
Of course, to avoid browser certificate warnings, the Portal certificate must be one of either:
Wildcard cert (*.mycompany.com in the Subject Alternative Name) or a multi-SAN cert that contains
- DNS SAN 1 = portal1.mycompany.com
- DNS SAN 2 = portal2.mycompany.com
The multi-SAN certs are typically more reasonably priced than wildcard certs. But if you already have a wildcard cert, then you can use that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2023 07:16 AM
Thank you for detailed explanation and really appreciate your help.
1). We are looking for single captive portal URL instead of two, which resolves to ise1 for our east coast users and for west coast users it resolves to ise2 and in case if ise1 is not available it fall back to ise2 and vice versa. Is that something possible?
2). you did mention about solution discussed in community; do you have reference where I can look those screenshots?
Regards,
Kunal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2023 07:00 PM
Hi Kunal,
You will still have a single captive portal. What I am describing with the two Results Profiles and AuthZ Rules, is simply to let the right ISE node return its own Portal URL. If you don't do it like this, then you have to use a load balancer, and send the WLC's RADIUS traffic to the load balancer, and not to ISE1 & ISE2. I assume load balancer is out of the question for you?
Remember that ISE RADIUS servers do not provide any redundancy on their own, since that is not their responsibility. ISE nodes (or PSNs - Policy Service Nodes) all get the same RADIUS Policy Set programming - so they are identical from that perspective. They only differ in their hostnames (as seen on the ISE CLI - e.g. ise1.company.internal and ise2.company.internal)
The HA responsibility is on the NAS/NAD. So WLC will have Primary RADIUS and Secondary RADIUS IPs configured. That's it.
And with my explanation in the previous post, each ISE node that the WLC hits, will cause the correct ISE node to return its own URL to the client. Because that is what clients need - they only care about the final URL and then build a TCP connection. You can't build a TCP connection to an ISE node that is not expecting it - each session created a unique URL.
I can't find many of my early postings in this Community. I grabbed this from the lab. This is guest portal, but same logic applies to other portal types involving redirection.
Create two Authorization Profiles - take note of the static FQDN
Then create the Authorization in the MAB Policy Set
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2023 09:38 AM
Thank you so much Arne Bier for sharing the screen shots and detailed explanation.
1). We don't have a load balancer in our environment so will follow the steps you described in the post and also, we need to create two public DNS records one for each FQDN like portal1.mycompany.com - 10.x.x.1 and portal2.mycompany.com - 10.x.x.2, am I correct?
Regards,
Kunal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2023 12:04 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2023 12:44 PM
Thanks for quick reply.
1). most probably we will generate single CSR that contains both the node with following subject alternative name.
- DNS SAN 1 = portal1.mycompany.com
- DNS SAN 2 = portal2.mycompany.com
I am still not sure about subject common name, what's your recommendation?
2). I was researching on certificate topic, the document mentioned about group tag for portal use, what's that and what else we need to keep in mind to set it up correctly to avoid browser certificate error.
Regard,
Kunal Shah
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2023 02:15 PM
One CSR for both nodes is fine. For the Subject you can put pretty much anything you like because the presence of SAN DNS overrides the Subject CN. I would simply make Subject CN = portal.mycompany.com
When you create a CSR for a Portal, ISE wants you to choose a label/tag for this cert - so that later on, when you create your portal, you can select that tag in the Portal config. You can have many portals with different certificates - just give it a name like "BYOD Portal" or something that relates to the certificate's function.
I'm pretty sure that when you select both ISE nodes in the CSR creation process, the output will be a single CSR file that you give to the public CA to sign. If you should mess up the CSR part, it doesn't matter - you can delete it and try again. After submitting to the CA, you should get back a single certificate that contains both SAN entries. The cert will be identical on both nodes. I think ISE takes care to copy the cert to both nodes during the bind. I don't recall. it's been a while since I did a multi-node CSR. I tend to always make it for one node only. In the worst case, create it for one ISE node, and then export that cert with the private key, and import it into ISE node 2. But I don't think it will come to that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2023 09:17 AM
Thank you so much for taking the time to explain the entire process, will follow all instructions as we discussed. will let you know if need any further assistance.
Regards,
Kunal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2023 12:38 PM
Hello Aren Bier,
I am getting warning message when putting CN value as well as both SAN value that Certificate contains non resolvable Common Name / SAN Values 'portal.mycompany.com'. Please confirm still you want to proceed.
Should I proceed with that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2023 02:14 PM
Hi @kshah2589
Yeah - that would have been useful if there was no SAN entry. But since there is a SAN, you're good. Anyway, web browsers always check to see if a SAN entry is available. If not, then they compare the FQDN to the Subject CN.
I don't think ISE should have this check, because you can legitimately create a CSR for an FQDN that you are still in the process of creating - e.g. you might be forced to create the CSR before you had a chance to create the DNS entry.
ISE wants to be helpful - but IMHO it just causes unnecessary doubt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2023 02:37 PM
Thank you so much for explain. I will ignore the warning and go ahead to create CSR.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2023 06:19 AM
Hello Aren Bier,
While generating CSR for "Portal", I select both ISE node and insert SAN1 and SAN2, as a result ISE created 2 PEM file one for each node and each PEM file has both SAN values, does that look correct? because when we did same thing for "EAP Authentication" it generated only one PEM file which contains both SAN value.
Let me know your thoughts.
Regards,
Kunal Shah
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide