- Cisco Community
- Technology and Support
- Networking
- Network Management
- ssh into a switch - no matching key exchange method found
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ssh into a switch - no matching key exchange method found
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 07:40 AM
Hello all,
I have inherited an infrastructure with several catalyst 9200 switches. A few of them are unreachable when using ssh from a terminal, such as a linux server or Powershell. The error message is this:
Unable to negotiate with <IP ADDRESS> port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
this is needed beacuse I have a linux server that needs to log into the switches automatically for backup; however, all of them are reachable using SSH from PUTTY, so it's not like ssh protocol isn't up.
This issue is not related to the login used, with the same login credentials I log into every switch using PUTTY, but only some using ssh from linux/powershell.
can you please suggest which parts of the config can I look at to troubleshoot this? I can see that the line vty are all configured the same way and the
ip ssh version 2
line is in every config
thanks in advance
F.
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 07:59 AM
but only some using ssh from linux/powershell.
what Linux ditro you using, you can update your ciphers - follow below guide :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 08:04 AM
The server offers "diffie-hellman-group-exchange-sha1" and "diffie-hellman-group14-sha1". These are older algorithms, possibly disabled by default on your SSH client due to security concerns (Mac did this a few years back). Use ssh -vV <IP_ADDRESS> to see detailed debug output, including supported algorithms by both client and server.
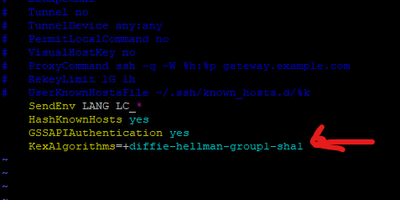
This is a temporary workaround and weakens security. Edit your SSH client configuration to allow the specific algorithms offered by the switch. Add KexAlgorithms=diffie-hellman-group1-sha1 to your SSH configuration.
Hope this helps.
Connect with me https://bigevilbeard.github.io
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 08:14 AM
I seem to already have this line in my ssh_config file, yet it doesn't work.
As I have two Catalyst 9200 switches (call them SW1 and SW2), the exact same model, SW1 is refusing the connection while SW2 is accepting it... is there any command to modify the ssh config of SW1 rather than the server's?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 08:49 AM
Use command show ip ssh all on SW1. This will display the current SSH server configuration, including the supported key exchange methods. You can then enable those on SW2.
Hope this helps.
Connect with me https://bigevilbeard.github.io
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 07:14 AM
I can see there's differences... can I ask you all if there are commands to enable the missing algorithms and everything else? Are there any security issues in doing so?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 08:55 AM - edited 04-19-2024 08:56 AM
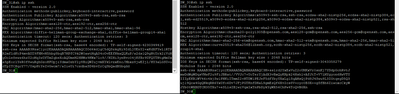
IOS XE do the below you see the ciphers :
#show ip ssh
SSH Enabled - version 2.0
Authentication methods:publickey,keyboard-interactive,password
Authentication Publickey Algorithms:x509v3-ssh-rsa,ssh-rsa,ecdsa-sha2-nistp256,e cdsa-sha2-nistp384,ecdsa-sha2-nistp521,x509v3-ecdsa-sha2-nistp256,x509v3-ecdsa-s ha2-nistp384,x509v3-ecdsa-sha2-nistp521,rsa-sha2-256,rsa-sha2-512
Hostkey Algorithms:x509v3-ssh-rsa,rsa-sha2-512,rsa-sha2-256,ssh-rsa
Encryption Algorithms:aes128-gcm,aes256-gcm,aes128-ctr,aes192-ctr,aes256-ctr
MAC Algorithms:hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac- sha2-256,hmac-sha2-512,hmac-sha1
KEX Algorithms:ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-h ellman-group14-sha1
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 2048 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded): TP-self-signed-244449417
ssh-rsa xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 10:19 AM
Hello,
it might just be easier, and save time, to reset the switch to factory defaults. Here is the procedure:
If you do not have access to the CLI of a Cisco Catalyst 9200 switch and need to reset it to factory defaults, you can perform a hardware reset using the mode button on the front panel of the switch. Here's how you can do it:
1. **Power Off the Switch**: Make sure the switch is powered off completely.
2. **Locate the Mode Button**: On the front panel of the switch, locate the Mode button. It is typically recessed and may require a small tool like a paperclip to press.
3. **Press and Hold the Mode Button**: Press and hold down the Mode button.
4. **Power On the Switch**: While continuing to hold down the Mode button, power on the switch.
5. **Wait for LED Indications**: Continue holding down the Mode button until the LED indicators on the front panel start flashing sequentially.
6. **Release the Mode Button**: Once the LED indicators start flashing, release the Mode button.
7. **Wait for Reset**: The switch will now reset to factory defaults. This process may take a few minutes.
8. **Verify Factory Defaults**: Once the reset process is complete, you can verify that the switch has been reset to factory defaults by observing its behavior when it boots up. You should see the switch go through its initial setup process as if it were brand new.
This hardware reset procedure should restore the switch to its factory default configuration, removing all existing configuration settings. Keep in mind that performing a hardware reset will also erase any configuration files stored on the switch, including the startup configuration file.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide