- TP FW doesn't act as router hop
- It uses bridging protocols to join two or more interfaces in one bridge group
- Within bridge group, segments can communicate
- You need to have BVI interface for each bridge group with an IP of the same subnet
- If BVI isn't configured the following syslog is generated '%ASA-6-322004: No management IP address configured for transparent firewall. Dropping protocol ICMP packet from IN:10.150.1.1/2048 to OUT:10.150.1.2/0'
- Communication between bridge groups is isolated within transparent firewall
- Dot1Q tagged traffic won't pass-through as you can't configure same VLAN on two interfaces in ASA
- It performs same functionalities as Routed FW related to access policies, inspection, etc
- Same checks are applied between interfaces in bridge group
- NameIf and Security-Levels should be assigned to interfaces within a group
interface GigabitEthernet0/0
nameif in
bridge-group 100
security-level 100
!
interface GigabitEthernet0/1
nameif out
bridge-group 100
security-level 0
!
interface BVI100
ip address 10.150.1.100 255.255.255.0
- Default Access rules:
- Unicast IPv4/IPv6 is allowed from high-sec to low-sec interfaces
- Low-sec to high-sec traffic is blocked and require access policy
- ARPs are allowed
- Broadcast and Multicast require access rules for both directions
- An example is allow routing protocols through TP FW
access-list routing extended permit eigrp any any
access-list routing extended permit udp any any eq rip
access-list routing extended permit ospf any any
!
access-group routing global
- Non-IP Traffic (EtherType 0x800) is blocked by default
- MPLS, CDP, etc (an exception made for BPDUs and IS-IS)
- CDP EtherType is 0x2000
- MPLS EtherType is 0x8847
- EtherType ACLs can't be global
access-list EtherType-ACL ethertype permit 2000
access-list EtherType-ACL ethertype permit mpls-unicast
!
access-group EtherType-ACL in interface in
access-group EtherType-ACL in interface out
- Mac Address vs. Route Lookups
- Within bridge group exit interface is identified using MAC Address Lookups
- For traffic initiated by TP FW traffic will use local routing table
- For traffic inspected by TP FW such as TFTP, SIP, etc traffic will use local routing table
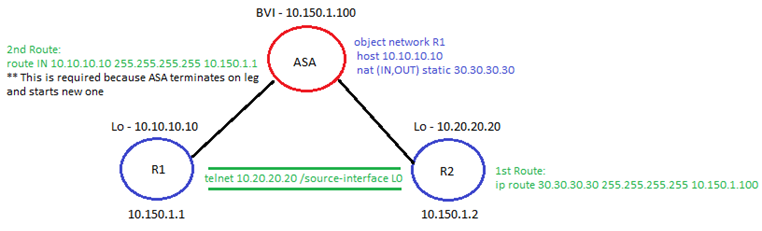
- For traffic natted by TP FW + Destination isn't directly connected:
- Static route is required on upstream router pointing to BVI IP of TPFW - Destination is the natted IP
- Static route is required on TP FW pointing to next-hop which is R1 - Destination is un-natted IP