- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: MY logs from Firepower 5516-x are filled with error and warning m
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
MY logs from Firepower 5516-x are filled with error and warning msg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 05:31 AM - edited 04-21-2024 08:48 AM
Hello all
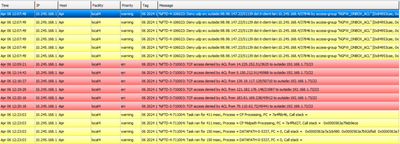
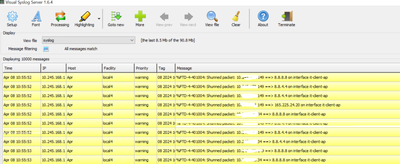
I'm receiving hundreds of warning messages i am getting in our syslog from our Cisco ASA 5516-x. The warning message are on below same as screenshots and dunt know how to act with these kind of massages as its huge numbers of massages coming and dunt know how to stop or its kind of attack or what ?
Note: im using free syslog system called visual syslog server app and its an open source app and ASA version is Cisco ASA5516-X Threat Defense (75) Version 7.0.1 (Build 84) ,Also no routing configured on ASA and ASA is directly connected to L3 core switch
who are these IPs coming from ! i think attackers trying to access outside IF of ASA which directly connected to ISP router and how to stop this ? its huge number of massages coming and cannot stop !
How to block the incoming weak ports such as ping/telnet/ssh also traffic from internet to ASA OUTSIDE interface with ip 192.168.1.73 ?? i think something running trying to access ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 06:08 AM
I will assume that this continue of your previous unsolved issue
the solution as I and other mention is
deny IP or shun it (if it single IP)
set the embryonic TCP connection per client
if Not help you
use Thread Detection in ASA, this check the TCP failed 3-way handshake and shun the IP for specific duration (configurable)
Ascertain ASA Threat Detection Functionality and Configuration - Cisco
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 06:13 AM - edited 04-06-2024 06:43 AM
shall i collect all these unknow IP addresses and shun them all !? these IP addresses coming from outside to inside or trying to access my system some how if im right according to the massages on syslog !? if yes so how to shun them all from ASA FTD GUI ? shall i use flexconnect option ! can u share with me please how ?
outside:
received (in 1984295.120 secs):
231191595 packets 186672209093 bytes
1 pkts/sec 94001 bytes/sec
transmitted (in 1984295.120 secs):
144647652 packets 62228603626 bytes
1 pkts/sec 31001 bytes/sec
1 minute input rate 16 pkts/sec, 4230 bytes/sec
1 minute output rate 13 pkts/sec, 5582 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 13 pkts/sec, 3383 bytes/sec
5 minute output rate 11 pkts/sec, 4858 bytes/sec
5 minute drop rate, 0 pkts/sec
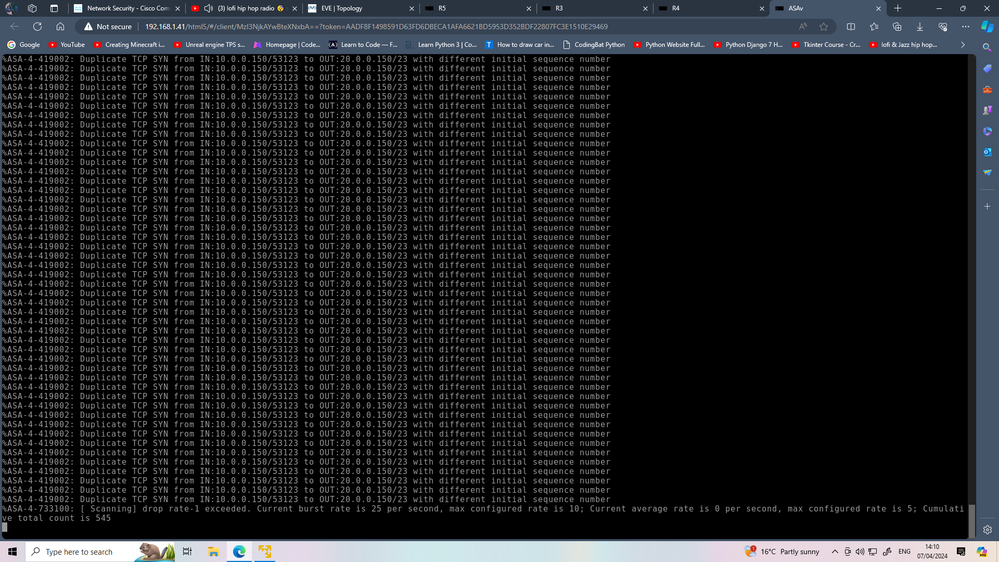
Also regarding the Duplicate TCP SYN massages forming from internet clients who are connecting to wifi office !! shall i shun them also ? and what is shun doing exactly ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 11:42 AM
I know your issue is urgently but for me I need some time to check points ypu share' sorry for late reply.
