- Cisco Community
- Technology and Support
- Security
- Network Security
- BGP between two remote FTD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
BGP between two remote FTD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2024 11:18 PM
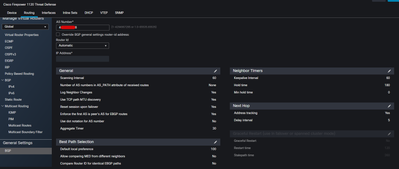
I have two Firepowers in two remote offices and i have two ISPs in each office, i had configured vti ipsec vpn between two offices but they are working with static routes, can i configure dynamic routing protocols for failover vpn? I tried to configure BGP but neighbours idle, what can you advice?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2024 11:33 PM
Share the config of vti and bgp of ftd
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 08:23 PM
Site A FMC configuration
Site B FDM configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 01:13 PM
Thanks for sharing
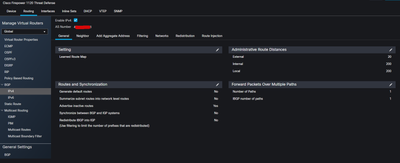
Now each FW have dual ISP
-config two VTI each one have it interface
- config two static route one for each VTI tunnel destination
-config bgp with two neighbors' one for each vti
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 11:50 PM
i have configured two vti and static routes everything works fine except BGP, i can ping each side with static route but i want dynamic update routes by BGP, in my case BPG neighbours are idle configuration i shared you, what can i do to up neighbours? Do i need to open 179 port from WAN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 12:25 AM
Can I see
Show run router <- from firepower cli
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 12:46 AM - edited 03-29-2024 12:48 AM
Sure
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF, BI - BGP InterVRF
Gateway of last resort is x.x.x.x to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via y.y.y.x, Link-to-ISP1
C 10.20.82.0 255.255.255.252 is directly connected, vti_10.20.82.1
L 10.20.82.1 255.255.255.255 is directly connected, vti_10.20.82.1
C 10.20.82.4 255.255.255.252 is directly connected, vti_10.20.82.5
L 10.20.82.5 255.255.255.255 is directly connected, vti_10.20.82.5
C 10.20.82.12 255.255.255.252 is directly connected, vti_10.20.82.13
L 10.20.82.13 255.255.255.255 is directly connected, vti_10.20.82.13
C 10.20.82.16 255.255.255.252 is directly connected, vti_10.20.82.17
L 10.20.82.17 255.255.255.255 is directly connected, vti_10.20.82.17
S 10.57.0.0 255.255.0.0 [1/0] via 10.20.82.2, vti_10.20.82.1
C 10.56.0.0 255.255.254.0 is directly connected, Network_Management
L 10.56.0.1 255.255.255.255 is directly connected, Network_Management
C 10.56.10.0 255.255.254.0 is directly connected, Server_Management
L 10.56.10.1 255.255.255.255 is directly connected, Server_Management
C 10.56.12.0 255.255.255.0 is directly connected, Shared_Server
L 10.56.12.1 255.255.255.255 is directly connected, Shared_Server
C 10.56.14.0 255.255.254.0 is directly connected, WLAN_Management
L 10.56.14.1 255.255.255.255 is directly connected, WLAN_Management
C 10.56.16.0 255.255.254.0 is directly connected, Production_3
L 10.56.16.1 255.255.255.255 is directly connected, Production_3
C 10.56.18.0 255.255.255.128 is directly connected, PRODUCTION_1
L 10.56.18.1 255.255.255.255 is directly connected, PRODUCTION_1
C 10.56.18.128 255.255.255.128 is directly connected, PRODUCTION_2
L 10.56.18.129 255.255.255.255 is directly connected, PRODUCTION_2
C 10.56.19.0 255.255.255.0 is directly connected, PRODUCTION_Server
L 10.56.19.1 255.255.255.255 is directly connected, PRODUCTION_Server
C 10.56.20.0 255.255.254.0 is directly connected, 4_PRODUCTION
L 10.56.20.1 255.255.255.255 is directly connected, 4_PRODUCTION
C 10.56.22.0 255.255.254.0 is directly connected, Wi-Fi_Leaders
L 10.56.22.1 255.255.255.255 is directly connected, Wi-Fi_Leaders
C 10.56.24.0 255.255.248.0 is directly connected, Wi-Fi_Employee
L 10.56.24.1 255.255.255.255 is directly connected, Wi-Fi_Employee
C 10.56.32.0 255.255.248.0 is directly connected, Wi-Fi_Guest
L 10.56.32.1 255.255.255.255 is directly connected, Wi-Fi_Guest
C 10.56.40.0 255.255.248.0 is directly connected, Maintenance_Device
L 10.56.40.1 255.255.255.255 is directly connected, Maintenance_Device
C 10.56.48.0 255.255.248.0 is directly connected, VoIP
L 10.56.48.1 255.255.255.255 is directly connected, VoIP
C 10.56.56.0 255.255.252.0 is directly connected, End_Device
L 10.56.56.1 255.255.255.255 is directly connected, End_Device
C 10.56.64.0 255.255.240.0 is directly connected, End_User
L 10.56.64.1 255.255.255.255 is directly connected, End_User
V 10.56.80.10 255.255.255.255
connected by VPN (advertised), Link-to-ISP1
C 10.56.86.0 255.255.254.0 is directly connected, Camera
L 10.56.86.1 255.255.255.255 is directly connected, Camera
S 10.58.0.0 255.255.0.0 [1/0] via 10.20.82.14, vti_10.20.82.13
C y.y.y.0 255.255.255.0 is directly connected, Link-to-ISP2
L y.y.y.y 255.255.255.255 is directly connected, Link-to-ISP2
V 192.168.70.6 255.255.255.255
connected by VPN (advertised), Link-to-ISP1
C x.x.x.y 255.255.255.240
is directly connected, Link-to-ISP1
L x.x.x.x 255.255.255.255
is directly connected, Link-to-ISP1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 02:45 AM
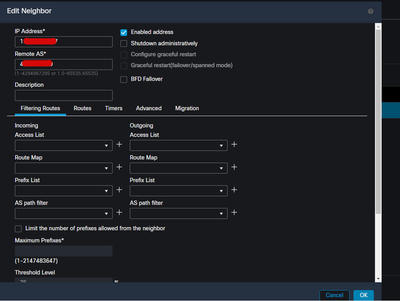
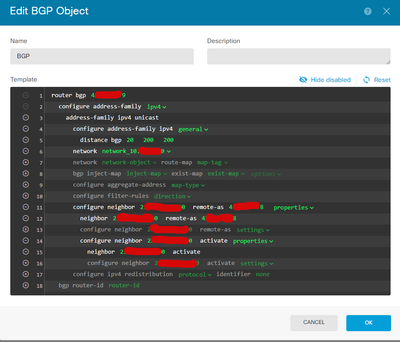
The neighbor command you have configured should be the VTI interface IP of the remote side, verify that this is correct on both ends.
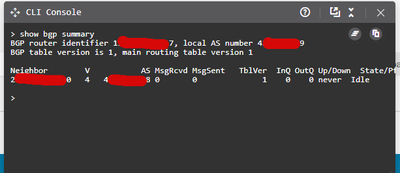
Is BGP flapping or just never being established?
Are you using BGP authentication? if yes, have you verified that the passwords match on both sides?
Are you redistributing connected and / or static? If yes, remember to configure route maps to exclude the public IP (VTI source IP) from being learned over BGP as this will cause problems.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 03:53 AM
@Marius Gunnerud написал (-а):The neighbor command you have configured should be the VTI interface IP of the remote side, verify that this is correct on both ends.
Is BGP flapping or just never being established?
Are you using BGP authentication? if yes, have you verified that the passwords match on both sides?
Are you redistributing connected and / or static? If yes, remember to configure route maps to exclude the public IP (VTI source IP) from being learned over BGP as this will cause problems.
I need BGP to failover VTI interfaces, to send traffic from secondary VTI if main VTI down. I configured BGP neighbours with WAN IP and it is never estabilished, i don't use authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 07:37 AM
You need to use the VTI interface IP in the neighbor command, not the WAN IP.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 04:04 AM
VTI IP need to use in bgp 10.20.82.14' 10.20.82.13'
The WAN IP need to add as static for both ISP' i.e.
WAN IP for VTI1 have it static route
WAN IP of VTI2 have it static route
Please I need to see
Show run router
not show route
Thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 04:24 AM
@MHM Cisco World написал (-а):
VTI IP need to use in bgp 10.20.82.14' 10.20.82.13'
The WAN IP need to add as static for both ISP' i.e.
WAN IP for VTI1 have it static route
WAN IP of VTI2 have it static route
Please I need to see
Show run router
not show route
Thanks
MHM
> show running-config router
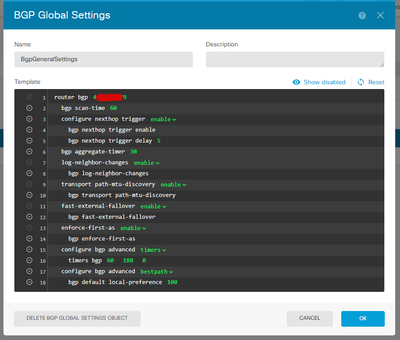
router bgp 4XXXXXXX8
bgp log-neighbor-changes
bgp router-id vrf auto-assign
address-family ipv4 unicast
neighbor a.a.a.a remote-as 4XXXXXXX9
neighbor a.a.a.a transport path-mtu-discovery disable
neighbor a.a.a.a activate
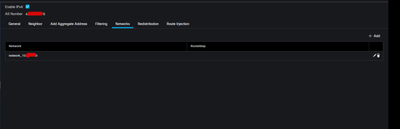
network 10.56.0.0 mask 255.255.0.0
no auto-summary
no synchronization
exit-address-family
The WAN IP need to add as static for both ISP' i.e.
WAN IP for VTI1 have it static route
WAN IP of VTI2 have it static route
Can you give example for this please i dont understand?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2024 09:04 AM
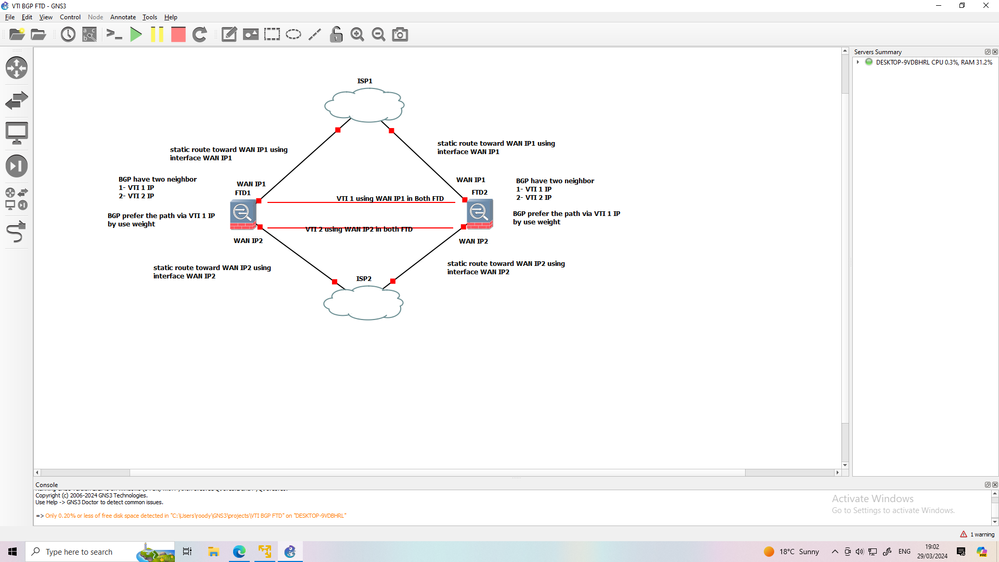
this is topology and not you need for your requirement
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2024 12:36 AM
Sorry for my stupid question but i cant understand why we need static route toward WAN IP1 using interface WAN IP2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2024 12:41 AM
static route toward WAN IP1 (FTD2) using interface WAN IP1 (FTD1)
This what I meaning
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide