- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Drop-reason: (acl-drop) Flow is denied by configured rule
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2024 09:48 AM
Hello,
I ran the following packet tracer using a destination on the Inside with private IP and I'm trying to understand what rule its specifically referencing when it say's the flow was dropped.
firepower# packet-tracer input outSIDE udp 69.185.96.215 1025 10.83.200.25 3544 detaild
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Elapsed time: 30708 ns
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffbc3df5f0, priority=1, domain=permit, deny=false
hits=281051874026, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=OUTSIDE, output_ifc=any
Phase: 2
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Elapsed time: 36679 ns
Config:
Additional Information:
Found next-hop 10.180.0.201 using egress ifc INSIDE(vrfid:0)
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Elapsed time: 14714 ns
Config:
access-group CSM_FW_ACL_ global
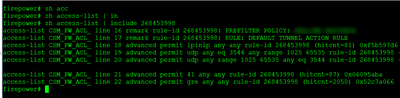
access-list CSM_FW_ACL_ advanced permit udp any range 1025 65535 any eq 3544 rule-id 268453998
access-list CSM_FW_ACL_ remark rule-id 268453998: PREFILTER POLICY: FASTPATH
access-list CSM_FW_ACL_ remark rule-id 268453998: RULE: DEFAULT TUNNEL ACTION RULE
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Forward Flow based lookup yields rule:
in id=0xffa81d3180, priority=12, domain=permit, deny=false
hits=13460, user_data=0xffddd42b00, cs_id=0x0, use_real_addr, flags=0x0, protocol=17
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=3544, tag=any, ifc=any, vlan=0,
src nsg_id=none, dst nsg_id=none
sport range<0> : 1025-65535 dscp=0x0, input_ifc=any, output_ifc=any
Phase: 4
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Elapsed time: 14714 ns
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffa85d57b0, priority=7, domain=conn-set, deny=false
hits=1858687396, user_data=0xffa85d3340, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any,
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=OUTSIDE(vrfid:0), output_ifc=any
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Elapsed time: 14714 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffc096c720, priority=0, domain=nat-per-session, deny=true
hits=6688481459, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any,
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=any, output_ifc=any
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Elapsed time: 14714 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffbc3e5970, priority=0, domain=inspect-ip-options, deny=true
hits=5318748547, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=OUTSIDE(vrfid:0), output_ifc=any
Phase: 7
Type: FOVER
Subtype: standby-update
Result: ALLOW
Elapsed time: 62269 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffbe9871d0, priority=20, domain=lu, deny=false
hits=930072487, user_data=0x0, cs_id=0x0, flags=0x0, protocol=17
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=OUTSIDE(vrfid:0), output_ifc=any
Phase: 8
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Elapsed time: 3412 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffb4c5fab0, priority=13, domain=ipsec-tunnel-flow, deny=true
hits=1328718509, user_data=0x0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=OUTSIDE(vrfid:0), output_ifc=any
Phase: 9
Type: NAT
Subtype: rpf-check
Result: DROP
Elapsed time: 14501 ns
Config:
nat (INSIDE,OUTSIDE) source dynamic any interface
Additional Information:
Forward Flow based lookup yields rule:
out id=0xffc0c80080, priority=6, domain=nat-reverse, deny=false
hits=24377256, user_data=0xffc0c75990, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=OUTSIDE(vrfid:0), output_ifc=INSIDE(vrfid:0)
Result:
input-interface: OUTSIDE(vrfid:0)
input-status: up
input-line-status: up
output-interface: INSIDE(vrfid:0)
output-status: up
output-line-status: up
Action: drop
Time Taken: 191925 ns
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x000000aaad882920 flow (NA)/NA
when running it this way my hit counter increases on the rule id 268453998. However, if I run this same packet tracer using my public IP as the destination I get the following output and my hit count doesn't go up.
Phase: 1
Type: NAT
Subtype: per-session
Result: ALLOW
Elapsed time: 30423 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffc096c720, priority=0, domain=nat-per-session, deny=true
hits=6688965993, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any,
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=any, output_ifc=any
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: DROP
Elapsed time: 30423 ns
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xffbc3e0a00, priority=0, domain=permit, deny=true
hits=79288593, user_data=0xb, cs_id=0x0, use_real_addr, flags=0x1000, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any,
src nsg_id=none, dst nsg_id=none
dscp=0x0, input_ifc=OUTSIDE(vrfid:0), output_ifc=any
Result:
input-interface: OUTSIDE(vrfid:0)
input-status: up
input-line-status: up
Action: drop
Time Taken: 60846 ns
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x000000aaad87a248 flow (NA)/NA
Why is that and how can I figure out what rule this hit?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2024 09:52 AM
You want to access server INside FTD from OUTside
You use NAT overload and this make retrun traffic drop.
You need static NAT for this case
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2024 08:46 PM
It looks like you are missing NAT configuration mapping a public IP to the private IP. Can you verify that you have this configured, and if you have it configured double check that it is configured correctly.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2024 09:06 AM
You need to create a NAT rule for that inbound traffic. If you have additional public IP different than the one you have on the OUTSIDE interface then you can do something similar to this:
object network SERVER-10.83.200.25
host 10.83.200.25
nat (INSIDE,OUTSIDE) static < the additional public IP >
And if you have only a single public IP which is the one assigned to the OUTSIDE interface then you can do something similar to this:
object network SERVER-10.83.200.25
host 10.83.200.25
nat (INSIDE,OUTSIDE) static < the OUTSIDE interface public IP > service udp 3544 3544
Or
object network SERVER-10.83.200.25
host 10.83.200.25
object network OUTSIDE-INTERFACE-PUBLIC-IP
host x.x.x.x
object service PORT-3544
service udp source eq 3544
nat (INSIDE,OUTSIDE) source static SERVER-10.83.200.25 OUTSIDE-INTERFACE-PUBLIC-IP service PORT-3544 PORT-3544
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 06:41 AM
Hello,
I apologize if I wasn't clear in my original ask. I'm not looking to solve for any NAT as this traffic should be blocked. I'm trying to understand what rule is actually doing the blocking. Upon looking at the access list via command line you can see all of these default permit statements that I don't have configured on the GUI. Running a packet tracer proves its being blocked but I would like to know what rule is doing the blocking. Hope that clears up what I'm after.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2024 08:05 AM
You can use the rule-id to identify which rule is being match, but you need to use API to do it.
You would first need to find the ID of the ACP you want to filter on and then remove the ACP ID portion of the ID and add the rule ID.
So the ID you are looking for is 268453998 and your ACP ID is 0F920F8-abcd-efgh-0000-030064774061, then you would remove the last portion of the ACP ID (the 12 numbers that come after the last -). Just bear in mind that there needs to be 12 characters in the last portion so you would add 0s if your rule ID has less than 12. So the rule ID you would be looking for is 0F920F8-abcd-efgh-0000-000268453998
Then you can use the following cURL statement to fetch the rule. remember to replace DOMAINUUID, access-policy UUID and access rule UUID to be the actual values. Also you would need to generate an access token.
curl -k -X 'GET' \
'https://10.20.30.40/api/fmc_config/v1/domain/{DOMAINUUID}/policy/accesspolicies/10F920F8-abcd-efgh-0000-030064774061/accessrules/0F920F8-abcd-efgh-0000-000268453998' \
-H 'accept: application/json' \
-H 'X-auth-access-token: e2e79282-aaaa-bbbb-cccc-4860e2964f0b'
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2024 08:59 AM
Marius,
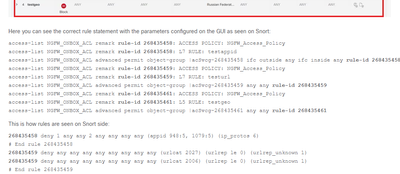
I will give that a try even though this seems overly complicated for what feels like a routine function within the CLI. I found a Cisco document that describes what I'm after but they don't go into detail on how they obtained the snort side. They use the rule ID to queried snort somehow to show what the results would be of hitting the rule. That's what I'm trying to do. information. https://www.cisco.com/c/en/us/support/docs/security/secure-firewall-threat-defense/218196-understand-how-lina-rules-configured-wit.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2024 09:20 AM
The easiest way in the long run would be to make a script in python and have it fetch the rule, you could also do this via the https://<FMC-IP/api/api-explorer page but again you would need to perform this in several steps.
But in short, to find the rule via the rule-id that you see in the CLI or packet-tracer, you will need to use API in some way.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2024 09:25 AM
Can you share all acl in lina?
Why you use | in
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide