We are excited to announce new additions to our growing list of Machine-Learning-powered Confirmed Threat detections provided by the Cognitive Intelligence engine. Thanks to the improvement made to our Machine Learning backend (see Machine Learning Backend Improved blog) we have added 22 net-new Confirmed Threat types (see list below) and increased detection rates for the previously existing Confirmed Threats in the past six months.
Newly Added Confirmed Threats
| Confirmed Threat ID |
Name |
Category |
Risk |
Description |
| CLKB00 |
LokiBot malware |
information stealer |
Critical |
LokiBot is a commodity malware sold on underground sites which is designed to steal private data from infected machines and submit it to the command and control (C2) server via a HTTP request. |
| CORR01 |
Orcus RAT |
information stealer |
Critical |
A campaign that delivers the Orcus Remote Access Trojan embedded in video files and images. The trojan focuses on information stealing and .NET evasion. Capable of stealing browser cookies, passwords, manipulating webcam and microphone, even launching server stress tests (DDoS attacks). |
| CRAT07 |
Gh0st RAT |
information stealer |
Critical |
Gh0st RAT. Gh0st RAT gives the attacker complete remote control and administration of the infected device. Threat is capable of stealing information, executing commands, modifying registry keys, and grabbing screen captures of the infected host. |
| CRAT08 |
NanoCore RAT |
information stealer |
Critical |
NanoCore RAT. NanoCore RAT gives the attacker complete remote control and administration of the infected device. Threat is capable of stealing information, executing commands, modifying registry keys, and grabbing screen captures of the infected host. |
| CDRP05 |
Malspam/Vidar |
malware distribution |
High |
Malicious spam (malspam) using Microsoft Office documents. This campaign is distributing the new version of Vidar, a powerful information stealer. |
| CFEK01 |
Fallout EK |
exploit kit |
High |
Fallout exploit kit (EK) which exploits vulnerabilities in IE and Flash to infect the device with malware. The malware delivered by the EK varies, it usually spreads ransomware, lately focusing on GandCrab. |
| CKRS01 |
Coin miner |
cryptocurrency miner |
High |
Linux coin miner which installs cryptocurrency-mining malware onto the device. It targets systems with high computational power. It is capable to survive reboots and deletions. |
| CSHL01 |
OSX/Shlayer malware |
malware distribution |
High |
OSX/Shlayer variant, macOS malware. The Trojan horse infection is spread through a fake Flash Player installer. The initial infection leverages shell scripts to download additional malware or adware onto the infected system. |
| CGCB01 |
GrandCrab ransomware |
ransomware |
High |
GandCrab ransomware which steals user data to hold it hostage. Distribution methods include automated attacks using exploit kits such as Fallout EK, Emotet, and credential stealers like Vidar. |
| CTAL0001 |
Emotet banking trojan |
trojan |
High |
Emotet is a banking trojan that has remained relevant due to its continual evolution to better avoid detection. It is commonly spread via malicious emails. (Talos cluster) |
| CTAL0002 |
GrandCrab ransomware |
ransomware |
High |
GandCrab is ransomware that encrypts documents, photos, databases and other important files using the file extension ".GDCB", ".CRAB" or ".KRAB". (Talos cluster) |
| CTAL0003 |
Cerber ransomware |
ransomware |
High |
Cerber is ransomware that encrypts documents, photos, databases and other important files using the file extension ".cerber". (Talos cluster) |
| CTAL0004 |
Eldorado Ircbot |
trojan |
High |
Ircbot, also known as Eldorado, is known for injecting into processes, spreading to removable media, and gaining execution via Autorun.inf files. (Talos cluster) |
| CTAL0005 |
Autoit malware family |
trojan |
High |
Autoit is a malware family leveraging the well-known AutoIT automation tool, widely used by system administrators. AutoIT exposes a rich scripting language that allows to write fully functional malicious software. (Talos cluster) |
| CTAL0006 |
Vobfus worm |
trojan |
High |
Vobfus is a worm that copies itself to external drives and attempts to gain automatic code execution via autorun.inf files. It also modifies the registry so that it will launch when the system is booted. Once installed, it attempts to download follow-on malware from its C&C servers. (Talos cluster) |
| CTAL0007 |
Razy trojan |
trojan |
High |
Razy is oftentimes a generic detection name for a Windows trojan. They collect sensitive information from the infected host and encrypt the data, and send it to a command and control (C2) server. (Talos cluster) |
| CTPG02 |
Emotet banking trojan |
banking trojan |
High |
Emotet banking Trojan, also known as Geodo. Geodo is a modular botnet which may steal confidential information including financial data and credit card information, modify encrypted traffic, and send spam. (Talos cluster) |
| CZAC00 |
ZeroAccess rootkit |
click fraud |
High |
ZeroAccess outbound communication, a rootkit that relies on P2P for C2 communications. ZeroAccess is typically delivered through exploit kits hosted on compromised servers and used for click-fraud and/or bitcoin mining. |
| CADI53 |
Browser ad-injector |
ad injector |
Med |
Potentially unwanted applications (PUAs) that inject advertising into the user’s browser session that may lead to further malware infections. |
| CTSQ02 |
Typosquatting sites |
malicious content distribution |
Low |
Typosquatting campaigns that distribute malicious software through drive-by downloads. When users access these sites, such as 'twitter.om' instead of 'twitter.com,' they get redirected to malicious sites meant to lure the user into installing malicious software. |
| CPRL01 |
Browser ad-injector |
PUA |
Low |
Potentially unwanted applications (PUAs) that inject advertising into the user’s browser session which may lead to further malware infections. |
| CPHI06 |
Pied Piper phishing/RAT |
malware distribution |
Low |
Pied Piper phishing campaign. The infection vectors are Word documents containing macros that leverage the legitimate msiexec.exe binary from Microsoft to download and execute downloaders that deploy RATs (Remote Access Trojans) such as Ammyy RAT. |
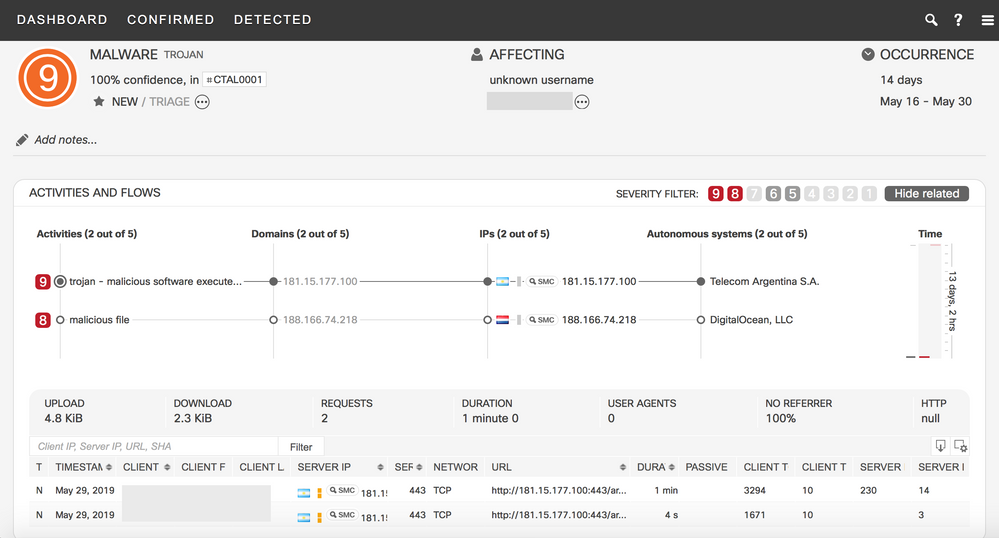 Sample finding of Emotet banking trojan (Confirmed Threat ID CTAL0001)
Sample finding of Emotet banking trojan (Confirmed Threat ID CTAL0001)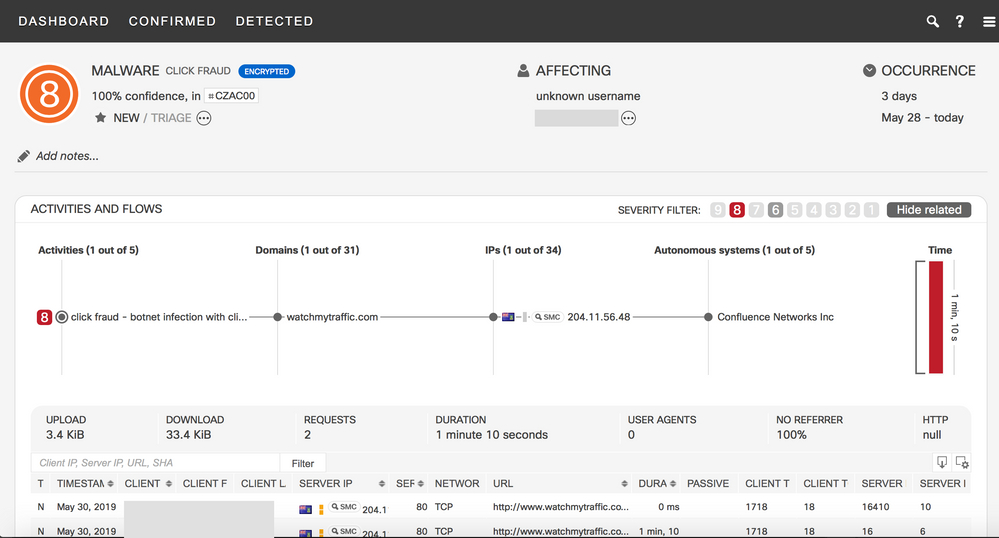 Sample finding of ZeroAccess rootkit (Confirmed Threat ID CZAC00)
Sample finding of ZeroAccess rootkit (Confirmed Threat ID CZAC00)
Confirmed Threat Updates
Note that our newly introduced semi-automatic Indicator-of-Compromise (IoC) hunt processes (see Machine Learning Backend Improved blog) allowed us to increase the IoC coverage of existing Confirmed Threats. From November 2018 till May 2019 we added altogether 792 High risk IoCs, 446 Mid risk IoCs and 1886 Low risk IoCs, covering 49 different Confirmed Threat types. In particular, more than hundred IoCs have been added to each of the following Confirmed Threats: ngrBot (variant of Dorkbot, high risk), Necurs backdoor trojan (high risk), Pirrit and other forms of adware (mid risk), Adware InstallCore (mid risk), Typosquatting (low risk) and untrusted VPN services (low risk).
