- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Using Let's Encrypt Certificates with Cisco FirePower, ISE & IOS XE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-02-2023 12:24 PM - edited 11-04-2023 04:18 PM
Table of Contents
- Table of Contents
- Summary
- Let's Encrypt
- Traditional Certificate Process
- Installing Certbot
- Let's Encrypt Registration
- Domain Validation Process
- Generating a Certificate
- Use Certbot to request a certificate for ravpn.ourdomain.net
- Use your DNS management tool to create the TXT record.
- Use GoogleToolBox App to Verify TXT Record
- Back to Certbot to Finish the Request
- Use your DNS management tool to delete the TXT record.
- Next Steps
- Other Certbot Tasks
- Validate
- Delete
- Revoke
- Deeper Dive into Certificate Directory & Files
- Certbot Logging
Summary
Most organizations use certificates. Popular reasons for needing certificates could be securing a Remote Access VPN solution, either ASA or Firepower, verifying identity, or encryption. Some of these purposes, especially Remote Access VPN solutions typically require a globally recognized certificate to operate correctly. These certificates can be obtained from a number of 'paid' entities, or they can be obtained for free from Let's Encrypt.
In this article, I will go over the process and requirements for obtaining a certificate from Let's Encrypt and how to manage certificates in the local Let's Encrypt database. In follow-up articles, I will discuss and show how to import those certificates to IOS XE & Cisco Firepower.
Let's Encrypt
Let's Encrypt was founded in 2014. Let's Encrypt offers free Domain Validated TLS certificates. They support the ACME protocol for certificate management. ACME is backed by RFC 8555. ACME allows for an automated certificate enrollment and renewal process. LE certificates have a validity period of 90 days which is much shorter than certificates that are purchased which are typically 365 days. We should all recognize that over the course of the past decade certificate lifetimes have gotten shorter and shorter. With the short certificate lifetime, we should embrace the ability to automate certificate operations.
Note: I'm writing this in Sept 2023 and it is my expectation that by January 2025, 90 day certificate lifetime will be standard. Google is already pushing for this to occur.
Traditional Certificate Process
Traditionally working with certificates is a multi-step process that looks something like the steps below.
- Generate an RSA or EC-based Key Pair. That Key Pair contains the Public Key which is used to encrypt data and the Private Key which is used to decrypt data.
- Generate a Certificate Signing Request which would contain the public key.
- Send that CSR to a Certificate Authority like Globalsign or Verisign.
- The Certificate Authority will send back an Identity certificate.
- Create a trustpoint that will include the CA Certificate, any intermediate CA Certificates, and the Identity Certificate.
Things are much different with Let's Encrypt, we will dive in a little deeper in the next sections.
Installing Certbot
First, we need to install Certbot. Certbot is the tool we will use to interact with Let's Encrypt. It's free, open source, very powerful, and it is an easy method of interacting with Let's Encrypt. In our examples below we will keep it pretty simple, just be aware Certbot can be a rabbit hole it has so much functionality!
I use Certbot on an Ubuntu box.
sudo apt-get install certbot python3-certbot-apache
Want to use Certbot on a Windows box. Click here for Windows Certbot Download.
Want to use Certbot on an OSX box? Install it via Homebrew with this command.
brew install certbot
Let's Encrypt Registration
NOTE: Typically all Certbot commands must be run with sudo. There are ways to work around this but that is for a different discussion.
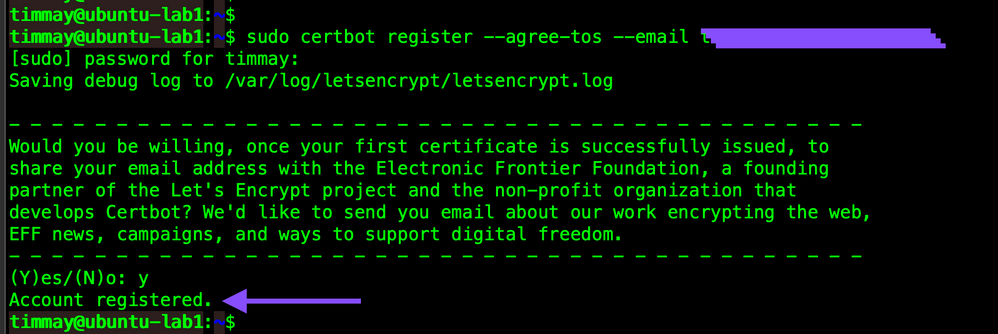
In order to use Certbot you must first register with Lets Encrypt.
In my experience, you won't receive a confirmation email. The only time I've received emails is when a certificate is close to expiring.
sudo certbot register --agree-tos --email your-email-address@ourdomain.net
Domain Validation Process
Let's Encrypt requires users to validate they own the domain. This can be done by either placing a file on a public-facing webserver (HTTP-01) or by creating a TXT record in public-facing DNS (DNS-01). Let's Encrypt calls these Challenge Types, you can read more at that link. Cisco IOS and Cisco FirePower do not allow for placing a file on the device; so we will need to use the DNS-01 authorization method.
Generating a Certificate
Let's say we own a public-facing domain called ourdomain.net, and our Firepower RA VPN FQDN will be ravpn.ourdomain.net. Let's Encrypt will require us to create a TXT DNS record with a string of characters before it issues us a certificate.
The process looks like this.
Use Certbot to request a certificate for ravpn.ourdomain.net
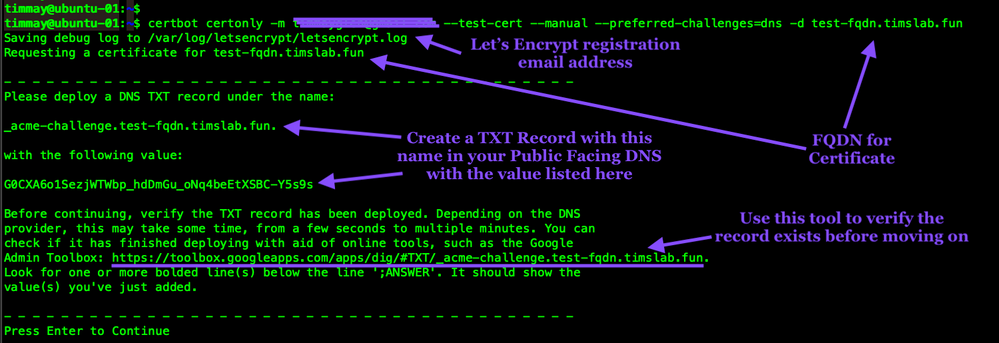
certbot certonly -m your-email-address@ourdomain.net --test-cert --manual --preferred-challenges=dns -d ravpn.ourdomain.net
Let's look at this command in more detail.
certbot is the executable
certonly tells Certbot to just obtain the certificate and not to install it on the box. We do this because we will install it on our Cisco device later.
-m tells Let's Encrypt the registration email address. This email will receive certificate expiring notices.
--test-cert tells Let's Encrypt to use the STAGING environment. It's very important to use the LE Staging environment while testing. The LE Production environment is strict when it comes to issuing and renewing certificates. Only use Prod when you know what you are doing.
--manual tells Certbot that we need to specify a Challenge Type, this is so Certbot doesn't try and install the certificate on the local machine
--preferred-challenges=dns tells Certbot we will use DNS-01 Challenge Type
-d ravpn.ourdomain.net is the FQDN of the device we will install the certificate on. The FQDN in this parameter will appear in both the Subject and the Subject Alternative Name fields of the certificate.
Certbot will prompt to add the TXT Record
DON'T press Enter yet!
Use your DNS management tool to create the TXT record.
This process really depends on what tool you use to manage your DNS so I'm not going to provide an example. Just be aware this HAS to be a public-facing DNS.
Use GoogleToolBox App to Verify TXT Record
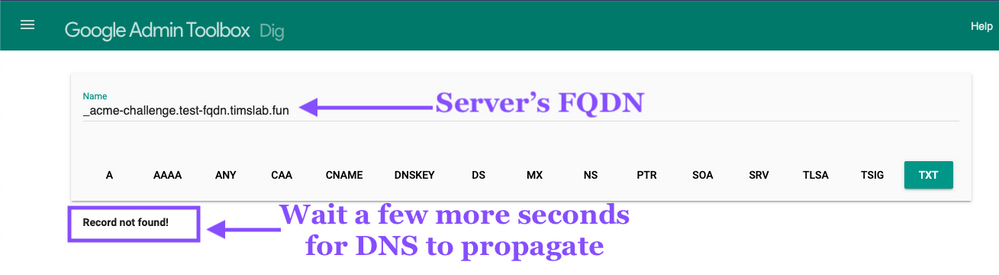
After you've created the TXT record we should verify that it's accessible. The certbot CLI that we used above provides you the URL to use to check.
This example shows the TXT Record is not available yet. Wait a few more seconds for DNS to update \ propagate.
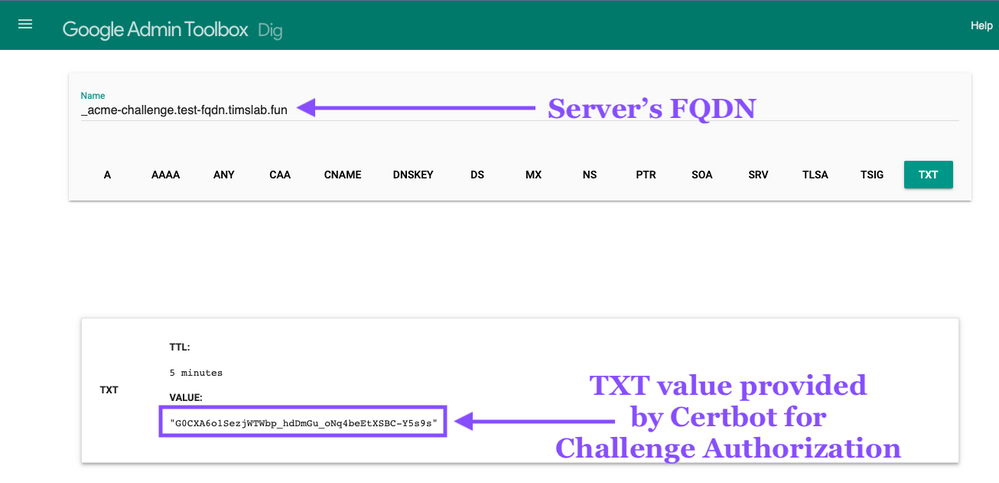
This example shows the record is created and the TXT is displayed for validation.
Back to Certbot to Finish the Request
Now that you've created the DNS TXT Record and verified it can be queried by the internet, you can go back to the Certbot command that should be still waiting for you to press Enter.
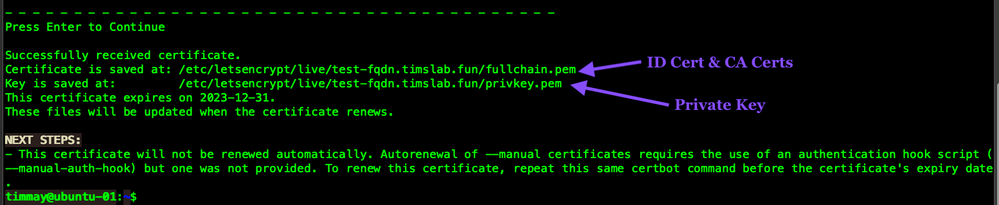
At this point we see the following. Successfully received certificate! We also see the certificate location and the private key location.
Use your DNS management tool to delete the TXT record.
This process really depends on what tool you use to manage your DNS so I'm not going to provide an example. Now that the TXT record has been validated and Let's Encrypt has issued the certificate you can and should delete the TXT record. It has no value.
Next Steps
I haven't authored these yet but they will come soon.
- Using Let's Encrypt Certificates with Cisco Firepower
- Using Let's Encrypt Certificates with Cisco ASA
- Using Let's Encrypt Certificates with IOS XE (link coming before the end of Dec 2023)
- Using Let's Encrypt Certificates with Cisco ISE (link coming before the end of Dec 2023)
Other Certbot Tasks
Validate
This command will show you all the certificates that Certbot is managing on this local box.
certbot certificates
If you need to display just one certificate you can use the --cert-name parameter.
certbot certificates --cert-name ravpn.ourdomain.net
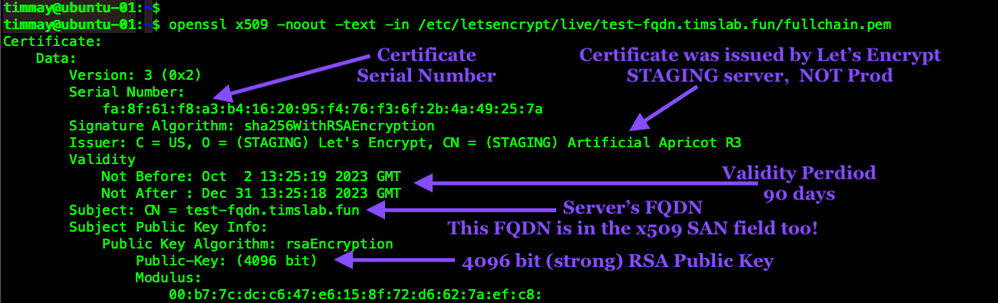
You can use the uber popular tool openssl to find details about the certificate you've just been issued. The output of this command is long.
openssl x509 -noout -text -in /etc/letsencrypt/live/ravpn.ourdomain.net/fullchain.pem
Delete
Delete allows you to delete certificates from the Certbot database
certbot delete --cert-name ravpn.ourdomain.net
Revoke
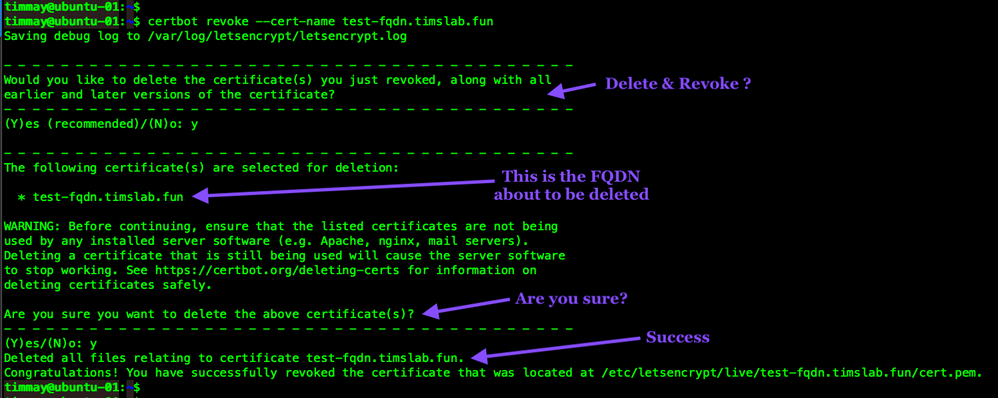
Revoke allows you to revoke certificates that Let's Encrypt has issued. Revoke will also ask if you would like to delete the certificate from the Certbot database.
certbot revoke --cert-name ravpn.ourdomain.net
You can also specify the reason you are revoking the certificate. This is a fairly popular option that I've seen in most Certificate Authorities. Supported reasons are unspecified, keycompromise, affiliationchanged, superseded, and cessationofoperation.
certbot revoke --cert-name ravpn.ourdomain.net --reason keycomprimise
Deeper Dive into Certificate Directory & Files
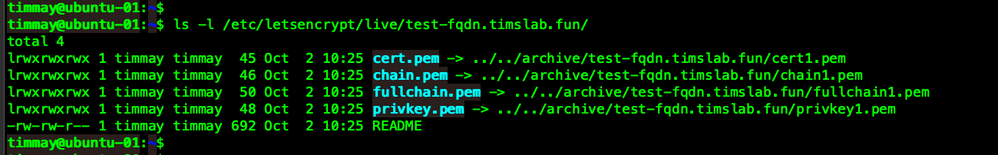
Let's take a look at the directories that our files are in ...
We can see that these files are just symlinks to other files that are located in the archive directory.
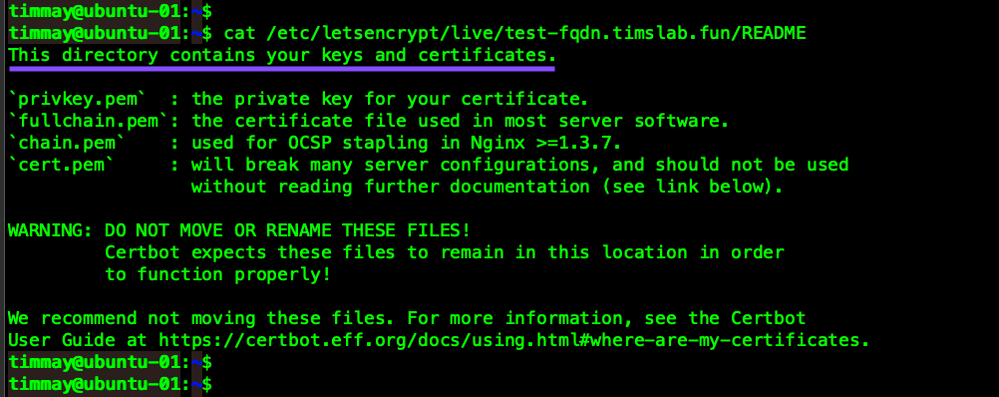
We also see a README file, let's check that out.
All the files are in PEM format. PEM is a Base64 text based method of storing data. There are countless tools on the internet for evaluating this Base64 text, my favorite is openssl. Take a look at this GitHub link for how to use openssl to investigate the data in these files.
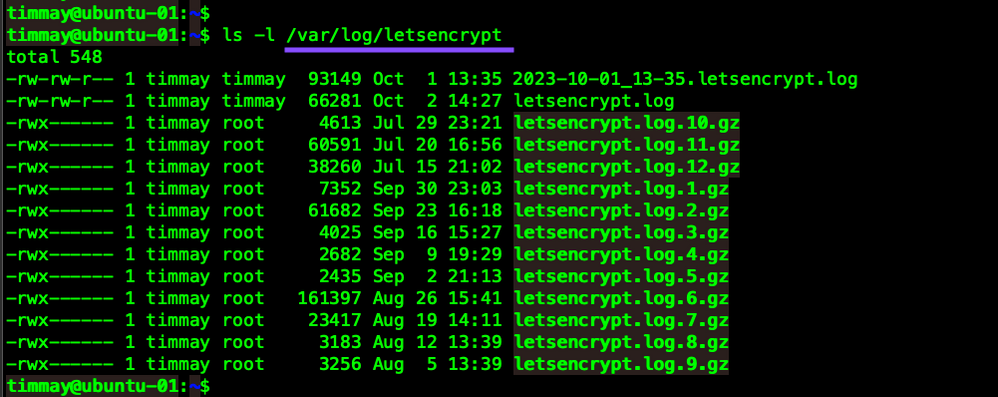
Certbot Logging
Certbot stores all its logs in /var/log/letsencrypt
They are in text format and can be viewed using any standard text editor.
That's It!
I hope this document has helped you become more familiar with Let's Encrypt process and the Certbot tool that we use to interact with the Let's Encrypt service.
Please let me know your feelings in the comment section or via DM.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great article. I gave it a try and it works great! Then I started wondering about a few things:
- should one delete the TXT record as soon as the cert has been generated? Isn't this a security weakness since anyone can guess the lookup construct and then use that to claim domain ownership? I guess that would break the renew process unless you created a new/unique txt record for each renew
- Have you tried doing a renew, and is it as simple as "certbot renew" ?
I am keen to try this with ISE 3.3 and the Cert API to install a Guest Portal cert programmatically.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for documenting this process. But it's sad that Cisco doesn't have any native implementations in these mentioned products. Especially as Cisco is a founding member of Let's Encrypt.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Karsten Iwen , agreed.
@Arne Bier , Yes , there is no need for the TXT record verification so delete it. I've updated the doc. Cert Renewal should use the same command as initial cert issuance. Because we are using --manual it makes renewal a manual process as well. Hope this helps!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the guide! Looking forward to the Cisco ISE part.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great article! Looking forward for the IOS XE and ISE part.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: