- Cisco Community
- Technology and Support
- Networking
- Routing
- GLBP virtual IP-address doesn't work
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
GLBP virtual IP-address doesn't work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2017 07:33 AM - edited 03-07-2019 12:22 AM
Hello, everybody!
I've configured GLBP between two routers (CR01 and CR02), but I can't use it's virtual IP from other router (CSW01) - so, there is no load-sharing nor redundancy. At the moment 95% of company's routing works without GLBP through CR01's physical interface and it works fine.
GLBP is configured as:
|
CR01#show glbp detail |
CR02#show glbp detail |
|
CR01#sh run | s glbp |
CR02#sh run | s glbp |
|
CR01#sh running-config interface po1.300 |
CR02#sh run int po1.300
|
On CSW01 I have:
CSW01#sh ip route vrf Border:
S* 0.0.0.0/0 [1/0] via 192.168.255.4 (It is 100% accessible from CSW01 with ping vrf Border 192.168.255.4 command)
10.0.0.0/8 is variably subnetted, 50 subnets, 4 masks
(omitted - many prefixes)
but when I trace 8.8.8.8 I get:
CSW01#traceroute vrf Border 8.8.8.8
Type escape sequence to abort.
Tracing the route to 8.8.8.8
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.255.1 0 msec 4 msec 0 msec (This is IP of Po1.300 interface of CR01)
2 x.x.x.x 0 msec 4 msec 0 msec
3 x.x.x.x 0 msec 0 msec 0 msec
4 x.x.x.x 4 msec 0 msec 0 msec
5 x.x.x.x 4 msec 0 msec 0 msec
6 x.x.x.x 4 msec 0 msec 0 msec
7 x.x.x.x 0 msec 0 msec 4 msec
8 x.x.x.x 20 msec 8 msec 20 msec
9 x.x.x.x 12 msec
10 8.8.8.8 12 msec 8 msec 8 msec
So, why CSW01 use 192.168.255.1 instead of 192.168.255.4, which is set as static next-hop for default routes?
There are some outputs below, which could be possibly useful:
CSW01#sh ip route vrf Border 192.168.255.4
Routing Table: Border
Routing entry for 192.168.255.0/29
Known via "connected", distance 0, metric 0 (connected, via interface)
Redistributing via ospf 102
Routing Descriptor Blocks:
* directly connected, via Vlan300
Route metric is 0, traffic share count is 1
CSW01#sh ip cef 192.168.255.4
192.168.255.0/29
nexthop 192.168.255.34 Vlan450
CSW01#sh ip cef vrf Border 192.168.255.4
192.168.255.4/32
attached to Vlan300
CSW01#sh ip cef 8.8.8.8
0.0.0.0/0
nexthop 192.168.255.34 Vlan450
CSW01#sh ip cef vrf Border 8.8.8.8
0.0.0.0/0
nexthop 192.168.255.4 Vlan300
I will provide all information you ask me.
Many thanks in advance,
Ilya
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2017 01:11 PM - edited 12-05-2017 01:13 PM
Hello
Your topology isnt physically correct, FHRP like glbp need to be able to send keepalive to each other, it looks like in you topology this isnt be allowed do to them not being physically connected to each other or connected by a L2 switch
The two glbp and spoke rtrs need to be on the same subnet but your topology shows the glbp rtr on different interfaces and i guess different ip addressing
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2017 02:14 PM
Hello,
in addition to Paul's remarks, post the full configuration of CSW01. We need to see how the GLBP segment/interfaces is/are connected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 12:31 AM
Hello, Gentlemen,
many thanks for your replies.
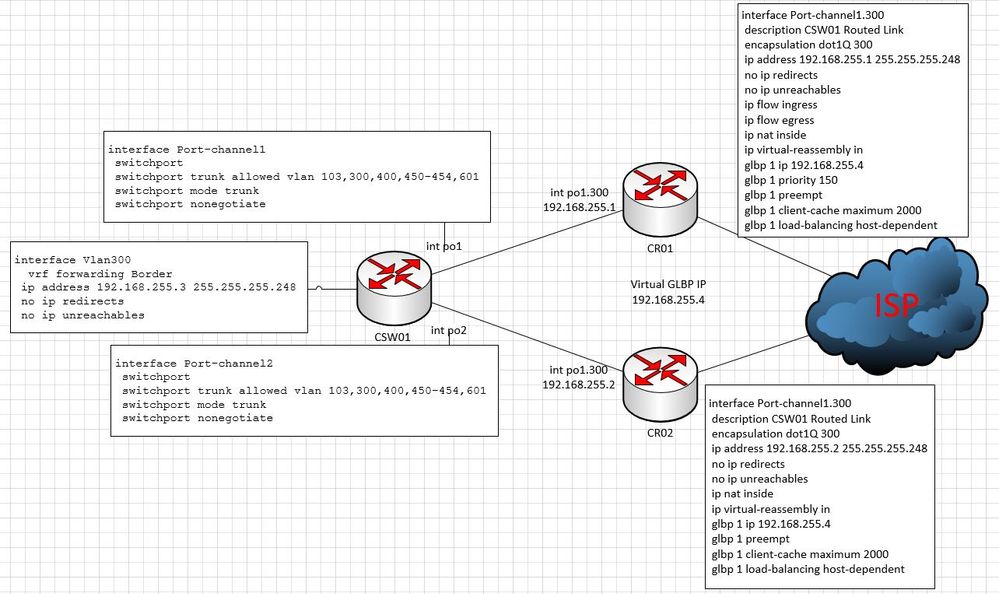
I've updated the schema for better visualization.
All the routers CSW01, CR01 and CR02 could ping these IPs 192.168.255.1, 192.168.255.2 and 192.168.255.3.
Here the full config of CSW01:
version 15.1
service compress-config
!
hostname CSW01
!
boot-start-marker
boot system flash bootflash:cat4500e-universalk9npe.SPA.03.04.00.SG.151-2.SG.bin
license boot level entservices
boot-end-marker
!
vrf definition Border
vnet tag 503
!
address-family ipv4
exit-address-family
!
vrf definition Contractor
vnet tag 504
!
address-family ipv4
exit-address-family
!
vrf definition DMZ
vnet tag 502
!
address-family ipv4
exit-address-family
!
vrf definition ForVPN
vnet tag 507
!
address-family ipv4
exit-address-family
!
vrf definition Management
vnet tag 500
!
address-family ipv4
exit-address-family
!
vrf definition Security
vnet tag 506
!
address-family ipv4
exit-address-family
!
vrf definition Servers
vnet tag 501
!
address-family ipv4
exit-address-family
!
vrf definition VoIP
vnet tag 505
!
address-family ipv4
exit-address-family
!
vrf definition Wireless
vnet tag 508
!
address-family ipv4
exit-address-family
!
vrf definition mgmtVrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
aaa session-id common
clock timezone MSK 3 0
hw-module uplink select tengigabitethernet
udld enable
no ip source-route
!
ip vrf Liin-vrf
!
no ip domain-lookup
ip domain-name banya.com
ip dhcp excluded-address 192.168.221.1 192.168.221.100
!
ip dhcp pool Temp
vrf Servers
network 192.168.221.0 255.255.255.0
dns-server 8.8.8.8
default-router 192.168.221.1
!
!
ipv6 multicast rpf use-bgp
vtp domain stobonn.com
vtp mode transparent
!
!
!
errdisable recovery cause bpduguard
errdisable recovery cause security-violation
errdisable recovery cause channel-misconfig
errdisable recovery cause pagp-flap
errdisable recovery cause dtp-flap
errdisable recovery cause link-flap
errdisable recovery cause sfp-config-mismatch
errdisable recovery cause gbic-invalid
errdisable recovery cause l2ptguard
errdisable recovery cause psecure-violation
errdisable recovery cause port-mode-failure
errdisable recovery cause mac-limit
errdisable recovery cause vmps
errdisable recovery cause storm-control
errdisable recovery cause inline-power
errdisable recovery cause arp-inspection
errdisable recovery interval 60
power redundancy-mode redundant
!
!
!
!
!
!
spanning-tree mode rapid-pvst
spanning-tree logging
spanning-tree extend system-id
spanning-tree vlan 1-4094 priority 0
!
redundancy
mode sso
!
vlan internal allocation policy ascending
!
vlan 2
!
vlan 3
!
vlan 5
!
vlan 8
!
vlan 12
!
vlan 13
!
vlan 14
!
vlan 15
!
vlan 22
!
vlan 25
!
vlan 26
!
vlan 27
!
vlan 28
!
vlan 56
!
vlan 66
!
vlan 71
!
vlan 98
!
vlan 99
!
vlan 100
!
vlan 101
!
vlan 102
!
vlan 103
!
vlan 105
!
vlan 106
!
vlan 107
!
vlan 108
!
vlan 115
!
vlan 156
!
vlan 180
!
vlan 199
!
vlan 260
!
vlan 261
!
vlan 263
!
vlan 300
name CSW01-CR Routed Link (vrf Border
!
vlan 400
!
vlan 405
!
vlan 450
name CSW01-FW01 (vrf Global)
!
vlan 451
!
vlan 452
!
vlan 453
!
vlan 454
!
vlan 455
!
vlan 456
!
vlan 457
!
vlan 458
!
vlan 459
!
vlan 600
!
vlan 601
!
vlan 700
!
vlan 701
!
vlan 702
!
vlan 800
!
vlan 801
!
vlan 802
!
vlan 803
!
vlan 804
!
vlan 805
!
vlan 806
!
vlan 807
!
vlan 911
!
vlan 1100
!
vlan 2000
!
vlan 2001
!
vlan 2002
!
vlan 2003
!
vlan 2005
!
vlan 2007
!
vlan 2100
!
vlan 3000
!
vlan 4044
!
vlan 4045
!
vlan 4052
!
vlan 4053
!
vlan 4056
!
vlan 4060
lldp run
!
interface Loopback199
vrf forwarding Management
ip address 192.168.200.1 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback201
ip address 10.255.1.1 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback202
vrf forwarding Management
ip address 10.255.1.2 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback203
vrf forwarding Servers
ip address 10.255.1.3 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback204
vrf forwarding DMZ
ip address 10.255.1.4 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback205
vrf forwarding Border
ip address 10.255.1.5 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback206
vrf forwarding Contractor
ip address 10.255.1.6 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback207
vrf forwarding VoIP
ip address 10.255.1.10 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback208
vrf forwarding ForVPN
ip address 10.255.1.14 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback209
vrf forwarding Security
ip address 10.255.1.20 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback210
vrf forwarding Wireless
ip address 10.1.255.30 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Port-channel1
switchport
switchport trunk allowed vlan 103,300,400,450-454,601
switchport mode trunk
switchport nonegotiate
!
interface Port-channel2
switchport
switchport trunk allowed vlan 103,300,400,450-455,601
switchport mode trunk
switchport nonegotiate
!
interface Port-channel3
switchport
switchport trunk allowed vlan 3,99,100,103,107,199,263,800,2100,3000
switchport mode trunk
!
interface Port-channel4
switchport
switchport mode trunk
switchport nonegotiate
!
interface Port-channel5
switchport
switchport trunk allowed vlan 1,3,100,180,199,3000
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface Port-channel6
switchport
switchport mode trunk
!
interface Port-channel7
switchport
switchport trunk allowed vlan 99,100,103,2100
switchport mode trunk
!
interface Port-channel8
switchport
switchport access vlan 3
switchport trunk allowed vlan 100,800
switchport mode trunk
!
interface Port-channel9
switchport
switchport trunk allowed vlan 28,56,71,98,107,156,260,261,450-459,2001,2100
switchport mode trunk
switchport nonegotiate
bandwidth 1500
!
interface Port-channel10
switchport
switchport trunk allowed vlan 28,56,71,98,107,156,260,261,450-459,2001,2100
switchport mode trunk
switchport nonegotiate
!
interface Port-channel11
switchport
switchport access vlan 600
switchport mode access
switchport nonegotiate
!
interface Port-channel12
switchport
switchport access vlan 600
switchport mode access
switchport nonegotiate
!
interface Port-channel13
switchport
switchport trunk allowed vlan 3,199,702,801,1100,2002-2004,2100
switchport mode trunk
!
interface Port-channel14
switchport
switchport mode trunk
!
interface FastEthernet1
vrf forwarding mgmtVrf
no ip address
speed auto
duplex auto
!
interface GigabitEthernet1/1
switchport trunk allowed vlan 1-198,200-4094
switchport mode trunk
switchport nonegotiate
spanning-tree bpduguard disable
!
interface GigabitEthernet1/2
switchport access vlan 2
switchport trunk allowed vlan 2,199
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet1/3
switchport trunk allowed vlan 66,103,156,199,801
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet1/4
switchport trunk allowed vlan 1,15,27,199,801
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet1/5
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet1/6
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet1/7
switchport trunk allowed vlan 199,801,2007
switchport mode trunk
!
interface GigabitEthernet1/8
switchport trunk allowed vlan 3,199,702,801,1100,2002-2004,2100
switchport mode trunk
channel-group 13 mode active
!
interface GigabitEthernet1/9
switchport trunk allowed vlan 199,801,911
switchport mode trunk
!
interface GigabitEthernet1/10
switchport mode trunk
channel-group 6 mode active
!
interface GigabitEthernet1/11
switchport access vlan 103
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet1/12
switchport access vlan 100
switchport mode access
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet2/1
switchport trunk allowed vlan 1-99,101-198,200-4094
switchport mode trunk
switchport nonegotiate
spanning-tree bpduguard disable
!
interface GigabitEthernet2/2
switchport trunk allowed vlan 1,15,22,105-108,156,199,804,4044,4045,4056
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet2/3
switchport trunk allowed vlan 22,108,156,199
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet2/4
switchport trunk allowed vlan 2,14,22,199,4052,4053,4060
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet2/5
switchport trunk allowed vlan 2,199,2001
switchport mode trunk
!
interface GigabitEthernet2/6
!
interface GigabitEthernet2/7
!
interface GigabitEthernet2/8
switchport trunk allowed vlan 3,199,702,801,1100,2002-2004,2100
switchport mode trunk
channel-group 13 mode active
!
interface GigabitEthernet2/9
switchport access vlan 108
switchport mode access
no lldp transmit
no cdp enable
spanning-tree bpdufilter enable
spanning-tree bpduguard disable
!
interface GigabitEthernet2/10
!
interface GigabitEthernet2/11
switchport access vlan 107
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet2/12
switchport access vlan 100
switchport mode access
!
interface TenGigabitEthernet3/1
no switchport
vnet trunk
ip address 192.168.255.17 255.255.255.252
!
interface TenGigabitEthernet3/2
!
interface GigabitEthernet3/3
!
interface GigabitEthernet3/4
!
interface GigabitEthernet3/5
!
interface GigabitEthernet3/6
!
interface TenGigabitEthernet4/1
no switchport
vnet trunk
ip address 192.168.255.21 255.255.255.252
!
interface TenGigabitEthernet4/2
!
interface GigabitEthernet4/3
!
interface GigabitEthernet4/4
!
interface GigabitEthernet4/5
!
interface GigabitEthernet4/6
!
interface GigabitEthernet5/1
switchport access vlan 22
switchport trunk allowed vlan 22,199
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet5/2
switchport access vlan 3
switchport mode access
switchport nonegotiate
switchport voice vlan 801
!
interface GigabitEthernet5/3
switchport access vlan 100
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/4
switchport access vlan 100
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/5
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/6
switchport trunk allowed vlan 2002,2003,2100
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet5/7
switchport trunk allowed vlan 3,199,801
switchport mode trunk
!
interface GigabitEthernet5/8
switchport mode trunk
shutdown
channel-group 14 mode desirable
!
interface GigabitEthernet5/9
switchport access vlan 100
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/10
switchport access vlan 100
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/11
switchport access vlan 100
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/12
switchport access vlan 3
switchport trunk allowed vlan 100,800
switchport mode trunk
channel-group 8 mode active
spanning-tree bpdufilter enable
!
interface GigabitEthernet5/13
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/14
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/15
switchport trunk allowed vlan 3,99,100,103,107,199,263,800,2100,3000
switchport mode trunk
channel-group 3 mode active
!
interface GigabitEthernet5/16
switchport trunk allowed vlan 3,99,100,103,107,199,263,800,2100,3000
switchport mode trunk
channel-group 3 mode active
!
interface GigabitEthernet5/17
switchport access vlan 701
switchport mode access
switchport nonegotiate
spanning-tree bpdufilter enable
!
interface GigabitEthernet5/18
switchport access vlan 702
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/19
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/20
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/21
switchport trunk allowed vlan 1,3,100,180,199,3000
switchport mode trunk
switchport nonegotiate
channel-group 5 mode active
!
interface GigabitEthernet5/22
switchport trunk allowed vlan 1,3,100,180,199,3000
switchport mode trunk
switchport nonegotiate
channel-group 5 mode active
!
interface GigabitEthernet5/23
switchport mode trunk
switchport nonegotiate
channel-group 4 mode active
!
interface GigabitEthernet5/24
switchport mode trunk
switchport nonegotiate
channel-group 4 mode active
!
interface GigabitEthernet5/25
switchport access vlan 100
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/26
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/27
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/28
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/29
switchport access vlan 700
switchport mode access
switchport nonegotiate
spanning-tree bpdufilter enable
!
interface GigabitEthernet5/30
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/31
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/32
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/33
description USER
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/34
switchport access vlan 700
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/35
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/36
switchport trunk allowed vlan 99,100,103,2100
switchport mode trunk
channel-group 7 mode active
!
interface GigabitEthernet5/37
switchport access vlan 100
switchport mode access
!
interface GigabitEthernet5/38
switchport trunk allowed vlan 1-199,801-807,1100
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet5/39
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet5/40
switchport trunk allowed vlan 103,300,400,450-454,601
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
!
interface GigabitEthernet5/41
switchport trunk allowed vlan 103,300,400,450-455,601
switchport mode trunk
switchport nonegotiate
channel-group 2 mode on
!
interface GigabitEthernet5/42
switchport access vlan 199
!
interface GigabitEthernet5/43
switchport access vlan 600
switchport mode access
switchport nonegotiate
channel-group 11 mode active
!
interface GigabitEthernet5/44
switchport access vlan 600
switchport mode access
switchport nonegotiate
channel-group 12 mode active
!
interface GigabitEthernet5/45
switchport trunk allowed vlan 28,56,71,98,107,156,260,261,450-459,2001,2100
switchport mode trunk
switchport nonegotiate
channel-group 10 mode active
spanning-tree bpdufilter enable
spanning-tree bpduguard disable
!
interface GigabitEthernet5/46
switchport trunk allowed vlan 28,56,71,98,107,156,260,261,450-459,2001,2100
switchport mode trunk
switchport nonegotiate
channel-group 10 mode active
spanning-tree bpdufilter enable
spanning-tree bpduguard disable
!
interface GigabitEthernet5/47
switchport trunk allowed vlan 28,56,71,98,107,156,260,261,450-459,2001,2100
switchport mode trunk
switchport nonegotiate
channel-group 9 mode active
!
interface GigabitEthernet5/48
switchport trunk allowed vlan 28,56,71,98,107,156,260,261,450-459,2001,2100
switchport mode trunk
switchport nonegotiate
channel-group 9 mode active
!
interface GigabitEthernet6/1
switchport access vlan 801
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/2
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/3
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/4
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/5
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/6
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/7
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/8
switchport mode trunk
shutdown
channel-group 14 mode desirable
!
interface GigabitEthernet6/9
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/10
switchport access vlan 103
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/11
switchport access vlan 3
switchport mode access
switchport nonegotiate
switchport voice vlan 801
!
interface GigabitEthernet6/12
switchport access vlan 3
switchport trunk allowed vlan 100,800
switchport mode trunk
channel-group 8 mode active
spanning-tree bpdufilter enable
!
interface GigabitEthernet6/13
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/14
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/15
switchport trunk allowed vlan 3,99,100,103,107,199,263,800,2100,3000
switchport mode trunk
channel-group 3 mode active
!
interface GigabitEthernet6/16
switchport trunk allowed vlan 3,99,100,103,107,199,263,800,2100,3000
switchport mode trunk
channel-group 3 mode active
!
interface GigabitEthernet6/17
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/18
switchport access vlan 14
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/19
!
interface GigabitEthernet6/20
switchport trunk allowed vlan 1,3,14,99,156,199,801,1100
switchport mode trunk
switchport nonegotiate
spanning-tree bpdufilter disable
spanning-tree bpduguard disable
!
interface GigabitEthernet6/21
switchport trunk allowed vlan 1,3,100,180,199,3000
switchport mode trunk
switchport nonegotiate
channel-group 5 mode active
!
interface GigabitEthernet6/22
switchport trunk allowed vlan 1,3,100,180,199,3000
switchport mode trunk
switchport nonegotiate
channel-group 5 mode active
!
interface GigabitEthernet6/23
switchport mode trunk
switchport nonegotiate
channel-group 4 mode active
!
interface GigabitEthernet6/24
switchport mode trunk
switchport nonegotiate
channel-group 4 mode active
!
interface GigabitEthernet6/25
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/26
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/27
switchport access vlan 2
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/28
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/29
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/30
description USER
switchport access vlan 3
switchport mode access
switchport nonegotiate
switchport voice vlan 801
!
interface GigabitEthernet6/31
description USER
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/32
description USER
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/33
description ACRIBIA-Kontinent
switchport access vlan 103
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/34
description ACRIBIA-Kontinent
switchport access vlan 103
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/35
description USER
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/36
switchport trunk allowed vlan 99,100,103,2100
switchport mode trunk
channel-group 7 mode active
!
interface GigabitEthernet6/37
description USER
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/38
description USER
switchport access vlan 3
switchport mode access
switchport nonegotiate
!
interface GigabitEthernet6/39
description dlink-voice-router
switchport access vlan 3
switchport mode access
switchport nonegotiate
switchport voice vlan 801
!
interface GigabitEthernet6/40
description CR01 Gi0/4
switchport trunk allowed vlan 103,300,400,450-454,601
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
!
interface GigabitEthernet6/41
description CR02 Gi0/4
switchport trunk allowed vlan 103,300,400,450-455,601
switchport mode trunk
switchport nonegotiate
channel-group 2 mode on
!
!
interface Vlan1
ip address 192.168.1.1 255.255.255.0
no ip redirects
no ip unreachables
!
interface Vlan2
ip address 192.168.2.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
no ip route-cache
!
interface Vlan3
ip address 192.168.3.1 255.255.255.0
!
interface Vlan5
ip address 192.168.5.1 255.255.255.0
ip helper-address 192.168.100.3
!
interface Vlan8
ip address 192.168.8.1 255.255.255.0
!
interface Vlan12
ip address 192.168.12.1 255.255.255.0
!
interface Vlan15
ip address 192.168.15.1 255.255.255.0
!
interface Vlan22
ip address 192.168.22.1 255.255.255.0
!
interface Vlan25
ip address 192.168.25.1 255.255.255.0
!
interface Vlan26
ip address 192.168.26.1 255.255.255.0
!
interface Vlan27
ip address 192.168.27.1 255.255.255.0
ip helper-address 192.168.100.2
ip helper-address 192.168.100.3
no ip redirects
no ip unreachables
!
interface Vlan66
ip address 192.168.66.1 255.255.255.0
!
interface Vlan99
ip address 192.168.99.1 255.255.255.0
!
interface Vlan100
vrf forwarding Servers
ip address 192.168.100.248 255.255.255.0
no ip redirects
no ip unreachables
standby 100 ip 192.168.100.1
standby 100 timers msec 250 1
standby 100 priority 255
standby 100 preempt
!
interface Vlan102
vrf forwarding DMZ
ip address 192.168.102.1 255.255.255.0
no ip redirects
no ip unreachables
!
interface Vlan105
ip address 192.168.111.1 255.255.255.0
no ip redirects
no ip unreachables
!
interface Vlan110
no ip address
shutdown
!
interface Vlan180
ip address 192.168.180.1 255.255.255.0
ip helper-address 192.168.100.2
ip helper-address 192.168.100.3
no ip redirects
no ip unreachables
!
interface Vlan199
vrf forwarding Management
ip address 192.168.201.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan263
bandwidth 4000
ip address 192.168.255.197 255.255.255.252
!
interface Vlan300
vrf forwarding Border
ip address 192.168.255.3 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan400
vrf forwarding Management
ip address 192.168.255.11 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan450
ip address 192.168.255.33 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan451
vrf forwarding Management
ip address 192.168.255.41 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan452
vrf forwarding Servers
ip address 192.168.255.49 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan453
vrf forwarding DMZ
ip address 192.168.255.57 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan454
vrf forwarding Border
ip address 192.168.255.65 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan455
vrf forwarding Contractor
ip address 192.168.255.169 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan456
vrf forwarding VoIP
ip address 172.29.255.33 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan457
vrf forwarding ForVPN
ip address 192.168.255.202 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan458
vrf forwarding Security
ip address 192.168.255.210 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan459
vrf forwarding Wireless
ip address 192.168.255.218 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan700
vrf forwarding ForVPN
ip address 10.128.1.1 255.255.255.240
no ip redirects
no ip unreachables
!
interface Vlan701
vrf forwarding ForVPN
ip address 10.128.1.17 255.255.255.240
no ip redirects
no ip unreachables
!
interface Vlan702
vrf forwarding ForVPN
ip address 10.128.1.33 255.255.255.248
no ip redirects
no ip unreachables
!
interface Vlan800
vrf forwarding VoIP
ip address 172.29.250.1 255.255.255.0
no ip redirects
no ip unreachables
!
interface Vlan801
vrf forwarding VoIP
ip address 172.29.0.1 255.255.240.0
no ip redirects
no ip unreachables
!
interface Vlan911
vrf forwarding Security
ip address 192.168.112.1 255.255.255.0
ip helper-address global 192.168.100.2
ip helper-address global 192.168.100.3
no ip redirects
no ip unreachables
!
interface Vlan1100
vrf forwarding Wireless
ip address 192.168.110.1 255.255.255.0
ip helper-address 192.168.100.2
ip helper-address 192.168.100.3
no ip redirects
no ip unreachables
!
interface Vlan2007
ip address 172.30.7.1 255.255.255.0
no ip redirects
no ip unreachables
!
interface Vlan4044
ip address 192.168.255.89 255.255.255.252
no ip redirects
no ip unreachables
!
interface Vlan4045
vrf forwarding Management
ip address 192.168.255.93 255.255.255.252
no ip redirects
no ip unreachables
!
interface Vlan4052
ip address 192.168.255.141 255.255.255.252
no ip redirects
no ip unreachables
!
interface Vlan4053
vrf forwarding Management
ip address 192.168.255.161 255.255.255.252
no ip redirects
no ip unreachables
!
interface Vlan4056
vrf forwarding VoIP
ip address 172.29.255.9 255.255.255.252
no ip redirects
no ip unreachables
!
interface Vlan4060
vrf forwarding VoIP
ip address 172.29.255.25 255.255.255.252
no ip redirects
no ip unreachables
!
router ospf 101 vrf Management
router-id 10.255.1.2
capability vrf-lite
redistribute connected subnets
network 192.168.255.0 0.0.0.255 area 101
!
router ospf 102 vrf Border
router-id 10.255.1.5
capability vrf-lite
redistribute connected subnets
network 192.168.255.0 0.0.0.255 area 102
!
router ospf 103 vrf DMZ
router-id 10.255.1.4
capability vrf-lite
redistribute connected subnets
network 192.168.255.0 0.0.0.255 area 103
!
router ospf 105 vrf Servers
router-id 10.255.1.3
capability vrf-lite
redistribute connected subnets
redistribute static subnets
network 192.168.255.0 0.0.0.255 area 105
!
router ospf 106 vrf Contractor
router-id 10.255.1.6
capability vrf-lite
redistribute connected subnets
network 192.168.255.0 0.0.0.255 area 106
!
router ospf 107 vrf VoIP
router-id 10.255.1.10
capability vrf-lite
redistribute connected subnets
network 172.29.255.0 0.0.0.255 area 107
network 192.168.255.0 0.0.0.255 area 107
!
router ospf 108 vrf ForVPN
router-id 10.255.1.14
capability vrf-lite
redistribute connected subnets
redistribute static subnets
network 10.128.1.0 0.0.0.255 area 108
network 192.168.255.0 0.0.0.255 area 108
!
router ospf 109 vrf Security
router-id 10.255.1.20
capability vrf-lite
redistribute connected
network 192.168.112.0 0.0.0.255 area 109
network 192.168.255.0 0.0.0.255 area 109
!
router ospf 110 vrf Wireless
router-id 10.255.1.30
capability vrf-lite
redistribute connected subnets
redistribute static subnets
network 192.168.110.0 0.0.0.255 area 110
network 192.168.255.0 0.0.0.255 area 110
!
router ospf 100
router-id 10.255.1.1
redistribute connected subnets
redistribute static subnets
network 192.168.255.0 0.0.0.255 area 0
!
ip http server
ip http authentication local
no ip http secure-server
!
ip route 192.168.0.0 255.255.255.0 192.168.156.254
ip route 192.168.72.0 255.255.255.0 192.168.111.254
ip route 192.168.75.0 255.255.255.0 192.168.111.254
ip route 192.168.76.0 255.255.255.0 192.168.111.254
ip route 192.168.79.0 255.255.255.0 192.168.111.254
ip route 192.168.106.0 255.255.255.0 192.168.111.254
ip route vrf Border 0.0.0.0 0.0.0.0 192.168.255.4
!
!
!
ip prefix-list REDIST_LOCAL seq 10 permit 192.168.0.0/16 le 32
logging trap notifications
logging source-interface Loopback199 vrf Management
logging host 192.168.100.251 vrf Management
!
route-map RM_REDIST_LOCAL permit 10
match ip address prefix-list REDIST_LOCAL
!
snmp-server community public RO
!
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 01:38 AM
Hello,
I need to lab this, but check the channel group numbering:
CR02#sh run int po1.300
Building configuration...
Current configuration : 324 bytes
!
interface Port-channel1.300
On CSW01, you have configured channel group 2 for the trunk to CR02. I think the numbers have to match, so try:
interface Port-channel2.300
Can you actually ping CSW01 from CR01 (using the 192.168.255.2 address as the source) ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 03:00 AM - edited 12-06-2017 03:00 AM
Hi, Georg,
At CSW01 side to CR01 connects Port-Channel1 interface, to CR02 - Port-Channel2.
Do you really insist to rename both interfaces on CSW01 to match with CR01&CR02? It is impossible to do during workhours and workdays, I need request a maintainance window.
Here the output you've requested:
CR01#Ping 192.168.255.3 source 192.168.255.2
% Invalid source address- IP address not on any of our up interfaces
I've also added this:
CR01#Ping 192.168.255.3 source 192.168.255.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.255.3, timeout is 2 seconds:
Packet sent with a source address of 192.168.255.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/6 ms
CR01#
Thank you very much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 04:03 AM
Hello,
don't change anything, I'll lab this first...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 10:50 AM - edited 12-06-2017 01:24 PM
Hello
Its a quite convoluted configuration - However i don't seem to see the default being directed towards the global rib table and also any statement telling the same rtr where to go for the return path for network192.168.255.0/29 into the vrf.
Can you trying adding this please:
ip route vrf Border 0.0.0.0 0.0.0.0 192.168.255.4 global
ip route 192.168.255.0 255.255.255.248 vlan 300
rtr1-2
interface Port-channel1.300
glbp 1 load-balancing round-robin
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 02:49 PM
What I meant was:
CR01#Ping 192.168.255.2 source 192.168.255.1
That is CR01 to CR02...
Either way, I recreated the setup without the VRF, which works. I know you cannot do a lot of testing, but if possible try and configure just the bare minimum to start out with and see if you get it to work.
CR01#sh run | s glbp
glbp 1 ip 192.168.255.4
CR02#sh run | s glbp
glbp 1 ip 192.168.255.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 11:59 AM
Hello,
post the full configs of CR01 and CR02 as well...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 12:57 PM
Evening, Georg,
May I ask you? Should I see Virtual GLBP address in trace output? When I trace something beyond the GLBP routers...? I ask because I've configured a small lab in GNS and don't see Virtual address in trace.
Full show-runs from CR01 and CR02 below. Many thanks to you.
CR01:
version 15.1
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime
service timestamps log datetime msec localtime
service password-encryption
!
hostname CR01
!
vrf definition Management
!
address-family ipv4
exit-address-family
!
no ipv6 cef
no ip source-route
!
ip cef
!
no ip bootp server
no ip domain lookup
ip domain name ashipyards.com
multilink bundle-name authenticated
!
crypto pki token default removal timeout 0
!
license udi pid C3900-SPE200/K9
!
interface Loopback199
vrf forwarding Management
ip address 192.168.200.254 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback201
ip address 10.255.254.5 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback202
vrf forwarding Management
ip address 10.255.254.2 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Port-channel1
no ip address
hold-queue 150 in
!
interface Port-channel1.103
encapsulation dot1Q 103
ip address x.x.x.x 255.255.255.248
ip nat outside
ip virtual-reassembly in
!
interface Port-channel1.300
encapsulation dot1Q 300
ip address 192.168.255.1 255.255.255.248
no ip redirects
no ip unreachables
ip flow ingress
ip flow egress
ip nat inside
ip virtual-reassembly in
glbp 1 ip 192.168.255.4
glbp 1 priority 150
glbp 1 preempt
glbp 1 client-cache maximum 2000
glbp 1 load-balancing host-dependent
!
interface Port-channel1.400
encapsulation dot1Q 400
vrf forwarding Management
ip address 192.168.255.9 255.255.255.248
no ip redirects
no ip unreachables
!
interface Port-channel1.601
encapsulation dot1Q 601
ip address 192.168.255.146 255.255.255.248
no ip redirects
no ip unreachables
standby delay minimum 20 reload 20
standby version 2
standby 254 ip 192.168.255.145
standby 254 priority 255
standby 254 preempt delay minimum 20 reload 20 sync 10
standby 254 name HSRP_NAT
!
interface Port-channel1.603
!
interface GigabitEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
channel-group 1
!
interface GigabitEthernet0/3
no ip address
duplex auto
speed auto
channel-group 1
!
router ospf 101 vrf Management
router-id 10.255.254.2
capability vrf-lite
redistribute connected subnets
network 192.168.255.0 0.0.0.255 area 101
!
router ospf 102
router-id 10.255.254.5
redistribute connected subnets
redistribute static subnets
network 192.168.255.0 0.0.0.255 area 102
default-information originate metric 10
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
ip flow-export source Loopback199
ip flow-export version 5
ip flow-export destination 192.168.100.250 9997 vrf Management
!
ip nat Stateful id 1
redundancy HSRP_NAT
mapping-id 10
mapping-id 20
protocol udp
ip nat translation timeout 600
ip nat translation tcp-timeout 400
ip nat translation udp-timeout 30
ip nat translation finrst-timeout 30
ip nat translation syn-timeout 30
ip nat translation dns-timeout 30
ip nat translation icmp-timeout 5
ip nat translation port-timeout tcp 80 20
ip nat translation max-entries all-host 400
ip nat translation max-entries host 192.168.100.2 15000
ip nat translation max-entries host 192.168.100.3 15000
ip nat translation max-entries host 192.168.100.56 15000
ip nat translation max-entries host 192.168.100.90 20000
ip nat translation max-entries host 192.168.55.5 8000
ip nat translation max-entries host 192.168.55.3 5000
ip nat translation max-entries host 192.168.100.83 20000
ip nat translation max-entries host 192.168.3.235 2000
ip nat pool NAT-POOL x.x.x.x x.x.x.x prefix-length 29
ip nat pool SERVERS x.x.x.x x.x.x.x prefix-length 29
ip nat inside source route-map NAT-POOL pool NAT-POOL mapping-id 10 overload
ip nat inside source route-map SERVERS pool SERVERS mapping-id 20 overload
ip nat inside source static tcp 192.168.100.90 25 x.x.x.x 25 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static tcp 192.168.100.90 443 x.x.x.x 443 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static tcp 192.168.100.90 465 x.x.x.x 465 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static udp 192.168.255.66 2020 x.x.x.x 2020 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static udp 192.168.255.66 2021 x.x.x.x 2021 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static tcp 192.168.71.12 5555 x.x.x.x 5555 redundancy HSRP_NAT mapping-id 10 extendable
ip nat inside source static 172.29.250.2 x.x.x.x
ip route 0.0.0.0 0.0.0.0 x.x.x.x
!
ip access-list standard ACL_NTP_CLIENT
permit 192.168.0.0 0.0.255.255
permit 10.0.0.0 0.255.255.255
!
ip access-list extended acl_local_nat
deny ip 192.168.100.0 0.0.0.255 any
permit ip 192.168.0.0 0.0.255.255 any
deny ip any any
ip access-list extended acl_local_servers
permit ip 192.168.100.0 0.0.0.255 any
permit ip host 172.30.100.5 any
permit ip host 172.30.100.4 any
deny ip any any
ip access-list extended acl_local_smtp
permit ip host 192.168.100.72 any
permit ip host 192.168.100.55 any
permit ip 192.168.100.0 0.0.0.255 any
ip access-list extended acl_nat_mail
permit ip host 192.168.100.90 any
permit ip host 192.168.100.52 any
ip access-list extended acl_voip_servers
permit ip host 172.29.250.2 any
permit ip host 172.29.250.3 any
deny ip any any
!
logging trap notifications
logging source-interface Loopback199 vrf Management
logging host 192.168.100.251 vrf Management
access-list 99 permit 192.168.0.0 0.0.255.255
access-list 99 deny any log
!
route-map VOIP permit 30
match ip address acl_voip_servers
set ip next-hop x.x.x.x
!
route-map SERVERS permit 20
match ip address acl_local_servers
!
route-map NAT-POOL permit 10
match ip address acl_local_nat
!
control-plane
!
CR02:
version 15.1
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname CR02
!
vrf definition Backup
!
address-family ipv4
exit-address-family
!
vrf definition Management
!
address-family ipv4
exit-address-family
!
aaa session-id common
clock timezone MSK 4 0
!
no ipv6 cef
no ip source-route
!
ip cef
!
crypto pki token default removal timeout 0
!
license udi pid C3900-SPE200/K9
!
interface Loopback199
vrf forwarding Management
ip address 192.168.200.253 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback201
ip address 10.255.253.5 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback202
vrf forwarding Management
ip address 10.255.253.2 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Loopback254
vrf forwarding Backup
ip address 10.255.253.254 255.255.255.255
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Port-channel1
no ip address
hold-queue 150 in
!
interface Port-channel1.103
encapsulation dot1Q 103
ip address x.x.x.x 255.255.255.248
ip nat outside
ip virtual-reassembly in
!
interface Port-channel1.300
encapsulation dot1Q 300
ip address 192.168.255.2 255.255.255.248
no ip redirects
no ip unreachables
ip nat inside
ip virtual-reassembly in
!
interface Port-channel1.400
encapsulation dot1Q 400
vrf forwarding Management
ip address 192.168.255.10 255.255.255.248
no ip redirects
no ip unreachables
!
interface Port-channel1.450
bandwidth 1000
encapsulation dot1Q 450
vrf forwarding Backup
ip address 192.168.255.36 255.255.255.248
delay 100000
!
interface Port-channel1.451
bandwidth 1000
encapsulation dot1Q 451
vrf forwarding Backup
ip address 192.168.255.44 255.255.255.248
delay 101000
!
interface Port-channel1.452
bandwidth 1000
encapsulation dot1Q 452
vrf forwarding Backup
ip address 192.168.255.52 255.255.255.248
delay 102000
!
interface Port-channel1.453
bandwidth 1000
encapsulation dot1Q 453
vrf forwarding Backup
ip address 192.168.255.60 255.255.255.248
delay 103000
!
interface Port-channel1.454
bandwidth 1000
encapsulation dot1Q 454
vrf forwarding Backup
ip address 192.168.255.68 255.255.255.248
delay 104000
!
interface Port-channel1.455
bandwidth 1000
delay 105000
!
interface Port-channel1.601
encapsulation dot1Q 601
ip address 192.168.255.147 255.255.255.248
no ip redirects
no ip unreachables
ip nat inside
ip virtual-reassembly in
standby delay minimum 20 reload 20
standby version 2
standby 254 ip 192.168.255.145
standby 254 priority 0
standby 254 preempt delay minimum 20 reload 20 sync 10
standby 254 name HSRP_NAT
!
interface GigabitEthernet0/0
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
channel-group 1
!
interface GigabitEthernet0/3
no ip address
duplex auto
speed auto
channel-group 1
!
router eigrp 100
!
address-family ipv4 vrf Management autonomous-system 100
redistribute connected
network 192.168.255.0
eigrp router-id 10.255.253.2
exit-address-family
!
address-family ipv4 vrf Backup autonomous-system 100
redistribute connected
network 192.168.255.0
eigrp router-id 10.255.253.254
exit-address-family
network 192.168.255.0
redistribute connected metric 1000 1000000 255 255 255
redistribute static metric 1000 1000000 255 255 255
eigrp router-id 10.255.253.5
!
router ospf 101 vrf Management
router-id 10.255.253.2
capability vrf-lite
redistribute connected subnets
network 192.168.255.0 0.0.0.255 area 101
!
router ospf 102 vrf Backup
router-id 10.255.253.254
capability vrf-lite
network 192.168.255.36 0.0.0.0 area 0
network 192.168.255.44 0.0.0.0 area 101
network 192.168.255.52 0.0.0.0 area 105
network 192.168.255.60 0.0.0.0 area 103
network 192.168.255.68 0.0.0.0 area 102
!
router ospf 100
router-id 10.255.253.5
redistribute connected metric 50 subnets
redistribute static metric 50 subnets
passive-interface Port-channel1.601
network 192.168.255.2 0.0.0.0 area 102
network 192.168.255.0 0.0.0.255 area 0
default-information originate metric 50
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip nat Stateful id 2
redundancy HSRP_NAT
mapping-id 20
mapping-id 10
protocol udp
ip nat translation timeout 600
ip nat translation tcp-timeout 400
ip nat translation udp-timeout 30
ip nat translation syn-timeout 120
ip nat translation dns-timeout 30
ip nat translation icmp-timeout 5
ip nat translation max-entries all-host 1000
ip nat translation max-entries host 192.168.100.2 15000
ip nat translation max-entries host 192.168.100.3 15000
ip nat translation max-entries host 192.168.100.56 15000
ip nat translation max-entries host 192.168.100.90 20000
ip nat translation max-entries host 192.168.55.5 8000
ip nat translation max-entries host 192.168.55.3 5000
ip nat translation max-entries host 192.168.100.83 20000
ip nat translation max-entries host 192.168.3.235 2000
ip nat pool NAT-POOL x.x.x.x x.x.x.x prefix-length 29
ip nat pool SERVERS x.x.x.x x.x.x.x prefix-length 29
ip nat inside source route-map LOCAL-NAT pool NAT-POOL mapping-id 10 overload
ip nat inside source route-map NAT-MAIL pool NAT-POOL mapping-id 10 overload
ip nat inside source route-map SERVERS pool SERVERS mapping-id 20 overload
ip nat inside source static tcp 192.168.100.90 25 x.x.x.x 25 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static tcp 192.168.100.90 443 x.x.x.x 443 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static tcp 192.168.100.90 465 x.x.x.x 465 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static udp 192.168.255.66 2020 x.x.x.x 2020 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static udp 192.168.255.66 2021 x.x.x.x 2021 redundancy HSRP_NAT mapping-id 20 extendable
ip nat inside source static tcp 192.168.71.12 5555 x.x.x.x 5555 redundancy HSRP_NAT mapping-id 10 extendable
ip route 0.0.0.0 0.0.0.0 x.x.x.x
!
ip access-list standard ACL_NTP_CLIENT
permit 192.168.0.0 0.0.255.255
permit 10.0.0.0 0.255.255.255
!
ip access-list extended acl_local_nat
deny ip 192.168.100.0 0.0.0.255 any
permit ip 192.168.0.0 0.0.255.255 any
deny ip any any
ip access-list extended acl_local_servers
permit ip 192.168.100.0 0.0.0.255 any
deny ip any any
ip access-list extended acl_nat_mail
permit ip host 192.168.100.90 any
permit ip host 192.168.100.52 any
permit ip host 192.168.100.54 any
!
logging trap notifications
logging source-interface Loopback199 vrf Management
logging host 192.168.100.251 vrf Management
access-list 99 permit 192.168.0.0 0.0.255.255
access-list 99 deny any log
!
route-map RM_REDIST_LOCAL_BACKUP permit 10
set metric +1000000
!
route-map LOCAL-NAT permit 30
match ip address acl_local_nat
!
route-map SERVERS permit 20
match ip route-source acl_local_servers
!
route-map NAT-MAIL permit 10
match ip address acl_local_nat
!
!
control-plane
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2017 05:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2017 06:47 AM
Hello, Joseph,
many thanks for your reply.
So, you mean that GPLB is not a proper solution in my case? Then, what else?
OSPF maximum-paths?
My primary goal is to provide load balancing and fault-tolerance for Internet connection. I have 2 ISPs...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2017 08:10 AM
One method would be to run a dynamic routing protocol between the 3 devices, and have CR01 and CR02 as equal cost from CSW01.
Another method (similar to your GLBP approach), would be to use mHSRP on CR01 and CR02, and route to two virtual gateways, one active/hot on CR01 and the other active/hot on CR02.
Or, if you use p2p routed links between CSW01 and CR01 and CR02, you could also just have a static route to each.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2017 09:08 AM
Hi, Joseph, CSW01 is Cat4507 switch
"One method would be to run a dynamic routing protocol between the 3 devices, and have CR01 and CR02 as equal cost from CSW01."
I've added to maximum-paths to my OSPF configuration but it seems there is no result...(
I can't use EIGRP because of other, non-CISCO switches.
Could you please enlight me with this:
"Or, if you use p2p routed links between CSW01 and CR01 and CR02, you could also just have a static route to each." What do you mean?
Many thanks in advance,
Ilya
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide