- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.7 dot1x Failure Reason 12308
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2021 03:27 AM
HEY
i have a strange problem when implementing dot1x in my lab environment
my supplicant successfully authenticate against active directory but still ISE consider the authentication as a failure because the supplicant send resualt TLV message.
| Event | 5400 Authentication failed |
| Failure Reason | 12308 Client sent Result TLV indicating failure |
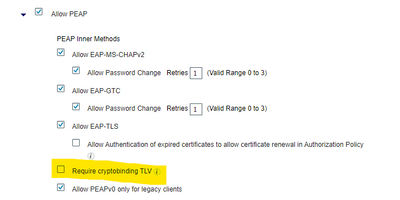
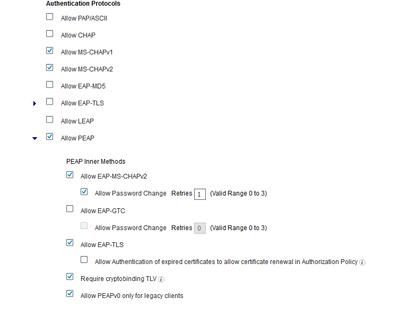
| Resolution | If ISE is configured to request Crypto-Binding TLV, ( i.e. "Require cryptobinding TLV??? is checked on the Allowed Protocols screen); and the client is not configured to use Crypto-Binding TLV then the client may react on this situation by sending "Result TLV" indicating failure. There will also be a communication failure if ISE is not configured to send Crypto-Binding TLV and the client is configured to use it. Both ISE and the client must be identically configured regarding using of Crypto-Binding TLV to result in successful communication.If failure still occurs - contact TAC. |
| Root cause | Internal error, possibly in the supplicant: PEAP v0 authentication failed because client sent Result TLV indicating failure. Client indicates that it does not support Crypto-Binding TLV |
i tried playing with the allowed protocols in my policy set
checked and unchecked - Require cryptobinding TLV
but still i no change appears
here is the steps in the report:
| 1001 | Received RADIUS Access-Request | |
| 11017 | RADIUS created a new session | |
| 15049 | Evaluating Policy Group | |
| 15008 | Evaluating Service Selection Policy | |
| 15048 | Queried PIP - Normalised Radius.RadiusFlowType | |
| 15048 | Queried PIP - Radius.Service-Type | |
| 11507 | Extracted EAP-Response/Identity | |
| 12300 | Prepared EAP-Request proposing PEAP with challenge | |
| 12625 | Valid EAP-Key-Name attribute received | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12302 | Extracted EAP-Response containing PEAP challenge-response and accepting PEAP as negotiated | |
| 12318 | Successfully negotiated PEAP version 0 | |
| 12800 | Extracted first TLS record; TLS handshake started | |
| 12805 | Extracted TLS ClientHello message | |
| 12806 | Prepared TLS ServerHello message | |
| 12807 | Prepared TLS Certificate message | |
| 12808 | Prepared TLS ServerKeyExchange message | |
| 12810 | Prepared TLS ServerDone message | |
| 12811 | Extracted TLS Certificate message containing client certificate | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 12318 | Successfully negotiated PEAP version 0 | |
| 12812 | Extracted TLS ClientKeyExchange message | |
| 12813 | Extracted TLS CertificateVerify message | |
| 12804 | Extracted TLS Finished message | |
| 12801 | Prepared TLS ChangeCipherSpec message | |
| 12802 | Prepared TLS Finished message | |
| 12816 | TLS handshake succeeded | |
| 12310 | PEAP full handshake finished successfully | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 12313 | PEAP inner method started | |
| 11521 | Prepared EAP-Request/Identity for inner EAP method | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 11522 | Extracted EAP-Response/Identity for inner EAP method | |
| 11806 | Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 11808 | Extracted EAP-Response containing EAP-MSCHAP challenge-response for inner method and accepting EAP-MSCHAP as negotiated | |
| 15041 | Evaluating Identity Policy | |
| 22072 | Selected identity source sequence - AD_Identity_store | |
| 15013 | Selected Identity Source - AD_INT | |
| 24430 | Authenticating user against Active Directory - AD_INT | |
| 24325 | Resolving identity - user10 | |
| 24313 | Search for matching accounts at join point - xxxx-domain | |
| 24319 | Single matching account found in forest - xxxx-domain | |
| 24323 | Identity resolution detected single matching account | |
| 24343 | RPC Logon request succeeded - user10@xxxx-domain | |
| 24355 | LDAP fetch succeeded - xxxx-domain | |
| 24458 | Not all Active Directory attributes are retrieved successfully - AD_INT | |
| 24100 | Some of the expected attributes are not found on the subject record. The default values, if configured, will be used for these attributes - AD_INT | |
| 24402 | User authentication against Active Directory succeeded - AD_INT | |
| 22037 | Authentication Passed | |
| 11824 | EAP-MSCHAP authentication attempt passed | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 11810 | Extracted EAP-Response for inner method containing MSCHAP challenge-response | |
| 11814 | Inner EAP-MSCHAP authentication succeeded | |
| 11519 | Prepared EAP-Success for inner EAP method | |
| 12314 | PEAP inner method finished successfully | |
| 12305 | Prepared EAP-Request with another PEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request ( Step latency=2086 ms) | |
| 11018 | RADIUS is re-using an existing session | |
| 12304 | Extracted EAP-Response containing PEAP challenge-response | |
| 12308 | Client sent Result TLV indicating failure | |
| 61025 | Open secure connection with TLS peer | |
| 12307 | PEAP authentication failed | |
| 11504 | Prepared EAP-Failure | |
| 11003 | Returned RADIUS Access-Reject |
is their any suggestions ?
thanks !
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2023 02:11 PM
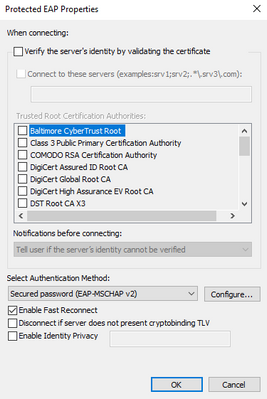
Uncheck this setting in Policy Elements > Results > Authentication > Allowed Protocols
Hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2021 03:41 AM
You need to tell us more about your environment - what is the end device? how it configured to authenticate?
post the complete logs from ISE when the user starts authenticating to the end process.
as per the message, this may be a bug :
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvu73387/?rfs=iqvred
Also have a look at this thread may help to resolve the issue :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2021 07:50 AM
hey BB first of all thanks for your respone
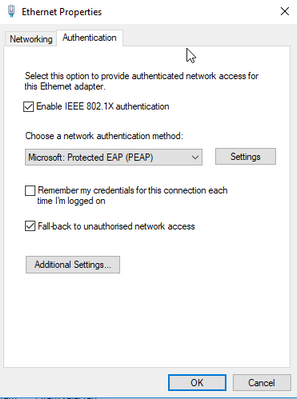
the authentications fails in first place because windows 10 sends the result TLV (maybe their is a way to disable it? PS - i didnt found one)
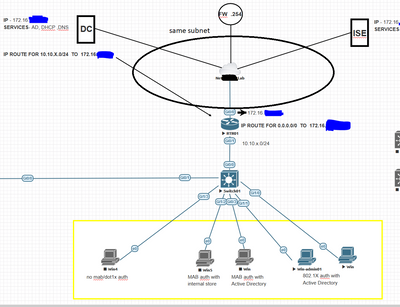
the device is a windows 10 host in EVE-NG VM.
the ISE sits on the same ESXI where the EVE-NG sits, also as a VM
i uploaded the windows host configuration and the topology
all computers are in the domain.
after doing some configuration changes their are still no updates...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2023 02:11 PM
Uncheck this setting in Policy Elements > Results > Authentication > Allowed Protocols
Hope that helps.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide