- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Logging MAC address of endpoints connecting over VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2017 07:47 AM
Dear Colleagues,
The customer would like to log the MAC addresses of the endpoints connecting over VPN into their SIEM.
As far as I know we can't do that. Seemingly we can't even send the MAC to ISE from ASA over the MDM-tlv attributes.
Is there any trick, e.g. getting the MAC address from Windows registry with the posture scan agent and log that out somehow, or custom DAP LUA script running on ASA?
Best regards,
Istvan
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 07:25 AM
Hostscan should not be required. Viktor is correct and not all OSes will expose the MAC address to an application.
I would debug the RADIUS at the ASA or could get packet capture after ASA to see the RADIUS attributes (or TCP dump at PSN). You will see the mdm-tlvs that are being sent. Most Windows clients expose the MAC address.
Support to send MDM TLV attributes over RADIUS via ACIDEX requires ASA 9.3.2+ and AC 4.1+.
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2017 10:45 AM
Istvan,
Not that I'm aware of and I don't think extracting the MAC using posture is going to work because of the possibility the endpoint has more than one NIC. I don't think what you are asking for is currently possible.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 07:30 AM
Hi Tim,
Thank you. Please follow my post that I am adding below. I re-tested in a dcloud LAB for some reasons the MAC is now there and seemingly it has been parsed from the ASA mdm-tlv attribute.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2017 03:35 PM
What version of ASA, Anyconnect and ISE are you using? Anyconnect on Windows and MAC send the client MAC address to ASA. Latest version of ASA (9.3+ I think) will send that information to ASA via ACIDEX. New versions of ISE (1.4+ I think, but may be later) will log that MAC address.
MAC address is not made available to Anyconnect client on iOS by Apple. To keep mobile clients consistent, Android version of Anyconnect also does not send the MAC address to the ASA. So for those mobile devices, you won't get the MAC address from Anyconnect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 07:39 AM
Hi Tim, Viktor,
I have opened the dCloud Rapid Threat Containment lab where I knew that we use ASAv and AnyConnect with ISE (actually 2.0).
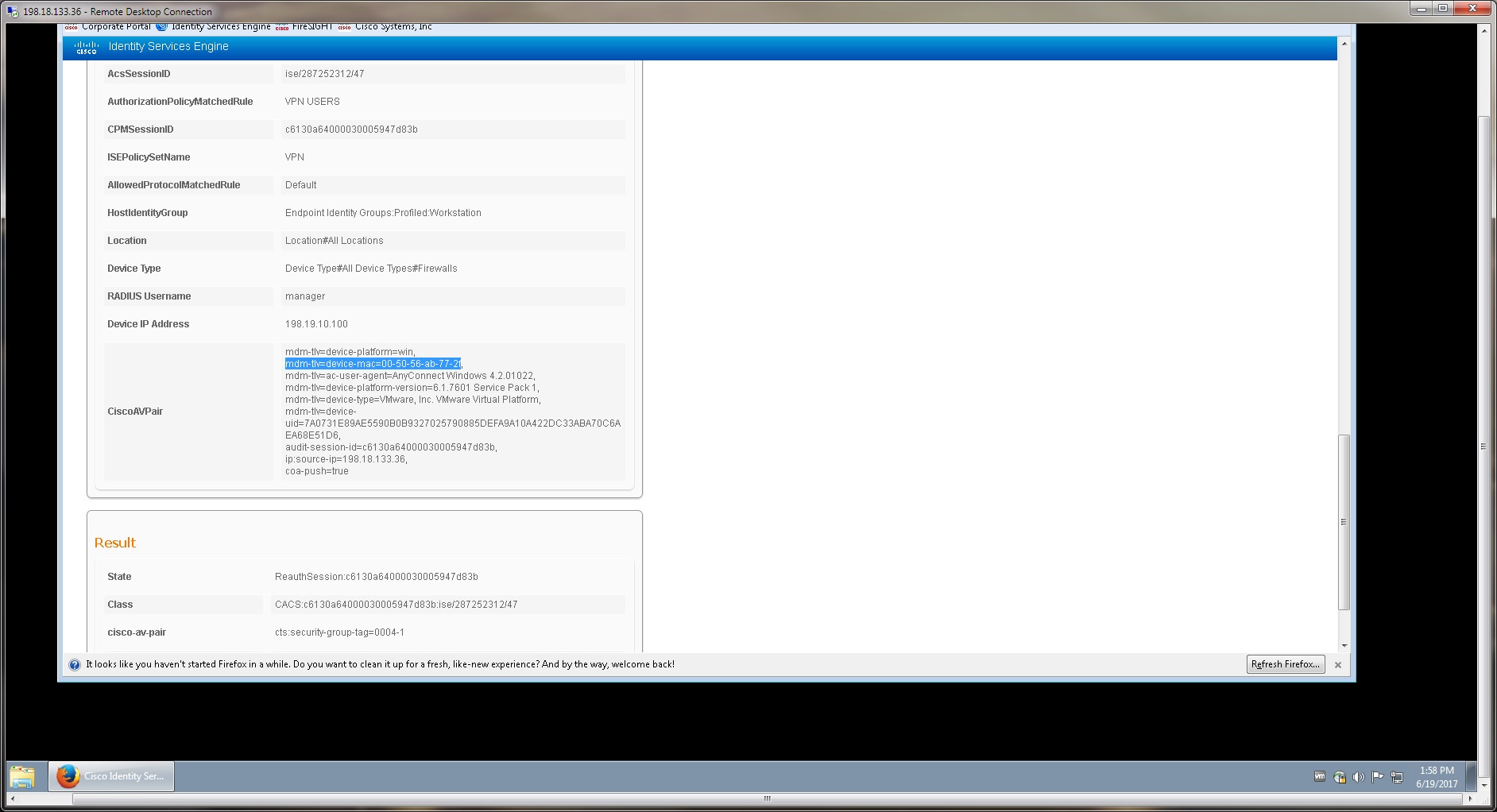
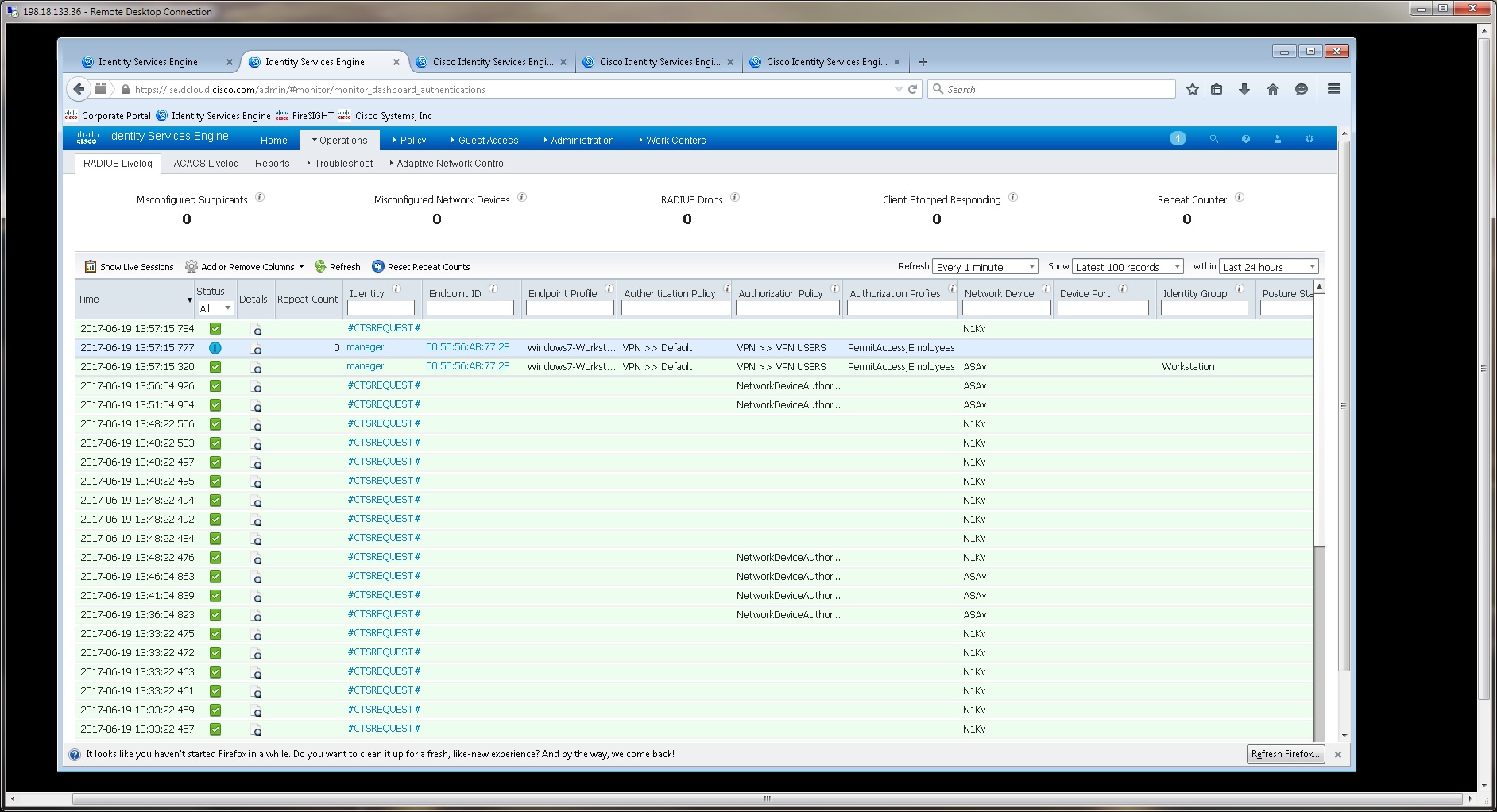
I used the same lab but a different pod before. That time no MAC address was presented in Livelog in ISE and the 'mdm-tlv=device-mac=...' string was not in the Cisco A/V pair in the authentication event details.
This last time the MAC address was presented without any change.
The questions are:
- How can this behavior controlled?
- Once it is there, can we send it to an upstream SIEM over syslog?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 07:53 AM
The test I did in my lab didn't send the MAC address either but I was using a different version of anyconnect. I was using the latest version of AnyConnect for IOS so I'm wondering if it is version / platform specific. I'll ask one of my AC colleagues to chime in. If the MAC address shows up in the live log / session directory, ISE can forward that information over syslog.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 08:44 AM
Thank you in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 06:08 PM
Hi Istvan,
I mentioned about this in my previous post. Apple blocks any Apps from accessing the MAC address, so you will never get a MAC address from Anyconnect on iOS. You will find the same for Android. Although, on Android, Anyconnect can get the MAC, the BU disabled it to keep all mobile clients consistent.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2017 11:56 PM
Hi Viktor,
At the moment the focus is Windows. And it seems - Tim's anyconnect friend hasn't confirmed yet - sending MAC address is not consistent across AnyConnect for Windows versions.
Hopefully Time can come up with a response from his fellow engineer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 05:53 AM
Do you have Hostscan enabled on the PC that's not reporting the MAC address? That may be required for Anyconnect to grab the MAC address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 06:09 AM
Hi Viktor,
This document says that HostScan is not required: http://www.cisco.com/c/en/us/support/docs/security/anyconnect-secure-mobility-client/118944-technote-anyconnect-00.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 07:12 AM
On the firewall, enable debug dap trace and see what attributes you're seeing there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 07:25 AM
Hostscan should not be required. Viktor is correct and not all OSes will expose the MAC address to an application.
I would debug the RADIUS at the ASA or could get packet capture after ASA to see the RADIUS attributes (or TCP dump at PSN). You will see the mdm-tlvs that are being sent. Most Windows clients expose the MAC address.
Support to send MDM TLV attributes over RADIUS via ACIDEX requires ASA 9.3.2+ and AC 4.1+.
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 07:45 AM
Hi Craig,
Thank you for Jumping in.
So can we say that with ASA 9.3.2 and AC 4.1 or later this is expected to work, if not there is something to troubleshoot?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2017 08:06 AM
Please run debug dap trace on the ASA to see what attributes anyconnect is reporting to the ASA. And as chyps mentioned, debug radius
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide