- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Extending CoA capabilities for 3rd party NADs during Central Web Auth
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extending CoA capabilities for 3rd party NADs during Central Web Auth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2020 05:51 AM
Hi all,
I wanted to ask, if ISE will utilize further CoA capabilites for 3rd party vendors, provided the network device profile is configured with those additional settings? Duplicating a profile opens up the configuration of other CoA messages.
I am specifically asking for the Reauth since on a Cisco WLC this is one of the things that prevents the client from undergoing a full SSID reconnect.
3rd party NADs when they support it are per default given the CoA Disconnect-Message during the CWA process, which causes a drop in the network connection. Question therefore is, if those additional message types would be utilized.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2020 08:19 PM
I have used custom Device Profiles in the past, but I didn't use any of the CoA stuff, because the NAS (HPE in this case) didn't support anything other than simple disconnect (as you stated). But I believe that ISE will support whatever you configure here.
What NAS vendor are you talking about that supports the more advanced CoA like Cisco? What does the NAS vendor claim to support (e.g. CoA Reauth)? - do you know what the format of the CoA needs to be?
The best way would be to clone the Cisco Device Profile, and then assign that to the NAS you're testing this with. But remember - if you assign a non-Cisco Device Profile to a NAS, then you MUST assign that same device profile to your Authorization Profile - or else ISE returns nothing.
And then create a session in ISE, and see whether ISE does something like CoA Reauth (or whatever the NAS vendor claims to support).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 03:02 AM - edited 11-30-2020 03:05 AM
Hi Arne,
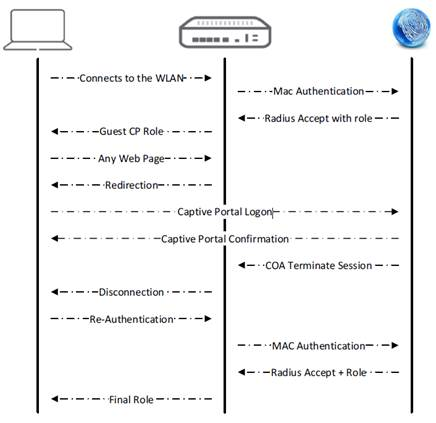
in this case it is an Aruba WLAN controller where I try to replicate Central Web Auth, but without using two distinct RADIUS requests.
In the first request ISE sends a role attribute to the NAD, which it then applies to the client session. This role contains the URL to the captive portal. Once the user authenticates to the captive portal, ISE sends the CoA DM and starts the session stitching timer.
When the client connects the second time the NAD will send another access-request. ISE sees there is a timer running for this client and sends back a role attribute, which gives the client full network access.
From a technical perspective unlike the Cisco WLC there is actually no need to trigger another authentication on the Aruba WLC. It only needs a new role pushed, which would then change the role locally on the WLC (effectively assigning a different Firewall profile that gives full access instead of pointing to a captive portal).
The idea is now avoid the CoA Disconnect, which gets sent once captive portal authentication was successful, because some clients do not handle that well. I know from Aruba's documentation that they support dynamic session management based on CoA, which involves Aruba's own NAC solution Clearpass. Based on how their WLAN controller works they only need to send the name of the new profile and the client session is allowed full access. This is what I am trying to replicate with ISE (if that is even possible).
I am still trying to find out the necessary AVPs that need to be sent to the NAD as well as what type of CoA message is needed on the ISE side in the device profile. I am in contact with Aruba on that one.
However once that is clarified another thing that I need to check is, how ISE is going to handle the session. If I should manage to get it working with only one request how will ISE behave, when no second auth-req is coming in? That might open another can of worms.
BR,
Patrick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2020 01:06 AM
Sounds tricky ... yes ISE Sessions are based mostly (if not entirely) on a session ID created by the NAS. And the NAS then has to send Accounting to keep the session alive - I don't know how all this is going to pan out. Weird scenario to have an Aruba wireless solution and ISE NAC. Perhaps someone has done this. Clearpass is quite different indeed.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide