- Cisco Community
- Technology and Support
- Networking
- SD-WAN and Cloud Networking
- Should we enable allow-service netconf all the time?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:04 PM
I understand that when implementing configuration changes from vManage to cEdge/vEdge, the changes are made via NETCONF.
However, even if no allow-service netconf is set under Interface tunnel, the configuration can be changed without any problem.
Why is this?
Solved! Go to Solution.
- Labels:
-
SD-WAN vManage
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 02:45 AM
Hi,
one more good question...
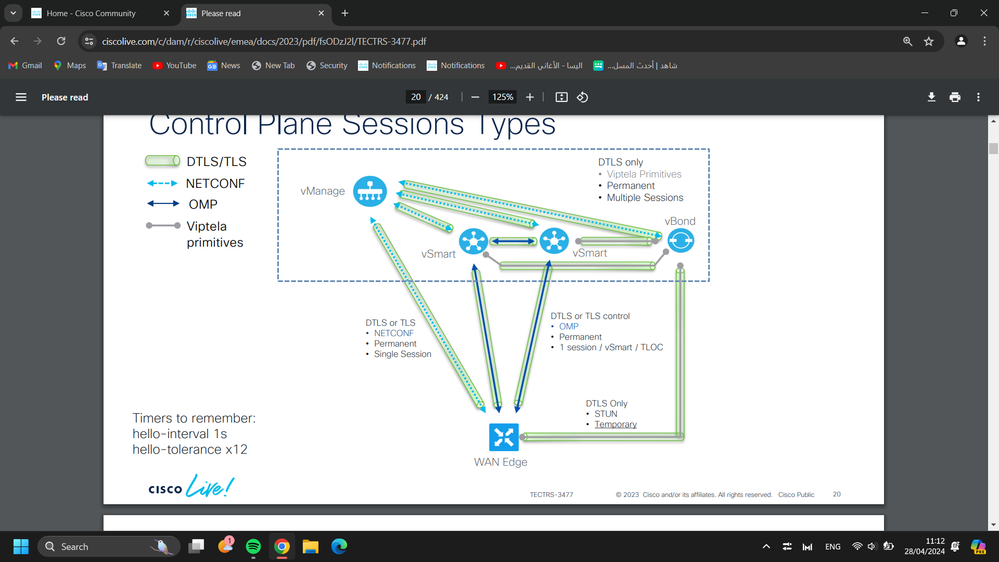
Netconf is mostly used over DTLS/TLS. So, even if you block service network on transport interface, it still works (as you mentioned) because config update is pushed via Netconf over DTLS/TLS.
However, there are certain cases where netconf is "natively" used (netconf directly over TCP830). These cases will not work when you have "no allow-service netconf".
For example, when we add controller to vmanage netconf is natively used. That is the reason on many guides/ blogs etc. it is written that "disable tunnel-interface when you add vbond/smart to vmanage". Disabling tunnel removes that implicit-access list and any checks. In reality if you allow network service while you have tunnel interface, you can still add vbond/smart to vmanage w/o any issue.
Network Configuration Protocol (NETCONF)
The NETCONF protocol defines a mechanism through which network devices are managed and configured. The SD-WAN Manager uses NETCONF for communication with SD-WAN devices, primarily over DTLS/TLS, but there are a few situations where NETCONF is used natively before DTLS/TLS connections are formed:
● When any control component (SD-WAN Manager, Validator, or Controller) is added to the SD-WAN Manager, an SD-WAN Manager instance uses NETCONF to retrieve information from them and allows them to be added as devices into the GUI. This might be when initially adding controllers to the SD-WAN Manager, or for incremental horizontal scaling deployments, by adding SD-WAN Manager instances to a cluster or adding additional SD-WAN Controllers or Validators.
● If any control component reloads or crashes, then that control component uses NETCONF to communicate back to the SD-WAN Manager before encrypted DTLS/TLS sessions are re-formed.
● NETCONF is also used from the SD-WAN Manager when generating Certificate Signing Requests from control components through the SD-WAN Manager GUI before DTLS/TLS connections are formed.
NETCONF is encrypted SSH using AES-256-GCM and uses TCP destination port 830.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 11:39 PM
Can you post full config of interface -
Do you have under interface allow-service all (this overrides all other config)
check the below guide what ports used :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 02:45 AM
Hi,
one more good question...
Netconf is mostly used over DTLS/TLS. So, even if you block service network on transport interface, it still works (as you mentioned) because config update is pushed via Netconf over DTLS/TLS.
However, there are certain cases where netconf is "natively" used (netconf directly over TCP830). These cases will not work when you have "no allow-service netconf".
For example, when we add controller to vmanage netconf is natively used. That is the reason on many guides/ blogs etc. it is written that "disable tunnel-interface when you add vbond/smart to vmanage". Disabling tunnel removes that implicit-access list and any checks. In reality if you allow network service while you have tunnel interface, you can still add vbond/smart to vmanage w/o any issue.
Network Configuration Protocol (NETCONF)
The NETCONF protocol defines a mechanism through which network devices are managed and configured. The SD-WAN Manager uses NETCONF for communication with SD-WAN devices, primarily over DTLS/TLS, but there are a few situations where NETCONF is used natively before DTLS/TLS connections are formed:
● When any control component (SD-WAN Manager, Validator, or Controller) is added to the SD-WAN Manager, an SD-WAN Manager instance uses NETCONF to retrieve information from them and allows them to be added as devices into the GUI. This might be when initially adding controllers to the SD-WAN Manager, or for incremental horizontal scaling deployments, by adding SD-WAN Manager instances to a cluster or adding additional SD-WAN Controllers or Validators.
● If any control component reloads or crashes, then that control component uses NETCONF to communicate back to the SD-WAN Manager before encrypted DTLS/TLS sessions are re-formed.
● NETCONF is also used from the SD-WAN Manager when generating Certificate Signing Requests from control components through the SD-WAN Manager GUI before DTLS/TLS connections are formed.
NETCONF is encrypted SSH using AES-256-GCM and uses TCP destination port 830.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 03:02 AM - edited 04-28-2024 01:15 AM
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2024 01:15 AM
check this photo
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide