- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ACL Denies With Permit Statements
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 10:16 AM
I am working on creating ACL to lock down our VLANs. I am running into some issue though. These are outbound ACL's
Here is my ACL
ip access-list extended veneer-75
remark permit KaceSMA agent access
permit tcp host 192.168.210.70 10.2.75.0 0.0.0.255 eq 443
remark permit RDP and remote assistance
permit tcp host 192.168.244.20 10.2.75.0 0.0.0.255 eq 3389
permit tcp host 192.168.244.25 10.2.75.0 0.0.0.255 eq 3389
permit tcp host 192.168.244.30 10.2.75.0 0.0.0.255 eq 3389
remark permit PSEXEC access
permit tcp host 192.168.244.20 10.2.75.0 0.0.0.255 eq 445
permit tcp host 192.168.244.25 10.2.75.0 0.0.0.255 eq 445
permit tcp host 192.168.244.30 10.2.75.0 0.0.0.255 eq 445
remark permit remote assistance
permit tcp host 192.168.244.20 10.2.75.0 0.0.0.255 eq 135
permit tcp host 192.168.244.25 10.2.75.0 0.0.0.255 eq 135
permit tcp host 192.168.244.30 10.2.75.0 0.0.0.255 eq 135
remark permit CBAC
permit tcp host 192.168.210.40 10.2.75.0 0.0.0.255 eq 41002
remark permit DNS
permit udp host 192.168.210.11 10.2.75.0 0.0.0.255 eq 53
permit udp host 192.168.210.16 10.2.75.0 0.0.0.255 eq 53
permit udp host 192.168.210.21 10.2.75.0 0.0.0.255 eq 53
permit udp host 192.168.210.22 10.2.75.0 0.0.0.255 eq 53
deny ip any any log
I am getting the following in the logs
%SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 192.168.210.70(443) -> 10.2.75.125(59252), 1 packet
Jul 11 10:15:50 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied udp 192.168.210.11(53) -> 10.2.75.125(58313), 1 packet
Jul 11 10:15:51 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied udp 192.168.210.21(53) -> 10.2.75.125(58313), 1 packet
Jul 11 10:15:53 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied udp 192.168.210.22(53) -> 10.2.75.125(58313), 1 packet
Jul 11 10:15:59 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied udp 192.168.210.11(53) -> 10.2.75.125(50199), 1 packet
Jul 11 10:16:00 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied udp 192.168.210.21(53) -> 10.2.75.125(50199), 1 packet
not sure why they are getting denied even with permit statements
Solved! Go to Solution.
- Labels:
-
Other Network Security Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 10:42 AM
permit udp host 192.168.210.11 10.2.75.0 0.0.0.255 eq 53
Jul 11 10:15:50 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied udp 192.168.210.11(53) -> 10.2.75.125(58313), 1 packet
from config of ACL 10.2.57.x is DNS server since you config eq 53 after it
but the deny LOG show different 192.168.210.11 is DNS server
so you need to correct acl
permit udp host 192.168.210.11 eq 53 10.2.75.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 10:25 AM
Share
Show ip access list
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 10:27 AM
Extended IP access list veneer-75
10 permit tcp host 192.168.210.70 10.2.75.0 0.0.0.255 eq 443
20 permit tcp host 192.168.244.20 10.2.75.0 0.0.0.255 eq 3389
30 permit tcp host 192.168.244.25 10.2.75.0 0.0.0.255 eq 3389
40 permit tcp host 192.168.244.30 10.2.75.0 0.0.0.255 eq 3389
50 permit tcp host 192.168.244.20 10.2.75.0 0.0.0.255 eq 445
60 permit tcp host 192.168.244.25 10.2.75.0 0.0.0.255 eq 445
70 permit tcp host 192.168.244.30 10.2.75.0 0.0.0.255 eq 445
80 permit tcp host 192.168.244.20 10.2.75.0 0.0.0.255 eq msrpc
90 permit tcp host 192.168.244.25 10.2.75.0 0.0.0.255 eq msrpc
100 permit tcp host 192.168.244.30 10.2.75.0 0.0.0.255 eq msrpc
110 permit tcp host 192.168.210.40 10.2.75.0 0.0.0.255 eq 41002
120 permit udp host 192.168.210.11 10.2.75.0 0.0.0.255 eq domain
130 permit udp host 192.168.210.16 10.2.75.0 0.0.0.255 eq domain
140 permit udp host 192.168.210.21 10.2.75.0 0.0.0.255 eq domain
150 permit udp host 192.168.210.22 10.2.75.0 0.0.0.255 eq domain
160 deny ip any any log (1563 matches)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 10:31 AM
160 deny ip any any log (1563 matches)
Only this have hit count.
So
Can I see config of vlan interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 10:31 AM
interface Vlan75
ip address 10.2.75.1 255.255.255.0
ip helper-address 192.168.210.21
ip helper-address 192.168.210.22
no ip redirects
ip access-group veneer-75 out
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 10:42 AM
permit udp host 192.168.210.11 10.2.75.0 0.0.0.255 eq 53
Jul 11 10:15:50 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied udp 192.168.210.11(53) -> 10.2.75.125(58313), 1 packet
from config of ACL 10.2.57.x is DNS server since you config eq 53 after it
but the deny LOG show different 192.168.210.11 is DNS server
so you need to correct acl
permit udp host 192.168.210.11 eq 53 10.2.75.0 0.0.0.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 01:21 PM
I am just full of ACL questions today, but I am hoping you got time for one more.
After implementing the ACL that we discussed here in this thread I began to get a lot of denies for inbound traffic from the internet.
Figured this was all return traffic that was getting blocked. I first applied the ACL
ip access-list extended veneer-75-in
remark this is to allow all established TCP connections
permit tcp any any established
permit udp any any
deny ip any any log
This was inbound.
I was still getting a bunch of denies
Jul 11 13:14:28 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56557) -> 40.97.205.2(443), 1 packet
Jul 11 13:14:29 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56541) -> 52.96.113.178(443), 1 packet
Jul 11 13:14:31 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56561) -> 3.223.18.180(443), 1 packet
Jul 11 13:14:32 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56563) -> 54.224.98.140(443), 1 packet
Jul 11 13:14:34 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56567) -> 3.217.227.12(443), 1 packet
Jul 11 13:14:35 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56572) -> 52.96.113.194(443), 1 packet
Jul 11 13:14:37 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56547) -> 52.96.113.178(443), 1 packet
Jul 11 13:14:38 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56575) -> 20.190.151.132(443), 1 packet
Jul 11 13:14:41 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56577) -> 3.224.142.88(443), 1 packet
Jul 11 13:14:42 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56579) -> 18.213.48.233(443), 1 packet
Jul 11 13:14:43 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56582) -> 3.211.34.234(443), 1 packet
Jul 11 13:14:45 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56559) -> 52.96.113.178(443), 1 packet
Jul 11 13:14:47 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56562) -> 52.96.113.210(443), 1 packet
Jul 11 13:14:49 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56591) -> 34.197.58.77(54443), 1 packet
Jul 11 13:14:51 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56592) -> 52.96.113.194(443), 1 packet
Jul 11 13:14:52 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56594) -> 54.224.98.140(54443), 1 packet
Jul 11 13:14:54 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56601) -> 3.217.227.12(54443), 1 packet
Jul 11 13:14:56 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56606) -> 52.96.119.98(443), 1 packet
Jul 11 13:14:58 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56583) -> 52.96.113.194(443), 1 packet
Jul 11 13:14:59 PDT: %SEC-6-IPACCESSLOGP: list veneer-75-in denied tcp 10.2.75.125(56610) -> 20.190.151.6(443), 1 packet
I then decied to add in permit tcp any any for anything that wasn't already established but then I started to get these denies on the outbound ACL
Jul 11 13:16:28 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 34.225.96.213(443) -> 10.2.75.125(56680), 1 packet
Jul 11 13:16:29 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 52.0.42.182(443) -> 10.2.75.125(56685), 1 packet
Jul 11 13:16:30 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 52.96.113.130(443) -> 10.2.75.125(56687), 1 packet
Jul 11 13:16:32 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 34.227.6.160(443) -> 10.2.75.125(56690), 1 packet
Jul 11 13:16:33 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 20.190.151.69(443) -> 10.2.75.125(56700), 1 packet
Jul 11 13:16:34 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 174.129.10.62(54443) -> 10.2.75.125(56695), 1 packet
Jul 11 13:16:35 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 34.202.153.67(443) -> 10.2.75.125(56688), 1 packet
Jul 11 13:16:36 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 52.96.113.130(443) -> 10.2.75.125(56709), 1 packet
Jul 11 13:16:38 PDT: %SEC-6-IPACCESSLOGP: list veneer-75 denied tcp 52.0.42.182(443) -> 10.2.75.125(56685), 1 packet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 01:44 PM
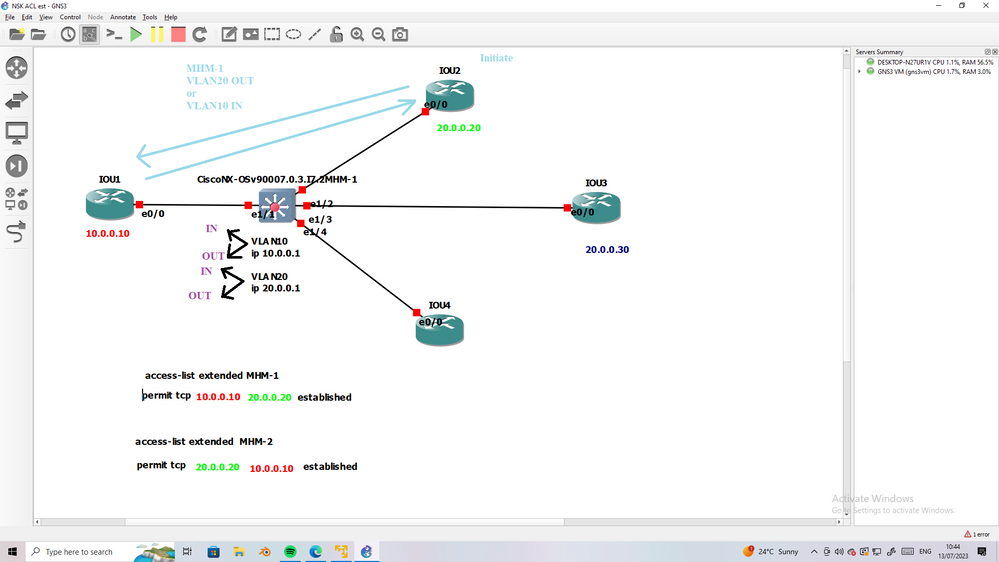
dont worry I will share lab explain TCP with SVI VLAN ACL with establish.
wait me two-three hours
thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 01:45 PM
perfect thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2023 06:48 AM
Thank you again for your help I was able to fix the next issue. The problem was that the ACL was blocking return internet traffic. I added the following line to the ACL
permit tcp any any established
That fixed the return traffic getting blocked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2023 11:48 AM - edited 07-11-2023 12:58 PM
The access list syntax would be:
< action > < protocol > < source IP > < source port > < destination IP > < destination port >
So, if you apply an entry like this:
permit udp host 192.168.210.11 10.2.75.0 0.0.0.255 eq domain
It will match the traffic sourcing from the host 192.168.210.11 from any port going to the destination IP 10.2.75.0/24 to the destination port 53 in UDP, this is why it was not matching the return traffic from the DNS server, because the DNS server would have responded to that traffic with the source port 53/udp. So in that case the port 53 is the source port in the traffic flow, and the destination port of the clients can be any from the range above port 1023.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2023 12:51 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide