- Cisco Community
- Technology and Support
- Security
- Network Security
- Adding Backup ISP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adding Backup ISP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 03:30 PM
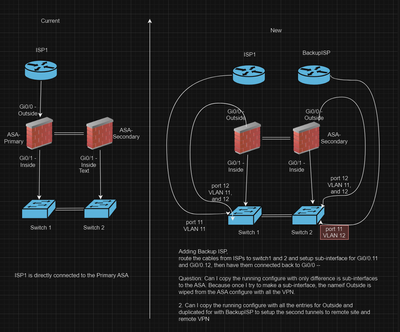
I have a pair of ASAs that I try to add a backup ISP. I would be creating sub interfaces on Gi0/0. Once I default the Gi0/0, the Outside configuration would be gone from the configure, can I do the sub interfaces. configure Gi0/0.10 with nameif Outside and paste all the configuration back to the ASA, would that restore all the configuration for the VPN and the site to site tunnel?
2. with the second sub-interface Gi0/0.20 nameif BackupISP, can I copy all the configure with NAT and crypto and change it from Outside to BackupISP to add it to the configuration to create the backup VPN tunnel for remote VPN and site to site?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 03:50 PM
I have a pair of ASAs that I try to add a backup ISP. I would be creating sub interfaces on Gi0/0. Once I default the Gi0/0, the Outside configuration would be gone from the configure, can I do the sub interfaces. configure Gi0/0.10 with nameif Outside and paste all the configuration back to the ASA, would that restore all the configuration for the VPN and the site to site tunnel?
2. with the second sub-interface Gi0/0.20 nameif BackupISP, can I copy all the configure with NAT and crypto and change it from Outside to BackupISP to add it to the configuration to create the backup VPN tunnel for remote VPN and site to site?
What I understand you will change the main interface G0/0 nameif OUTside to be G0/0.10 nameif OUTside same IP?
If Yes then let me check this in lab see the effect of change the interface with nameif
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 06:01 PM - edited 04-22-2024 02:57 AM
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2024 07:35 PM
Hi MHM, thanks for the response. When I try to default the interface it wipes out the configure. I try to prevent reconfigure everything that is why I use the same name Outside with the same IP. Can I upload a changed running configure for the Gi0/0.1 and test the running configure? Currently the first ISP is going directly to the ASA1, try to make it redundant with second ISP for failover to ASA2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2024 04:22 AM - edited 04-22-2024 02:58 AM
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2024 04:40 AM - edited 04-20-2024 04:41 AM
How is your network diagram looks like ?
is the ISP terminating Switch ?
ASA Gi0/0 outside interface connected to Switch ?
Do you have any sample configuration to look, and what ASA version code running on ASA ?
I have a pair of ASAs that I try to add a backup ISP. - If you have Pair of ASA you can terminate other ISP connection directly ASA 2 right ? what is the challenge here ? (when ASA 1 Fails - Other ASA 2 can take care of statefull switch over of the configured correctly ?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 02:23 PM
When you default the Gi0/0 interface all configuration that references the Outside name will be removed. So this will include, but not limited to, routing, NAT, access-group configuration, Site to site VPN configuration that references the interface name, remote access VPN configuration that references the interface name.
So when you do this, I recommend that you have a full configuration backup, extract all configuration that references the Outside interface name and then add it back once you have created the subinterface.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 05:25 PM
This is what I'm thinking.
I should be able to do replace the configure with running-configure to restore the configure once the sub-interface is added or do I need to do it with running-configure all?
Can I take the running configure with Outside and change it to BackupISP and paste it back to the running configure to setup the second backup tunnel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 05:42 PM
Here is a sample of the configure.
---
From
interface GigabitEthernet0/0
nameif Outside
security-level 0
ip address 85.15.23.242 255.255.255.248 standby 85.15.23.243
!
-----
Change it to
interface GigabitEthernet0/0
no nameif Outside
no security-level
no ip address
interface GigabitEthernet0/0.11
nameif Outside
Vlan 11
security-level 0
ip address 85.15.23.242 255.255.255.248 standby 85.15.23.243
interface GigabitEthernet0/0.12
nameif Outside
Vlan 12
security-level 0
ip address 95.16.24.242 255.255.255.248 standby 95.15.24.243
---
From
access-list Outside_1_cryptomap extended permit ip object-group DM_INLINE_NETWORK_8 172.16.176.0 255.255.255.0
access-list Outside_1_cryptomap extended permit ip 192.168.0.0 255.255.255.0 172.16.177.0 255.255.255.0
access-list Outside_1_cryptomap extended permit ip 192.168.0.0 255.255.255.0 172.16.180.0 255.255.255.0
access-list Outside_1_cryptomap extended permit ip 192.168.1.0 255.255.255.0 172.16.176.0 255.255.255.0
nat (Outside,Outside) source static 172.16.180.0 172.16.180.0 destination static 10.10.20.0 10.10.20.0 no-proxy-arp route-lookup
nat (Outside,Outside) source static 172.16.181.0 172.16.181.0 destination static 10.10.20.0 10.10.20.0 no-proxy-arp route-lookup
nat (Outside,Outside) source static 172.16.16.0 172.16.16.0 destination static 10.10.20.0 10.10.20.0 no-proxy-arp route-lookup
nat (Inside,Outside) source static any any destination static NETWORK_OBJ_10.10.20.0_23 NETWORK_OBJ_10.10.20.0_23 no-proxy-arp route-lookup
nat (DMZ,Outside) source static any any destination static NETWORK_OBJ_10.10.20.0_23 NETWORK_OBJ_10.10.20.0_23 no-proxy-arp route-lookup
-----
Change to
access-list BackupISP_1_cryptomap extended permit ip object-group DM_INLINE_NETWORK_8 172.16.176.0 255.255.255.0
access-list BackupISP_1_cryptomap extended permit ip 192.168.0.0 255.255.255.0 172.16.177.0 255.255.255.0
access-list BackupISP_1_cryptomap extended permit ip 192.168.0.0 255.255.255.0 172.16.180.0 255.255.255.0
access-list BackupISP_1_cryptomap extended permit ip 192.168.1.0 255.255.255.0 172.16.176.0 255.255.255.0
nat (BackupISP,BackupISP) source static 172.16.180.0 172.16.180.0 destination static 10.10.20.0 10.10.20.0 no-proxy-arp route-lookup
nat (BackupISP,BackupISP) source static 172.16.181.0 172.16.181.0 destination static 10.10.20.0 10.10.20.0 no-proxy-arp route-lookup
nat (BackupISP,BackupISP) source static 172.16.16.0 172.16.16.0 destination static 10.10.20.0 10.10.20.0 no-proxy-arp route-lookup
nat (Inside,BackupISP) source static any any destination static NETWORK_OBJ_10.10.20.0_23 NETWORK_OBJ_10.10.20.0_23 no-proxy-arp route-lookup
nat (DMZ,BackupISP) source static any any destination static NETWORK_OBJ_10.10.20.0_23 NETWORK_OBJ_10.10.20.0_23 no-proxy-arp route-lookup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 10:33 PM
This will not work. You will need a different name for the the BackupISP interface and then duplicate all configuration from the Outside interface for the backup interface. You would need to set the default route for the secondary ISP with a higher admin distance and then configure ipsla to track the outside interface and when it stops responding move to the BackupISP default route.
From what you have posted you only have. not NAT configuration for site to site VPN and do not have any public IPs exposed to the internet (i.e. webservers). But if you do have static one to one NAT for access from the Outside, in the case of a failover to the BackupISP you would need to manually change the DNS for those servers or create a script (if available to you) to do that for you.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 02:52 AM
Sorry, my mistake, the BackupISP would have the name of BackupISP and different address.
interface GigabitEthernet0/0.12
nameif BackupISP
security-level 0
ip address 95.16.24.242 255.255.255.248 standby 95.15.24.243
Question is can I copy the running config with anything that says Outside and just create a new one with BackupISP to create a second tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 02:55 AM
It appear ypu want to waste your time and my answer is igonre!!
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 03:14 AM
Sorry MHM, I appreciated your help. I understand what you said. Anything with Outside would be wiped. I just try to find out if I copy the configure back with sub-interface would the configuration be stored.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 03:20 AM
do you know which command use nameif OUTSIDE exactly ?
NO
so the better and safe solution use for subinterface new nameif like OUT1 then start config from zero.
config NAT and ACL and crypto ...etc.
copy same config and paste it when change interface will more harder than use new nameif
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 11:14 PM - edited 04-22-2024 02:56 AM
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide