- Cisco Community
- Technology and Support
- Security
- Network Security
- block ip addresses that try to brute force into VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 11:46 PM - edited 04-27-2023 11:48 PM
Hello,
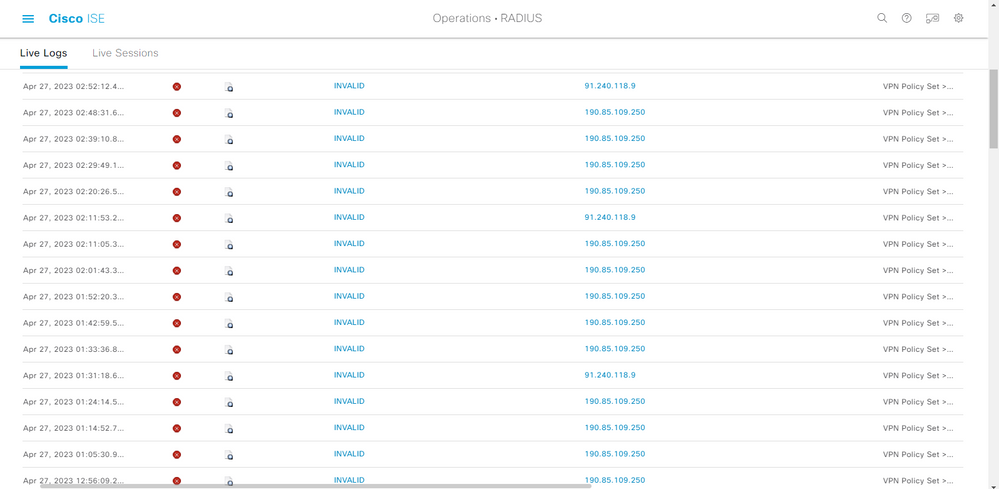
Starting from the last three weeks these IP Addresses are attempting to VPN into our network. In the ISE LiveLogs we can see that there are multiple attempts from these ip addresses. These IP addresses were added to the prefilter block rule on the FTD firewall. But still the authentication traffic is reaching the ISE server. shouldn't it be blocked the firewall.
Any ideas why this address is still able to attempt auth, even though it should be getting denied before it even gets that far?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 12:04 AM
@mikeyasg if the pre-filter rule you are referring to is configured on the FTD acting as the Remote Access VPN concentrator, then that will not work. The pre-filter and Access Control rules control traffic "through" the firewall and not "to" the firewall itself, so it cannot block those connections.
Rarely used, but you could use a control-plane ACL to deny the specific IP addresses and permit the rest of the remote access vpn connections. Example: https://integratingit.wordpress.com/2021/06/26/ftd-control-plane-acl/
Or deny the traffic on the upstream ISP router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 12:04 AM
@mikeyasg if the pre-filter rule you are referring to is configured on the FTD acting as the Remote Access VPN concentrator, then that will not work. The pre-filter and Access Control rules control traffic "through" the firewall and not "to" the firewall itself, so it cannot block those connections.
Rarely used, but you could use a control-plane ACL to deny the specific IP addresses and permit the rest of the remote access vpn connections. Example: https://integratingit.wordpress.com/2021/06/26/ftd-control-plane-acl/
Or deny the traffic on the upstream ISP router.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 09:40 AM
Agree with @Rob Ingram . Filter on an upstream router or terminate RA VPN on a firewall in the DMZ. then the Internet-facing firewall rules would apply to the incoming traffic.
Regarding Duo, generally the Duo configuration (whether SSO, Duo Auth Proxy or Duo Access Gateway) will be still trying to perform the first authentication against your primary authentication source - e.g., AD via ISE. So the attempts will still be logged by ISE (or AD if you bypass ISE for AuthC and only use it for AuthZ).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 12:06 AM
>...These IP addresses were added to the prefilter block rule on the FTD firewall.
- Depends on what you mean by that , guess that should not be 'prefilter block' , but just block or deny/drop (e.g.)
M.
-- ' 'Good body every evening' ' this sentence was once spotted on a logo at the entrance of a Weight Watchers Club !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 03:35 AM
this VPN is RAVPN or L2L VPN ?
if it L2L VPN then the solution is Control-plane
if it RAVPN then I think Duo can solve the issue <<- this I need to dive deep to check best solution for you but idea is the ASA make first auth and then send to ISE for second auth, here only the user that pass first Auth will send to ISE for more Auth, the ASA will drop other attempt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 09:57 AM
Can I use Duo to protect ASA local account logins?
Absolutely! To protect users local to the ASA, with the Duo LDAPS configuration for SSL VPN, continue to use the "LOCAL" AAA Server Group for authentication and add the Duo LDAP AAA server group for secondary authentication.
To protect local ASA users connecting with the Duo RADIUS configuration for SSL VPN clients, use the duo_only_client and radius_server_duo_only configurations in your Authentication Proxy setup, and again continue to use the "LOCAL" AAA Server Group for authentication and add the Duo RADIUS AAA server group for secondary authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2023 12:09 AM
The vpn is RAVPN and we are thinking to use control plane ACL as @Rob Ingram suggested. if it is applicable for RAVPN or blocking these ip on the upstream router. But blocking the traffic on upstream router would be adding the addresses everytime we face these issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2023 12:52 AM
@mikeyasg yes control-plane ACL works on RAVPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2023 02:31 AM
Please can you confirm that
One IP is outside interface IP of FW
Other is IP from ravpn pool ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2023 06:41 AM
The outside interface is the vpn concentrator and the endpoint that is making the remote connection will get ip from the ravpn pool. But the screenshot that i shared is neither the outside interface nor the ip from the pool rather it is the ip address that belongs to the endpoint initiating the vpn connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2023 07:17 AM
then if you sure that these IP is not OUT and VPN Pool
as other mention you can use ACL
Client-internet-ASA-INside-ISE
apply ACL to INside allow only Mgmt IP to send to ISE plus first IP of VPN Pool (for more sure allow all VPN Pool)
that it.
you will ask then how RAVPN connect to ISE , the RAVPN not direct connect to ISE for auth, the FW do this, FW work as proxy to auth RAVPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2023 06:55 AM
Thank You all and @Rob Ingram We were able to use the control plane ACL and it was successful Thank You for your support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2023 07:01 AM
Sorry for my info.
What you permit and what you deny in control-plane acl??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 08:05 AM - edited 04-17-2024 08:05 AM
Having a router upstream from the FTD, wouldn't it be possible to create a correlation policy and use the Cisco IOS Null Route Module to automate blocking the offending IP's at the upstream router?
I began looking into this option this morning but am not clear as to how to create and associate the remediation step with the correlation policy.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


