- Cisco Community
- Technology and Support
- Networking
- Routing
- Intervlan routing on layer 3 switch - does it require ip addresses? or will trunks work?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 11:35 AM - edited 03-05-2019 07:34 AM
Hello,
I am trying to get my head around intervlan routing and the thing that keeps me going in circles is the layer 3 switch does it need to ip addresses i.e gateways on the vlans of the layer 3 switch?
If we trunk from a router the vlans will the layer 3 switch be smart enough to first send to router and then do its internal switching inside.
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 04:18 PM
These are exactly correct; both will accomplish what you want and both will work. I set up my networks more in the line of the second diagram. The only change is that I don't use a VL:AN between the switch and the ASA/router. I will designate a port on the switch as a routed port (interface command no switchport), once you do this you will assign an IP address to that port like you do for a router's port. For instance in your second diagram I would assign 10.16.1.1/30 to the ASA and assign 10.16.1.2/30 to the interface on the switch. Your diagram will work just as well as my modification however. You will need to assign a gateway of 10.16.1.1 to the switch.
Regards,
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 12:35 PM
For an L3 switch to route, it needs interfaces with IPs. This could be routed port interfaces and/or SVIs. If using SVIs, would could route between them while using a trunk port.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 12:55 PM
When you say you can route between then while using a trunk port are you talking about another set of switches below the layer 3 switch i.e 2 layer 2 switches connected to a different vlan? But the L3 switch will still need vlan IPs to be able to route? correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 01:59 PM
Matt, I think you are confusing yourself talking about L3 and trunks; they are two different parts of the OSI layer and should not be interchanged.
Inter VLAN routing happens at layer 3 in a switch; within that switch you have multiple VLANs. Each VLAN has a Switch Virtual Interface (SVI), this is the VLAN interface which has an IP address assigned to the SVI. As you add VLANs and SVIs the switch will build a routing table similar to what you see in a router or a PC. Like any other IP network device (in your case the L3 switch) you have to assign an IP address (one for each VLAN or SVI) and a default router. This default route will be to a boundary devices usually a router or in your case an ASA. The only real difference for inter VLAN routing is that the switch has multiple VLANs, SVIs and IPs. Below are the VLANs I have on my L3 switch and appropriately the routing table from that switch:
interface Vlan100
description SERVERS
ip address 10.244.0.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan200
description RNT-LAB
ip address 10.19.9.1 255.255.255.224
no ip route-cache
no ip mroute-cache
!
interface Vlan250
description BUILD LAB
ip address 10.19.9.33 255.255.255.224
no ip route-cache
no ip mroute-cache
!
interface Vlan300
description RNT-HOME
ip address 10.19.8.1 255.255.255.0
no ip route-cache
no ip mroute-cache
!
interface Vlan500
description WIRELESS
ip address 10.19.9.193 255.255.255.192
no ip route-cache
no ip mroute-cache
!
interface Vlan550
description GUEST WIRELESS
ip address 10.19.9.129 255.255.255.192
ip access-group 155 in
no ip route-cache
no ip mroute-cache
!
interface Vlan900
description MANAGEMENT
ip address 10.244.3.193 255.255.255.192
no ip route-cache
no ip mroute-cache
Routing table...
Gateway of last resort is 10.13.13.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.13.13.1
10.0.0.0/8 is variably subnetted, 16 subnets, 5 masks
C 10.13.13.0/30 is directly connected, GigabitEthernet0/1
L 10.13.13.2/32 is directly connected, GigabitEthernet0/1
C 10.19.8.0/24 is directly connected, Vlan300
L 10.19.8.1/32 is directly connected, Vlan300
C 10.19.9.0/27 is directly connected, Vlan200
L 10.19.9.1/32 is directly connected, Vlan200
C 10.19.9.32/27 is directly connected, Vlan250
L 10.19.9.33/32 is directly connected, Vlan250
C 10.19.9.128/26 is directly connected, Vlan550
L 10.19.9.129/32 is directly connected, Vlan550
C 10.19.9.192/26 is directly connected, Vlan500
L 10.19.9.193/32 is directly connected, Vlan500
C 10.244.0.0/24 is directly connected, Vlan100
L 10.244.0.1/32 is directly connected, Vlan100
C 10.244.3.192/26 is directly connected, Vlan900
L 10.244.3.193/32 is directly connected, Vlan900
In the routing table you will see a /32 address, this is the SVI IP address and the various subneted addresses are the individual VLAN addresses. The only address I manually added was the gateway of last resort, everything else was built off of the SVIs and subnets by the switch.
Hope this help!
Regards,
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 03:46 PM
Hi there,
Thank you for this, yes I was getting confused, I was thinking that if the ASA trunked the vlans to the L3 switch, that the layer 3 switch would then see that it has these vlans on different physical ports and instead of sending the traffic back to the ASA, it would instead switch inside the L3 switch between the trunked vlans.
Now that I have written this out it sounds a bit dumb(sorry a i'm still learning this stuff)
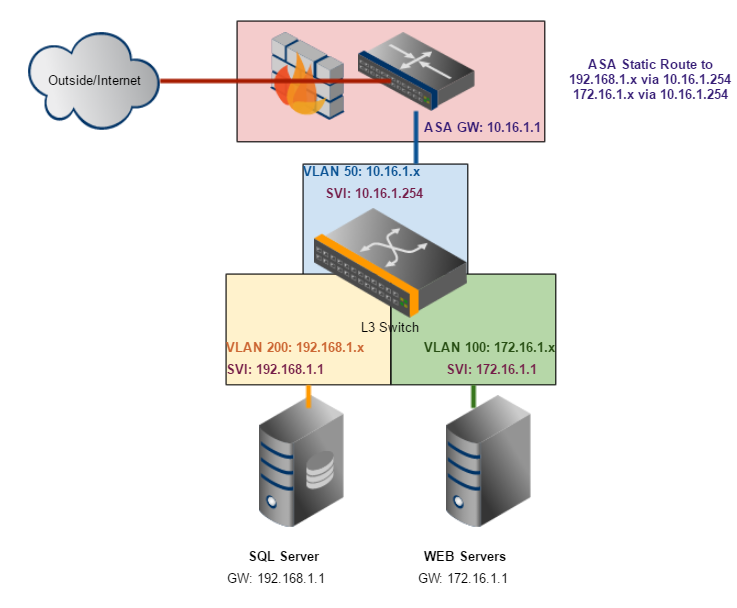
So I have created 2 diagrams, can you tell me which would be the better way to go about it?
Diagram 1 ASA shares vlan with Web servers, static route for on web servers to sql servers
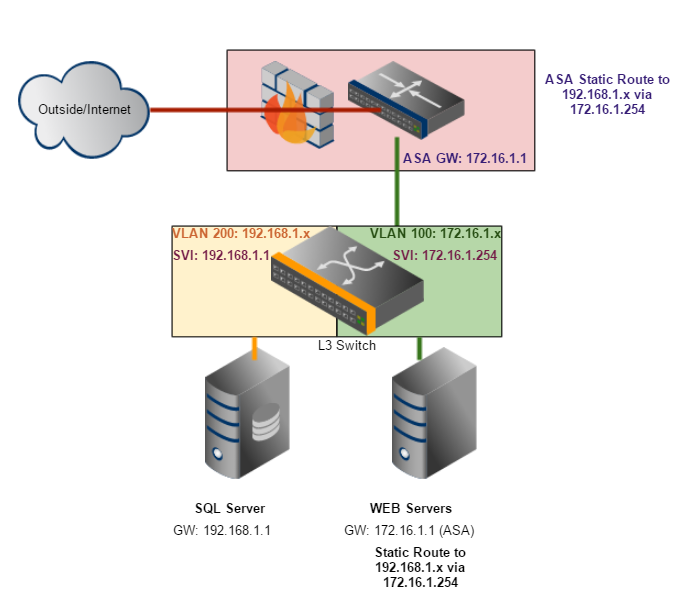
Diagram 2 (3 Vlans - no static routes on servers, only on ASA):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 04:18 PM
These are exactly correct; both will accomplish what you want and both will work. I set up my networks more in the line of the second diagram. The only change is that I don't use a VL:AN between the switch and the ASA/router. I will designate a port on the switch as a routed port (interface command no switchport), once you do this you will assign an IP address to that port like you do for a router's port. For instance in your second diagram I would assign 10.16.1.1/30 to the ASA and assign 10.16.1.2/30 to the interface on the switch. Your diagram will work just as well as my modification however. You will need to assign a gateway of 10.16.1.1 to the switch.
Regards,
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 04:25 PM
Hi Sam,
Thank you for this, I was reading some cisco documentation and saw this exactly what your talking about
http://www.cisco.com/c/en/us/support/docs/switches/catalyst-3750-series-switches/45002-intervlan3750-45002.html
So yes, I think this is better. I am hoping the ASA NAT rules will still NAT properly too with out having to change them and use the static routes to get to them, it should shouldn't it?
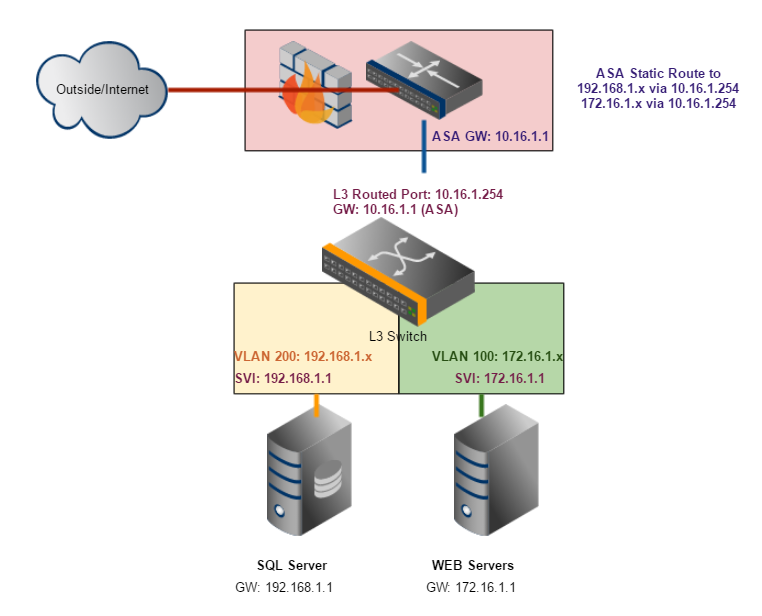
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 04:31 PM
The simple thing to do for the router and NAT translations is to use a continuous block of addresses. For instance from the ASA send back 172.16.1.0/22, this will equate to 172.16.1.1 through 172.16.3.254. Once you send the entire block back to the switch you can segment it as you need. The only thing you need to change in the ASA if you need more addresses is the subnet for the NAT process. In your example you have to NAT three different subnets.
Regards,
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 04:43 PM
Hi Sam,
This is exactly what we do now, we NAT the outside ip ranges to only 172.16.1.x /24 range addresses, which is our web servers. We don't NAT to any other network ranges.
Thank you for your help today, I am very much appreciative.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 04:48 PM
Glad I could help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2017 03:25 PM
Hi Sam,
Not sure if you can help further, but how do I setup the ASA to forward its DMZ subnet via a static route to the SVI?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2017 04:46 PM
Hi Matt,
I don't know that I can help you on this; I have no knowledge of the ASA devices. I will give you a link to a discussion on how I would handle this in an IOS device. The first thing I will tell you is that a true DMZ will send all traffic for a given public IP to a host(s) so that the host(s) can offer services to the client.
In an IOS device I send ports to individual servers based on the services they offer. That is to say I will send tcp/udp 53 to one machine, tcp 25 to another and tcp 80 to another for example. Keeping this in mind you will understand the following post a little better.
I do not know if the ASA manages these in the same way or not.
https://supportforums.cisco.com/discussion/11738651/multiple-wan-ip-addresses-and-multiple-inside-hosts
Regards,
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 12:36 PM
You are asking two questions.
The first question asks whether the layer 3 switch needs IP addresses to do inter vlan routing and the answer is that yes the switch must have an IP address in each vlan for which it will do inter vlan routing. If the layer 3 switch does not have an IP address in some particular vlan then the switch can not do inter vlan routing for that vlan.
I do not understand what you are trying to ask in your second question about sending first to the router and then doing its internal switching. Can you clarify your question?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 12:57 PM
So we have an ASA firewall, with 3 networks outside, SQL (192) and WEB (172). The plan is to move the WEB and SQLto the layer 3 switch because the ASA firewall can not handle the amount of traffic that our webservers are communicating with our SQL.
If I trunk the SQL Vlan and Web Vlan to the layer 3 switch, will they still use the ASA to switch traffic, or will the layer 3 switch know that it contains those vlans and switch internally rather than going to the ASA?
or will I need to move the ASA vlans to the layer 3 switch and bascailly set static routes in the asa to point to the interface on the switch.?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