Now' I real your reply and other comment
And I retrun to point that there is asymmetric or loop routing'
You mention that this direct connect L3SW and ISP'
You need defualt route but I think you use pppoe to ISP abd you auto get defualt route' please confirm this point?
To make sure that this is not loop
Select any IP appear in log
Do packet-tracer
And see the ingress and egress of packet is it same or not.
Waiting your reply
Thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2024 04:15 AM
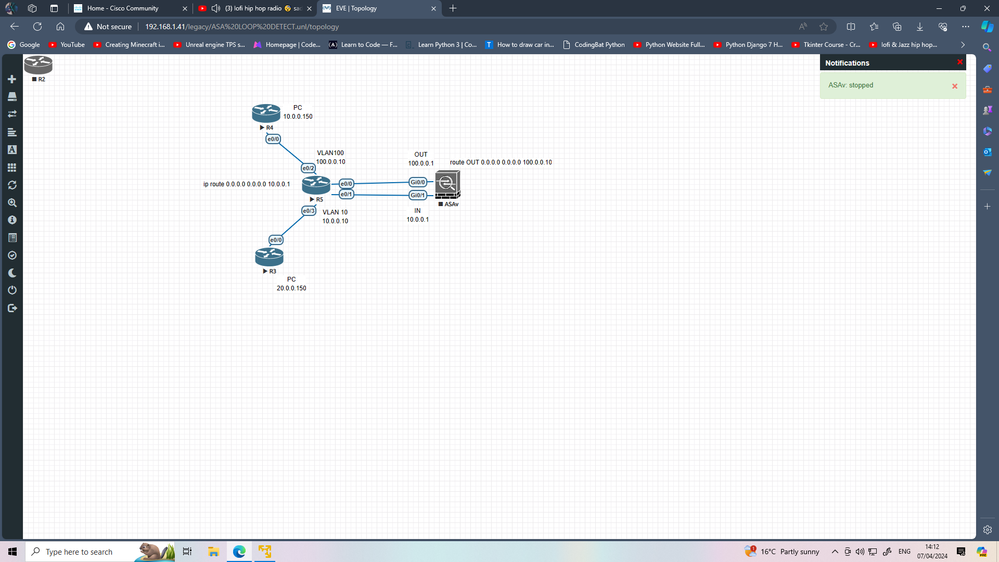
simple lab and wrong routing generate LOOP
as you can see same log you get.
so one Q
are you connect two port of FTD to same SW ? or is ISP have any connection to L3SW?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 06:51 AM
@amralrazzaz the error in your log - 710003 does indicate an attack. Multiple IP addresses tried connecting to 192.168.1.73 using SSH, this was denied as you do not allow connections from those source IP addresses. No need to shun as the FTD has already denied those connections, as per the message.
Error Message %FTD-3-710003: {TCP|UDP} access denied by ACL from source_IP/source_port to interface_name :dest_IP/service
Explanation The Secure Firewall Threat Defense device denied an attempt to connect to the interface service. For example, the Secure Firewall Threat Defense device received an SNMP request from an unauthorized SNMP management station. If this message appears frequently, it can indicate an attack.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 07:34 AM - edited 04-06-2024 07:49 AM
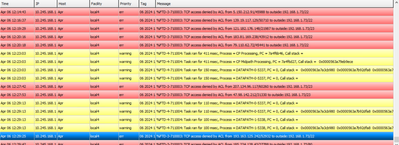
@Rob Ingram Thanks dear and i have 1st question , so these hundreds of massages coming to syslog i can ignore as all these connections denied already form outside to 192.168.1.73 (outside ASA i/f)? and this is the part of accessing from internet or outside to my ASA using outside I/F ! so shall i ignore ?
2nd question is for %FTD Duplicate TCP SYN from inside to outside with different initial !!
This messages appears during working hours when users connected to WIFI office VLAN using the inside ASA port (it-client-ap) and its disappearing when users leave office ! so i have just apply the below action using flexconnect but actually I'm not sure if this will do something or i have to remove ?
ASAFTD# show running-config all threat-detection
threat-detection rate dos-drop rate-interval 600 average-rate 100 burst-rate 400
threat-detection rate dos-drop rate-interval 3600 average-rate 80 burst-rate 320
threat-detection rate bad-packet-drop rate-interval 600 average-rate 100 burst-rate 400
threat-detection rate bad-packet-drop rate-interval 3600 average-rate 80 burst-rate 320
threat-detection rate acl-drop rate-interval 600 average-rate 400 burst-rate 800
threat-detection rate acl-drop rate-interval 3600 average-rate 320 burst-rate 640
threat-detection rate conn-limit-drop rate-interval 600 average-rate 100 burst-rate 400
threat-detection rate conn-limit-drop rate-interval 3600 average-rate 80 burst-rate 320
threat-detection rate icmp-drop rate-interval 600 average-rate 100 burst-rate 400
threat-detection rate icmp-drop rate-interval 3600 average-rate 80 burst-rate 320
threat-detection rate scanning-threat rate-interval 600 average-rate 5 burst-rate 10
threat-detection rate scanning-threat rate-interval 3600 average-rate 4 burst-rate 8
threat-detection rate syn-attack rate-interval 600 average-rate 100 burst-rate 200
threat-detection rate syn-attack rate-interval 3600 average-rate 80 burst-rate 160
threat-detection rate fw-drop rate-interval 600 average-rate 400 burst-rate 1600
threat-detection rate fw-drop rate-interval 3600 average-rate 320 burst-rate 1280
threat-detection rate inspect-drop rate-interval 600 average-rate 400 burst-rate 1600
threat-detection rate inspect-drop rate-interval 3600 average-rate 320 burst-rate 1280
threat-detection rate interface-drop rate-interval 600 average-rate 2000 burst-rate 8000
threat-detection rate interface-drop rate-interval 3600 average-rate 1600 burst-rate 6400
threat-detection basic-threat
threat-detection scanning-threat shun duration 1800
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 09:54 AM
@amralrazzaz anything in the logs matching the syslog event id - 710003 are denied, so can be ignored.
In regard to the duplicate SYN, if you shun the traffic from the legitimate wireless users, that will block them from any communication through the Firewall. You'd be better investigating these devices and determine if it's a misbehaving client or a problem with the destination website (the logs indicate its the same destination IP).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2024 10:10 AM
@amralrazzaz, you need to figure out WHY 419002 messages are produced BEFORE trying to apply any commands like "set connection" and "threat-detection".
First, does 419002 always complain about 52.123.128.14 or it can contain other Internet IPs as well? (We understood that source IPs vary, but how about destination IPs)?
Second, "no routing configured" is not true. You should at least have a default route to the Internet, right? I believe your firewall runs in routed mode since you mentioned L2L VPN, right?
Third, 419002 messages are almost always produced when there is a routing loop in the network. When TCP segment goes through the firewall, the firewall randomizes its SEQ#. In case of a routing loop, if the same packet is again received by the firewall, it prints 419002 and drops the packet. You need to carefully examine your physical topology (L1) and logical topology (L2) and configuration (of the switch) and then collect captures on the firewall interfaces to find out why the firewall sees same packet few times. E.g. in the past such issues could be caused by Windows computers bridging between wireless and wired interfaces, although it's hard to believe that you're facing with this issue today.
106023 messages are produced when the packet is dropped by the interface ACL. Usually they're useless and hence it's typically recommended to add "log" option to ACL lines (to optimize and convert them to 106100) or "log disable" (to get rid of them completely). This should be possible in the GUI too.
711004 pertains to CPU utilization which can increase significantly if traffic rate is high (again, a loop?). You can increase logging level for them to 2 and pay attention to "show cpu detail".
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2024 07:52 AM - edited 04-08-2024 06:05 AM
@tvotna Dear i have configured the below and not sure if it will impact or not & also i HYG the CPU details on below:
Basic-rate-Threat-Detection :-
threat-detection basic-threat
threat-detection rate acl-drop rate-interval 1200 average-rate 250 burst-rate 550
Threat-Detection-statistics :-
threat-detection statistics host number-of-rate 2
threat-detection statistics tcp-intercept
threat-detection statistics tcp-intercept rate-interval 45 burst-rate 400 average-rate 100
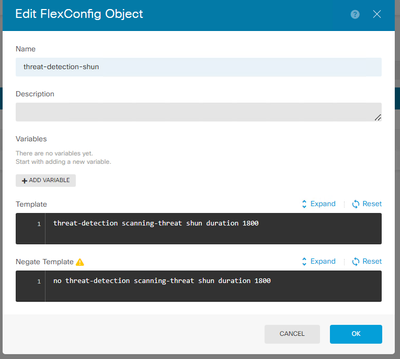
Threat-Detection-Scanning-shun: :-
threat-detection scanning-threat
threat-detection rate scanning-threat rate-interval 1200 average-rate 250 burst-rate 550
threat-detection scanning-threat shun
threat-detection scanning-threat shun duration 1000
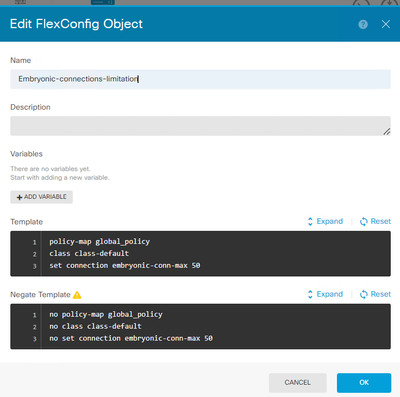
Embryonic-connections-limitation:-
class-map tcp_syn
match port tcp eq 80
match port tcp eq 443
match port tcp eq 23
match port tcp eq 22
match port tcp eq 21
policy-map global_policy
class tcp_syn
set connection conn-max 100
set connection embryonic-conn-max 200
set connection per-client-embryonic-max 10
set connection per-client-max 5
set connection random-sequence-number enable
set connection timeout embryonic 0:0:45
set connection timeout half-closed 0:25:0
set connection timeout tcp 2:0:0
service-policy global_policy global
ProtectingAgainst-IP-Spoofing-Attacks:-
ip verify reverse-path interface outside
> show cpu usage
CPU utilization for 5 seconds = 3%; 1 minute: 2%; 5 minutes: 1%
> show cpu core
Core 5 sec 1 min 5 min
Core 0 1.0% 1.0% 0.7%
Core 1 0.8% 0.7% 0.6%
> show cpu profile
No profiling data.
> show cpu detailed
Break down of per-core data path versus control point cpu usage:
Core 5 sec 1 min 5 min
Core 0 0.4 (0.4 + 0.0) 0.9 (0.7 + 0.1) 0.6 (0.5 + 0.0)
Core 1 0.4 (0.4 + 0.0) 0.8 (0.6 + 0.1) 0.7 (0.5 + 0.0)
Current control point elapsed versus the data and control point elapsed for:
5 seconds = 18.3%; 1 minute: 18.1%; 5 minutes: 18.1%
CPU utilization of external processes for:
5 seconds = 0.4%; 1 minute: 0.9%; 5 minutes: 0.5%
Total System CPU utilization for:
5 seconds = 1.0%; 1 minute: 1.9%; 5 minutes: 1.4%> show cpu usage > show cpu core> show cpu profile > show cpu detailed
New massages came to syslog after apply the above configuration and its users at office complain of no internet connection !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 10:15 AM
@tvotna @MHM Cisco World @Rob Ingram
lets me focus on this now and if there is any actions to apply to avoid or mitigate this because i think its impacting the connectivity to ASA FTD via WEB HTTPS ! Most times showing down and coming up again , but connecting to the device via ssh is stable anytime !
Error Message %ASA-4-106023: Deny protocol src [interface_name:source_address/source_port] [(idfw_user|FQDN_string)] dst interface_name:dest_address/dest_port [(idfw_user|FQDN_string)] [type {string}, code {code}] by access_group acl_ID [0x8ed66b60, 0xf8852875]
Error Message Explanation: A real IP packet was denied by the ACL. This message appears even if you do not have the log option enabled for an ACL. The IP address is the real IP address instead of the values that display through NAT. Both user identity information and FQDN information are provided for the IP addresses if a matched one is found. The ASA logs either identity information (domain\user) or the FQDN (if the username is not available). If the identity information or FQDN is available, the ASA logs this information for both the source and destination.
Message: %FTD-3-710003: {TCP|UDP} access denied by ACL from source_IP/source_port to interface_name:dest_IP/service
Error Message %FTD-3-710003: {TCP|UDP} access denied by ACL from source_IP/source_port to interface_name :dest_IP/service
Explanation The Secure Firewall Threat Defense device denied an attempt to connect to the interface service. For example, the Secure Firewall Threat Defense device received an SNMP request from an unauthorized SNMP management station. If this message appears frequently, it can indicate an attack.
Message: %FTD-5-199017: sudo: root : TTY=unknown ; PWD=/ ; USER=root ; COMMAND=/usr/bin/pgrep -x snort
Message: %FTD-5-199017: syslog
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2024 01:52 PM
By default FTD / ASA running FTD software does not accept management connections to data interfaces. Are you by chance managing the FTD via a data interface?
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 01:45 AM - edited 04-22-2024 01:49 AM
Dear its not by data interface its only by management interface ! but its not stable and the webserver GUI like 60% of the time is down and then coming up again! which means something like DDoS attack or hundreds of massages coming to syslog from outside as requests to access and denied for sure ! But im not sure if this is reason of down time the https GUI ! i can reach to ASA via putty SSH normally anytime but GUI no coz always not stable between up and down !!
One Note:
i think when i applied the below command the GUI connectivity back to stability but on other hands the users at office complain of no internet connection because its shunned all ip addresses which cause TCP SYN ACK issue !
Threat-Detection-Scanning-shun: :-
threat-detection scanning-threat
threat-detection rate scanning-threat rate-interval 1200 average-rate 250 burst-rate 550
threat-detection scanning-threat shun
threat-detection scanning-threat shun duration 1000
Then i removed it again to return back the internet connection to users !!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide