- Cisco Community
- Technology and Support
- Networking
- Routing
- ASA 5515-X Failover setup by using different subnet standby ip
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5515-X Failover setup by using different subnet standby ip
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2023 10:03 PM - edited 09-29-2023 10:34 PM
Hello community! I hope everything is well in your life.
I have 2x ASA 5515-X and I was using Active/Standby before and it was working great.
We moved in a new datacenter and in this datacennter they have 2x gateway switch.
They gave me 1 uplink cable from each gateway.
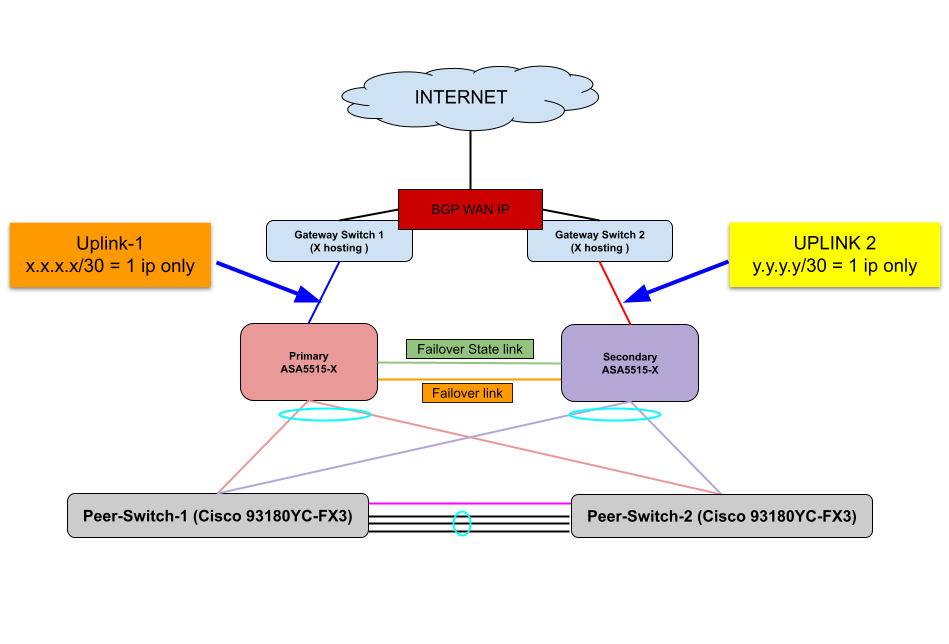
My current diagram is below:
My problem is they gave me 1 ip for each uplink cable and these ip's are only working on their cable because these ip's are two different /30 subnets.
ASA5515 Active/Standby failover configuration do not accept 2 different subnet as primary and standby ip. They have to be in the same subnet.
Because of this issue I have to change my configuration!
I think there is only 2 different solution to solve this issue and in my mind I'm sure both of these solution will work but I'm trying to find a proved solution for this kind of case. Let me tell you my ideas first.
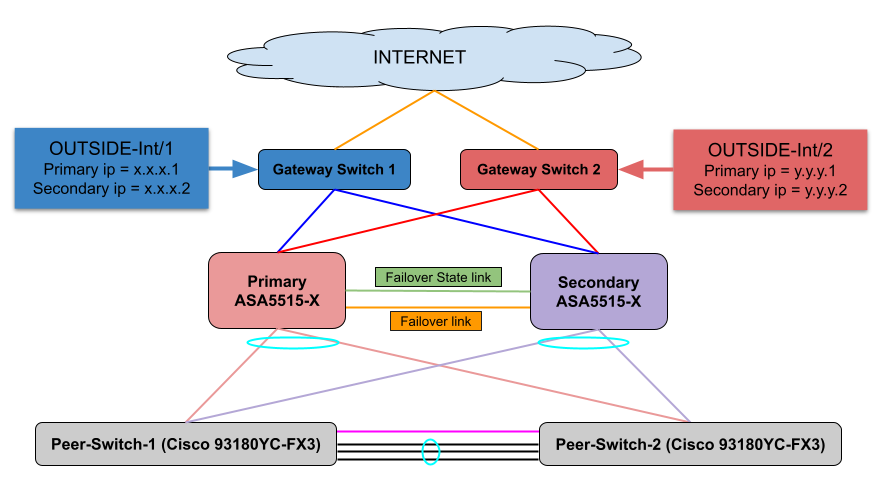
Solution 1: I will request 2 more uplink cable and cross connect. So each ipsec will be able to reach both gateway. But I have to use Active/Active because I have to configure two different interface as OUTSIDE and I have to use the 4 ip total (primary + secondary) Then I will have something like this:
PRIMARY ASA5515 device:
Outside-int1 = x.x.x.1/30
Outside-int2 = y.y.y.1/30
SECONDARY ASA5515 device:
Outside-int1 = x.x.x.2/30
Outside-int2 = y.y.y.2/30
With this setup, Failover must be able to work in my theory. What do you think?
New diagram will be like this:
Solution 2: In the case that they can't give me 2 more uplink cable, then I can not use solution 1. In this case I have to configure an internal BGP setting I guess and redirect all the traffic on that internal BGP ip.
I have 2x VPC enabled main switches (backbone) and I'm really not sure but I guess I have to create this bgp on the backbone and redirect all the traffic (inside<->out) I think this solution will work too but I don't know how to configure this setup.
What should I do ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2023 11:04 AM
Hello @Ozy,
Preference for solution 2. This solution involves implementing iBGP to manage routing and traffic redirection within your internal network. BGP can be a powerful tool for managing traffic flows and can be effective in scenarios like this.
Solution 1, using Active/Active can sometimes introduce complexity.
.ı|ı.ı|ı. If This Helps, Please Rate .ı|ı.ı|ı.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2023 12:46 PM - edited 10-01-2023 12:52 PM
I agree with you but I want to continuew with Active/Active setup because it is easier for me because I know this area but I'm not sure what to do with others.
I'm researching the solution 2 also because I only have 1 link for each gateway and 2 link total. To setup active active, I have to request 2 more link and its really hard to get new links and it take times. I was thinking solution 2 as a backup plan. But if you tell me the reasons and prove this will be better. Then I'm open to do this and learn new stuff. I only have 1 week to setup this so I'm rushing with the time also
Can we please discuss the all possible solutions in an order?
1- What should I do to achive Active/Active ? Do we need BGP at gateway side?
2- If I keep 2 links I have now. Can I setup Active/Backup setup with multi mod by using x.x.x.x/30 and y.y.y.y/30 on different interface? After failover, x.x.x.x/30 will fail on secondary device but it will continue with y.y.y.y/30. So 1 link is always failed with this solution. And I think I will need an internal failover ip as a default gateway and use this internally but redirect this to active gateway ip above ASA. Thats the part I don't know how to do
3- Not using any failover. We have to use BGP at gateway side. What we have to do at ASA layer and Backbone layer? I guess HSRP or something like this.
Lets discuss all of these by the order (logical+easy) to (logical+hard) in seperate answers.
Thank you so much for your help. You always save me my friend. You are my hero
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2023 01:03 PM - edited 10-01-2023 01:04 PM
You're so welcome @Ozy. Thanks for your kind words.
First, setting up A/A with BGP involves configuring BGP on your ASA and at the gateway side.
Configure BGP on the gateway side to handle the routing between your network and the upstream providers. Ensure BGP is set up to advertise the correct routes to both ASAs and that it can handle failover in case one ASA goes down.
BGP will handle the failover and routing between the ASAs and the gateway. BGP will automatically update routing tables based on link availability.
Setting up Active/Backup with Multi-Mode involves configuring your ASAs to use both links but prefer one over the other. You should assign a higher metric or cost to the less preferred interface to make it the backup link. Also, configure the gateway to route traffic to the ASA using both IP addresses (x.x.x.x/30 and y.y.y.y/30), and to prefer the x.x.x.x/30 link and use y.y.y.y/30 only if x.x.x.x/30 is down.
One link is prefered (Active), and traffic primarily flows through it. If that link fails, traffic is automatically redirected through the backup link (Passive).
Last scenario, BGP is used for routing without ASA failover. I think this is the least complex of the three "setups" but may not provide the same level of redundancy.
Configure BGP on the gateway to handle routing between your network and upstream providers. Advertise your network's IP ranges to the upstream providers through BGP.
This setup doesn't involve ASA failover; instead, the gateway handles routing decisions. While simpler, it may not provide the same level of failover redundancy as the previous methods.
.ı|ı.ı|ı. If This Helps, Please Rate .ı|ı.ı|ı.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2023 04:34 PM - edited 10-11-2023 06:50 PM
Canceled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2023 06:50 PM - edited 10-11-2023 08:46 PM
I couldn't get 2 more link. Solution 1 failover setup now of the table.
I started to implement the solution 2:
- I destroyed both ipsec by (write erase)
- I configured both ipsec from scratch
- I didn't setup Failover this time
- When I setup OUTSIDE interface by using 1 layer up gateway ip's I started to receive ping from outside
- I setup 2x AWS ipsec tunnel on the first ASA device. I had to setup static GW at AWS side order to skip BGP routing at my side. It worked
- I set setup second ASA with the same configuration ant it worked aswell.
Now instead of seting static GW at AWS side, I have to deal with BGP setup on my both ASA devices.
You should know that, I never configured BGP before. I know the concept but it is not enough.
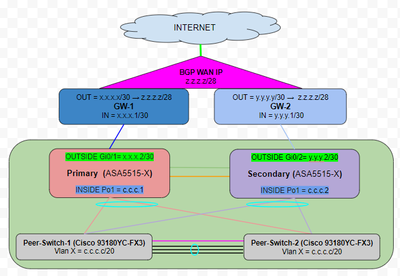
Also the BGP setup is actually 1 layer above from my ASA devices. The BGP created at Gateway1 and Gateway2 routers.
I only setup the OUTSIDE ip's as
ASA-1:(x.x.x.1) ---> GW1-router:(x.x.x.2/30)
ASA-2:(y.y.y.1) ---> GW2-router:(y.y.y.2/30)
BGP config above GW1 and GW2 and it is (z.z.z.z/28) and it includes usable 14 WAN ip's.
So currently I don't have any control over BGP network and I don't know what should I do at this point.
I started to do some research about eBGP (extarnal BGP) setup but the guides usually about creating the setup on ASA.
I have to learn how to use an outside BGP network inside the ASA.
Currently when I send a network package by using ASA-1:(x.x.x.1) or ASA-2:(y.y.y.1) one layer above, the GW's changes the package source to any of these 14 ip's from (z.z.z.z/28) network.
When the receiver tries to get back to me, it sends the answer to (z.z.z.z/28) network ofc.
But the BGP layer can not route back to the back ASA-1:(x.x.x.1) or ASA-2:(y.y.y.1) because it does not know.
So the question is, as you see as an engineer, I know the concept but at this point I don't know what should I do ? :)))))
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2023 10:02 PM - edited 10-11-2023 10:04 PM
Hello @Ozy
Could please share a draw focus on that BGP ?
But the BGP layer can not route back to the back ASA-1:(x.x.x.1) or ASA-2:(y.y.y.1) because it does not know.
It seems that ASA don't communicate subnets to BGP Gw. I'm a bit lost without a draw.
Do you check on ASAs BGP state? It should be 'Established'.
Check if ASA announce/advertise networks through BGP peer.
Some commands: https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/118050-config-bgp-00.html
Thanks a lot.
.ı|ı.ı|ı. If This Helps, Please Rate .ı|ı.ı|ı.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2023 01:54 PM - edited 10-12-2023 04:04 PM
Finally I understand the concept and created the eBGP setup from asa-1 <-> gw1 && asa-2 <-> gw2
The current configuration is below:
ASA1(config)# sh bgp summary
BGP router identifier GW1, local AS number 64717
BGP table version is 4, main routing table version 4
2 network entries using 400 bytes of memory
2 path entries using 160 bytes of memory
2/2 BGP path/bestpath attribute entries using 416 bytes of memory
1 BGP AS-PATH entries using 24 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 1000 total bytes of memory
BGP activity 2/0 prefixes, 2/0 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
GW1 4 65535 12 11 4 0 0 00:08:01 1
ASA2(config)# sh bgp summary
BGP router identifier GW2, local AS number 64717
BGP table version is 4, main routing table version 4
2 network entries using 400 bytes of memory
2 path entries using 160 bytes of memory
2/2 BGP path/bestpath attribute entries using 416 bytes of memory
1 BGP AS-PATH entries using 24 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 1000 total bytes of memory
BGP activity 2/0 prefixes, 2/0 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
GW2 4 65535 13 12 4 0 0 00:07:49 1
Now I have to research the route-map, filter list and prefix-list setup.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide