- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: access rules firepower 1010
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
access rules firepower 1010
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2023 06:01 PM
Hi team,
have a question regarding access rules.
how come if any any eveyrhting works fine.
however when i want to allow lets say connect to facebook, and everything else disable
so i put source(inside) network(any-ipv4) ports(any) destination(outside_zone) network(FQDN facebook.com) ports (any)
so now I should have connection only to facebook, however no connection at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2023 02:27 AM
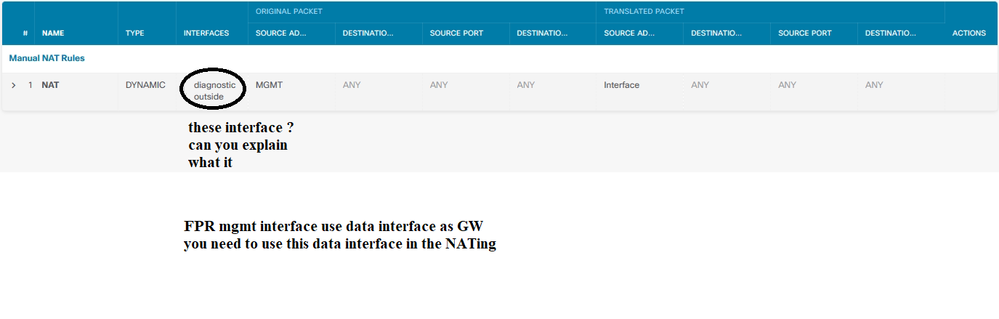
Yes below note to add new NATing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2023 02:57 AM
can you go into expert mode (tye expert at the > prompt), become root user (sudo su -) and then do an nslookup for facebook.com (nslookup facebook.com) and see what result you get.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2023 03:09 AM
You will most likely find that an FQDN object for such a large scale web service will not work for your use-case. That's not the intended use.
If you configure an FQDN Object such as facebook.com, the FTD device will do a DNS lookup for facebook.com and put that IP address into the Access Control entry, it will repeat that based on the TTL of the DNS query.
Meanwhile your device behind the firewall is going to do it's own DNS lookup for facebook.com and connect to the IP address.
Due to the nature of how DNS operates, there is no way to guarantee that the lookup from the firewall and the lookup from the client will always resolve the same IP address. Similarly the client may also navigate to web.facebook.com or www.facebook.com which may resolve to different IP addresses than just facebook.com.
In reality you'd be better served using the Application Visibility and Control capabilities or a URL rule depending on the requirement. In the latter case, you may also want to check out the TLS Server Identity Discover feature.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2023 05:17 PM - edited 07-14-2023 05:44 PM
facebook was just an example.
I have tried example.com same result
However you are right about using Application option.
I tried google as an application and it worked.
Might have to use the URL option to allow specific websites
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2023 04:19 AM
Like the last comments summarize:
the ACL should be on Application, not on FQDN.
generally you FTD should lookup DNS either internally via an internal DNS Server and then the interface you specify is the specific internal interface where the DNS server resides.
OR the Firewall does DNS-lookups to the internet directly, like 8.8.8.8 or 208.67.222.222, then you specify your Outside-Interface as source
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide