- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: SSH Terrapin Prefix Truncation Weakness
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSH Terrapin Prefix Truncation Weakness
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2024 05:56 AM
Good Day All,
I found a vulnerability on my 4321 router regarding this:
"The remote SSH server is vulnerable to a man-in-the-middle prefix truncation weakness known as Terrapin. This can allow a remote, man-in-the-middle attacker to bypass integrity checks and downgrade the connection's security."
Anyone information on how to resolve this is greatly appreciated.
-Alfred
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2024 09:56 PM - edited 01-30-2024 10:00 PM
Hi @mmsabaeai ,
I am currently going to apply this fix and wanted to make sure the fix is already applied.
1. Do you have a command to run to verify if the fix already was applied?
2. Does this require a server reboot or will this cause impact traffic?
3. I believe this fix is applicable for Cisco Nexus 9300?
Thank you,
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2024 10:41 PM
>3. I believe this fix is applicable for Cisco Nexus 9300?
For Nexus 9300, NX-OS, the fix will be different for modifying the SSH daemon CipherSuites. ~BAS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 06:47 AM
If you are still able to ssh to the device after adding that command then that is the correct way. I used Nessus scanner to identify vulnerabilities on my network device that how I was able to detect this vulnerability. hth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 10:04 PM
Hi,
I there a way to run a command to check if the fix was is already working? I dont have access on the customer physical location and just doing it remotely and losing ssh will be a problem for me. It is the customer who do the nessus scan.
Thank you,
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2024 10:48 PM
> Is there a way to run a command to check if the ..
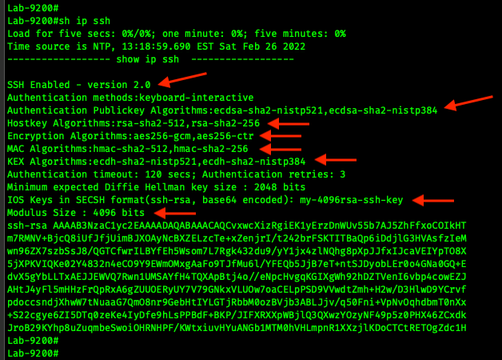
IOS (and IOS-XE?)# show ip ssh
Cat9K ( NX-OS ) # show ssh server
(it should print the acceptable KEX Key Exchange, MACs, and encryption CipherSuites)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2024 12:23 AM
Hi,
I tried to check the command but it seems (ip ssh server algorithm encryption) is not available on my Nexus Cisco Nexus9000.
I tried to tab below command nothing shows.
(config)# ip ssh ser
Thank you,
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2024 10:59 PM
Terrapin CVE-2023-48795
Related to the the following Nessus plugins: 153953, 187315
https://www.tenable.com/plugins/nessus/187315
https://www.tenable.com/plugins/nessus/153953
For Traditional IOS (this thread was originally about IOS-XE) version 15.2(8)+ on the Industries/IOT ( IE-Series ) switches, I've validated the following change with Nessus while maintaining compatibility with PuTTY v0.79 and v0.80:
IOS-Traditional (config)# ip ssh server algorithm encryption aes256-ctr
IOS-Traditional (config)# ip ssh server kex ecdh-sha2-nistp521
IOS-Traditional (config)# ip ssh server mac hmac-sha2-256 hmac-sha2-512
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2024 04:28 PM
Those commands don't work on Nexus devices. Has anyone found the command to remediate this vuln on nexus devices?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2024 09:53 PM
I am using Nexus N9K C93180YC-FX and running version is 10.2.5
It has been reported that the switch is having CVE-2023-48795. Is this applicable to nexus? and if Yes then what is the work around strictly for Nexus. Currently SSH version 2 is enabled.
Thanks in advanced
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 07:47 AM
I'm not sure if you've figured this out yet or not, but we have so I wanted to share.
1. Enable bash shell feature - #feature bash-shell
2. Connect to bash shell - #run bash sudo su
3. Change directory to /isan/etc - cd /isan/etc
4. cat dcos_sshd_config
5. Make a backup copy of the file on the bootflash before editing so you can restore it if something goes wrong - cp dcos_sshd_config /bootflash/dcos_sshd_config_backup
6. Open the dcos_sshd_config file and remove the unwanted MAC ciphers - vi dcos_sshd_config
7. move to the line which you want to delete (chacha20-poly1305@openssh.com)
8. Press "x" to delete the characters.
9. ESC then :wq!
10. cat /isan/etc/dcos_sshd_config file will shows chacha20-poly1305@openssh.com cipher is no longer present.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2024 10:15 PM
We have received SSH Terrapin Prefix Truncation Weakness (CVE-2023-48795) vulnerability on AIR-CT5508-K9 IOS version AireOS 8.5.140.0. This vulnerability is associated with bug CSCwi61646. Please advise if we can ignore this vulnerability as on below link it says workaround is Not Available or Not Applicable. Or kindly suggest for the FIX.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide