- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: How to configure to process policy set by policy set at ISE 3.0
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2023 08:13 PM
Hello all,
Let me ask some helps regarding ISE multiple policy set, i'm trying to configure my policy sets to get segregate for each.
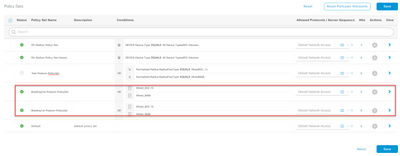
For example, we have two policy set as (Building1st-Posture-PolicySet and Building2nd-Posture-PolicySet)
For each policy set, i have authorization and authentication policies for multiple departments. As i expected is 'If user not found at Building2nd-Posture-PolicySet and it should not meeting with any authorization profile and it should go on to check user at Building1st-Posture-PolicySet and apply authorization profile accordingly but it does not work as expected and if user not found at Building2nd-Posture-PolicySet, it get reject with Default-Deny of Authorization policy of Building2nd-Posture-PolicySet and did not continue to process top-to-down until Building1st-Posture-PolicySet. So, all of users who are at Building1st-Posture-PolicySet get Deny.
How can i configure to process top-to-down policy set by policy set? Is there anyone experienced about that? Thanks.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2023 12:36 AM
@journey jane at present the conditions to match the Policy Sets are identical (Wired Dot1x and Wired MAB). You need to distinguish between them with an additional unique condition. You can group the NAD (switches) for each building in to a different Network Device Group (NDG) and use this in the policy set to distinguish between the different connection requests depending where they are coming from.
I personally would just combine those 2 Policy Sets into 1 and use the different conditions within the authorisation rules to achieve the same result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2023 08:43 AM
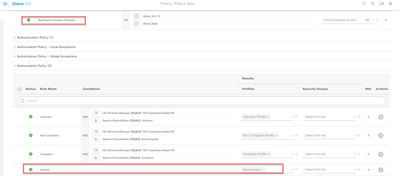
Hello @journey jane , the approach that I would take is to add an extra condition within the couple of policy sets that you have created in order to differentiate if the request is coming from building 1 or 2, the easiest way it would be if you create a device group and involves all the NAD that you have in building 1 and then use a condition like the one below ( notice that instead of SWITCH it would have to be the NAD group of building 1) ,
for further reference :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2023 12:36 AM
@journey jane at present the conditions to match the Policy Sets are identical (Wired Dot1x and Wired MAB). You need to distinguish between them with an additional unique condition. You can group the NAD (switches) for each building in to a different Network Device Group (NDG) and use this in the policy set to distinguish between the different connection requests depending where they are coming from.
I personally would just combine those 2 Policy Sets into 1 and use the different conditions within the authorisation rules to achieve the same result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2023 09:24 PM
Thanks @Rob Ingram for the input. When i modify condition by adding devices group. it works well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2023 08:43 AM
Hello @journey jane , the approach that I would take is to add an extra condition within the couple of policy sets that you have created in order to differentiate if the request is coming from building 1 or 2, the easiest way it would be if you create a device group and involves all the NAD that you have in building 1 and then use a condition like the one below ( notice that instead of SWITCH it would have to be the NAD group of building 1) ,
for further reference :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2023 09:25 PM
Thanks @Rodrigo Diaz for the input. When i modify condition by adding devices group as you mentioned. it works well.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide