- Cisco Community
- Technology and Support
- Networking
- Routing
- Unable to Access Web Server - Whats Wrong with this Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unable to Access Web Server - Whats Wrong with this Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 02:37 AM
ASA working in IPSec, I am able to access HQ from UNIT No problem. Internet is only allowed on specific IPs which are outside DHCP Scope. When I assign IP for internet, now Internet is working, HQ Network is accessible, but S_EXT (webserver - 10.10.10.111) don't work. Unable to understand why it is working when internet is OFF. Here is configuration - What's wrong pl
ASA Version 9.1(1)
!
interface GigabitEthernet0/0
description ****WAN-INTERFACE****
nameif outside
security-level 0
ip address 203.x.x.x 255.255.255.252
!
interface GigabitEthernet0/1
description ****LAN-INTERFACE****
nameif inside
security-level 100
ip address 192.168.135.1 255.255.255.0
!
ftp mode passive
object network OBJ_ANY
subnet 0.0.0.0 0.0.0.0
object network S_INTERNET
range 192.168.135.230 192.168.135.240
object network S_UNIT
subnet 192.168.135.0 255.255.255.0
object network HQ
subnet 192.168.100.0 255.255.255.0
object network S_EXT
host 10.10.10.111
access-list 100 extended permit ip object S_UNIT object HQ
access-list 100 extended permit ip object S_UNIT object S_EXT
access-list OUTSIDE extended permit icmp any any echo
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static S_UNIT S_UNIT destination static HQ HQ
nat (inside,outside) source static S_EXT S_EXT destination static HQ HQ
!
object network S_INTERNET
nat (inside,outside) dynamic interface
access-group OUTSIDE in interface outside
route outside 0.0.0.0 0.0.0.0 203.x.x.x 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set MYSET esp-3des esp-md5-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map VPNMAP 20 match address 100
crypto map VPNMAP 20 set peer x.x.x.x
crypto map VPNMAP 20 set ikev1 transform-set MYSET
crypto map VPNMAP interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption
hash md5
group 2
lifetime 86400
telnet timeout 5
dhcpd dns 8.8.8.8
!
dhcpd address 192.168.135.50-192.168.135.200 inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
tunnel-group x.x.x.x type ipsec-l2l
tunnel-group x.x.x.x ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
class-map default
!
policy-map type inspect dns migrated_dns_map_1
parameters
: end
- Labels:
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 02:39 AM - edited 04-25-2024 02:40 AM
access-list 100 extended permit ip object S_UNIT object S_EXT <<- this line of crypto ACL is confuse me' I think it wrong
Compare to no-NAT you use
nat (inside,outside) source static S_EXT S_EXT destination static HQ HQ
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 09:38 AM
Thank you - what should I do ? Need to allow my UNIT to access this webserver located on HQ Subnet (10.10.10.111 is behind that subnet) and it is Tunnel traffic so also need to exclude it from NAT.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 09:43 AM
If the config you share is not for HQ then you need
access-list 100 extended permit ip object S_UNIT object HQ
access-list 100 extended permit ip object S_EXT object HQ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 09:53 AM
Again thank you - config is of UNIT not HQ, S_EXT (10.10.10.111) is a webserver which is accessible through HQ subnet (not placed in HQ). This config works good and server is accessible in UNIT office, when internet is not working. Once internet is available in UNIT on same network this server is inaccessible, will try update access-list and will update pl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 11:21 PM
@MHM Cisco World wrote:If the config you share is not for HQ then you need
access-list 100 extended permit ip object S_UNIT object HQ
access-list 100 extended permit ip object S_EXT object HQ
Changed access-list to above and now S_EXT is inaccessible from UNIT even without Internet. So, it is not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 02:38 AM
Hello
Can you share a topology diagram of this, As it will assist on understanding this issue and providing a solution
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 02:41 AM
Yes please @mfdarvesh share topolgy
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 03:04 AM
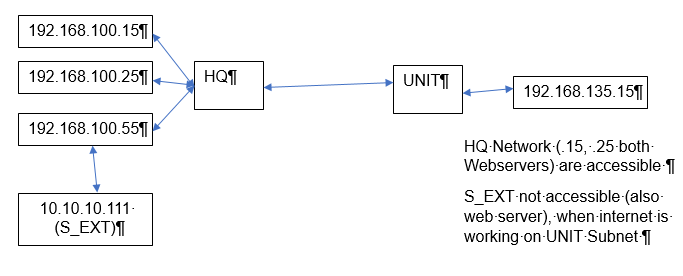
Forgive me on by bad diagram pl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 03:31 AM
Hello
So the ASA and this configuration is from UNIT , Which shows it has a Lan interface in 192.168.135.x and a wan interface, which suggest reachability to HQ is over via the internet and HQ is NATing for its internal web servers?
What i dont understand is your comment that HQ web server ( 10.10.10.111 S_EXT) IS reachable when internet is turned off at UNIT
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 03:56 AM - edited 04-26-2024 03:59 AM
@paul driver wrote:Hello
So the ASA and this configuration is from UNIT , Which shows it has a Lan interface in 192.168.135.x and a wan interface, which suggest reachability to HQ is over via the internet and HQ is NATing for its internal web servers?What i dont understand is your comment that HQ web server ( 10.10.10.111 S_EXT) IS reachable when internet is turned off at UNIT
UNIT and HQ and on IPSec tunnel and it is working. Internet is not available in UNIT (only specific IPs 192.168.100.230 has Internet). UNIT is able to access S_EXT Server when Internet is not working. When I assign UNIT PC IP Address 192.168.100.230 (Internet IP), now S_EXT server is not accessible, rest of HQ tunnel is working good, I am unable to understand, why it is creating problem with Internet enables IP in UNIT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 03:33 AM
in UNIT do you add route toward HQ for S_EXT?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 03:58 AM - edited 04-26-2024 04:00 AM
@MHM Cisco World wrote:in UNIT do you add route toward HQ for S_EXT?
MHM
NO - as this server (S_EXT) is part of HQ Subnet and through IPSec tunnel, it is working but only when Internet is not enabled in UNIT Subnet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
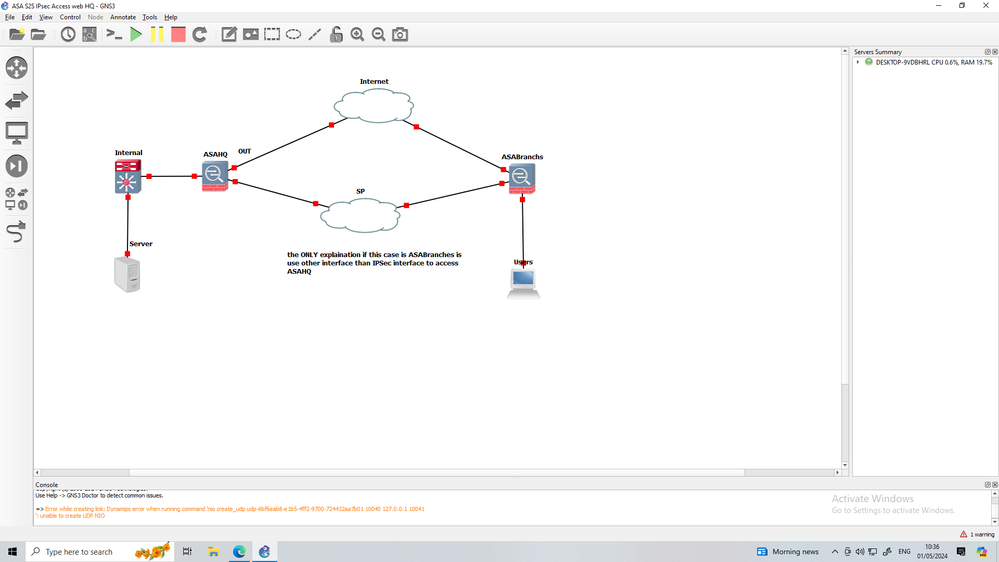
05-01-2024 12:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2024 03:16 AM
All traffic from Br to HQ is through IPSec tunnel, servers directly placed in HQ are accessible, the only server, which is not placed in HQ and accessible through HQ subnet is creating problem.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide