- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: SSM ON-Prem TACACS+ and Clearpass
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSM ON-Prem TACACS+ and Clearpass
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 01:51 AM
Hi,
I am trying to configure TACACS+ on our SSM On-Prem server so that I am able to login on the Webinterface with my AD user. The TACACS+ configuration is done in Clearpass. And the test in the configuration window on the SSM server was successful.
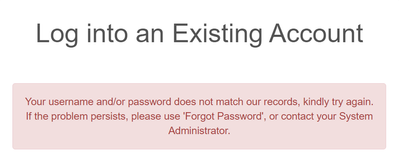
But as soon as I try to login with my user on the login window it is not working:
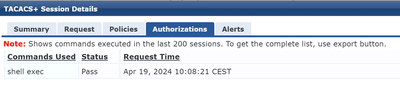
In Clearpass everything looks fine and I am not sure how I could debug that issue on the SSM side.
This is how my config in Clearpass looks:
Is anybody using Clearpass for TACACS+ and SSM?
Thank you!
Cheers,
Marius
- Labels:
-
Other NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 10:38 AM
What are you trying to do? Cisco SSM? As Smart Software Manager? Does SSM use TACACS+ priv levels?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 06:20 AM
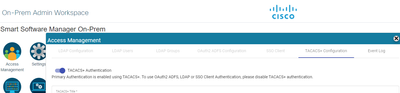
Yes, Cisco Smart Software Manager. At least it offers TACACS+ Auth in the settings:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 07:39 AM
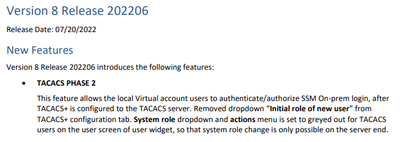
Just saw this message in the release notes:
So I guess I need to configure Clearpass to send back the correct user role. But I don't know which exact role I need to send and which service to use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2024 06:50 AM
The three system role types are: System User • System Operator • System Administrator. Is this for CLI or GUI access to SSM? It looks to me from the configuration guide that the GUI uses system roles while the CLI uses Privilege levels. But it doesn't specify what those attributes should be.
As far as the Service, that's up to the ClearPass configuration and where you would like that service to live.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2024 10:59 PM
That's the problem I have. I don't know which attributes are needed for the GUI. I am still going through the logs on SSM side but there is not a lot of info in it. Like you said, the configuration guide doesn't specify anything unfortunately.
Apr 25 05:22:09 uzuh41 a17c57646a7b: (tacacs) Setup endpoint detected, running now.
Apr 25 05:22:09 uzuh41 a17c57646a7b: (tacacs) Request phase initiated.
Apr 25 05:22:10 uzuh41 a17c57646a7b: (tacacs) Authentication failure! unauthorized encountered.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 06:12 AM
I use secure ldap for on-prem SSM access with no issues - the bug below states:
"It appears that there is no possibility of using TACACS attributes to fully automate User/Operator/Admin access."
hth
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2024 11:37 PM - edited 05-02-2024 11:40 PM
I think I found out what the issue and bug is and also how to fix it.
So the whole SSM on-prem is running multiple docker containers and one of them is called "tacacs-client". In this container you will find the following file which checks for the privilege level that is sent back from the TACACS+ server. The "arg.match" is looking for 'priv-lvl'.
/usr/local/bundle/bundler/gems/ochimus-d67b47ff0569/lib/ochimus/tacacs_packet/authorization/tacacs_reply_body.rb
# Authorization arguments from Tacacs+ server are AV pairs seperated by equal sign
# i.e. priv-lvl=10
def self.priv_lvl_extractor(args_length, raw_data)
priv_lvl = 0 #unauthorized initially
args_length.each do |arg_length|
arg = raw_data.read(arg_length)
File.open("/usr/src/authorize.log", "a") {|f| f.write("Privilege level raw data: #{arg}\n") }
if arg.match('priv-lvl')
priv_lvl = Integer(arg.partition('=').last)
end
end
priv_lvl
end
Now the issue is that SSM is not requesting 'priv-lvl' from the TACAS+ server but 'priv_lvl'! This is from the Clearpass log. Check out the very last argument "ArgList" here:
2024-05-03 07:59:52,431 [AAAModuleThread-0x7f79b099b700 h=996] DEBUG AAA.AuthorSession - handleAuthorRequest: TacacsAuthorRequest={{version=192, type=2, flags=0, seqNum=1, sessionId=465481928, length=47}{authenMethod=6, privLvl=0, authenType=3, authenMethod=6, service=3, userLen=6, portLen=2, remAddrLen=14, argCnt=1}(User=xxxxxxx, Port=49, RemAddr=ochimus_device, ArgList=service=priv_lvl)}
So now there are three things that can be done to fix it. Only one option is needed. #3 is the easiest one.
1. Fix the request on SSM that is sent to the TACAS+ server to request 'priv-lvl' instead of 'priv_lvl'
2. Fix the tacacs_reply_body.rb file so it accepts 'priv_lvl' additionally:
# Authorization arguments from Tacacs+ server are AV pairs seperated by equal sign
# i.e. priv-lvl=10
def self.priv_lvl_extractor(args_length, raw_data)
priv_lvl = 0 #unauthorized initially
args_length.each do |arg_length|
arg = raw_data.read(arg_length)
File.open("/usr/src/authorize.log", "a") {|f| f.write("Privilege level raw data: #{arg}\n") }
if arg.match('priv-lvl') || arg.match('priv_lvl')
priv_lvl = Integer(arg.partition('=').last)
end
end
priv_lvl
end
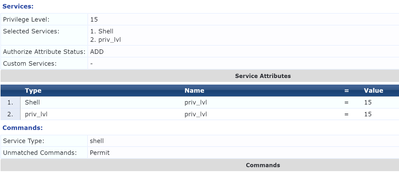
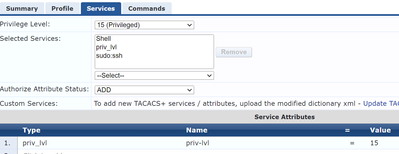
3. Create the service 'priv_lvl" with type 'priv_lvl' and send back 'priv-lvl' from the TACACS+ server. I tested it and it works. My Clearpass setup looks like this now for the profile:
This is how the Service Dictonary for Clearpass should look like:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<TipsContents xmlns="http://www.avendasys.com/tipsapiDefs/1.0">
<TipsHeader exportTime="Thu May 02 13:44:05 CEST 2024" version="6.11"/>
<TacacsServiceDictionaries>
<TacacsServiceDictionary dispName="priv_lvl" name="priv_lvl">
<ServiceAttribute allowedValuesCsv="0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15" dataType="Unsigned32" dispName="Privilege level" name="priv-lvl"/>
</TacacsServiceDictionary>
</TacacsServiceDictionaries>
</TipsContents>
Hopefully someone can use this info to use Clearpass as well in future as the TACACS server for SSM.
Best,
Marius
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide