- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ZONE BASED FIREWALL IMPLEMENTATION
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-17-2024 07:09 AM - edited 04-24-2024 11:59 PM
Zone-Based FireWall (ZBFW)
Introduction
Rules for applying ZBFW
ZBFW Terminology
ZBFW Actions
ZBFW Configuration
Introduction:
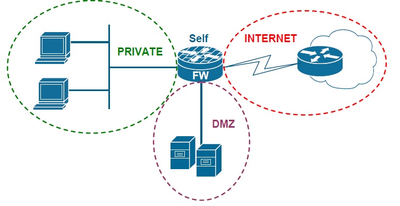
The Cisco IOS Zone-Based Firewall is a stateful firewall used in Cisco IOS devices. ZBFW is the successor of the legacy IOS firewall or the ContextBased Access Control (CBAC) feature. Zone Based Firewall is the most advanced method of a stateful firewall that is available on Cisco IOS routers.
Zone-Based Policy Firewall (also known as ZBAF) changes the firewall configuration from the older interface-based model to a more flexible, more easily understood zone-based model. The idea behind ZBW is that we don’t assign access-lists to interfaces but we will create different zones. Interfaces will be assigned to the different zones & security policies will be assigned between zones.
Cisco ASA and FTD devices are considered dedicated firewall devices. However, Cisco integrated the firewall functionality into the router, which infact will make the firewall a cost-effective device. The Zone-Based FireWall (ZBAF) includes features that are not available in CBAC/IOS firewall. Zone-Based Firewalls (ZBAF) can also be implemented in an SD-WAN solution.
Rules For Applying Zone-Based Firewall:
- A zone must be configured before interfaces can be assigned to the zone. An interface can be assigned to only one security zone. All traffic to and from a given interface is implicitly blocked when the interface is assigned to a zone.
- Traffic is implicitly allowed to flow by default among interfaces that are members of the same zone. In order to permit traffic to and from a zone member interface, a policy allowing or inspecting traffic must be configured between that zone and any other zone.
- The self zone is the only exception to the default deny all policy. Traffic cannot flow between a zone member interface and any interface that is not a zone member. Pass, inspect, and drop actions can only be applied between two zones.
- Interfaces that have not been assigned to a zone function as classical router ports and might still use classical stateful inspection/CBAC configuration.
- If it is required that an interface on the box not be part of the zoning/firewall policy. It might still be necessary to put that interface in a zone and configure a pass all policy (sort of a dummy policy) between that zone.
Zone-Based Firewall Terminology
- Security zone: It is a group of interfaces to which a policy can be applied. To allow traffic pass between zones, administrators must explicitly declare by creating a zone-pair and a policy for that zone.
- Zone-pair: It allows you to specify a unidirectional firewall policy between two zones. In other words, a zone-pair specifies the direction of the interesting traffic. This direction is defined by specifying a source and destination zone. Notice that we can’t defined a zone as both source and destination zone.
- Zone Policy: It defines what we want to allow or deny to go between zones. For example we just want to allow HTTP while dropping SMTP, ICMP and other protocols.
Zone-Based Firewall actions
- Drop: This is the default action for all traffic, as applied by the "class class-default" that terminates every inspect-type policy-map. Traffic that is handled by the drop action is "silently" dropped (i.e., no notification of the drop is sent to the relevant end-host) by the ZFW.
- Pass: This action allows the router to forward traffic from one zone to another. The pass action does not track the state of connections or sessions within the traffic
- Inspect: The inspect action offers state-based traffic control. For example, if traffic from the private zone to the Internet zone in the earlier example network is inspected, the router maintains connection or session information for TCP and User Datagram Protocol (UDP) traffic. Therefore, the router permits return traffic sent from Internet-zone hosts in reply to private zone connection requests.
Zone-Based FireWall Configuration
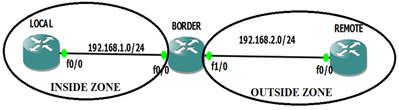

Step 1: Create the Zones
BORDER(config)# zone security Inside
BORDER(config-sec-zone)# description Inside network
BORDER(config)# zone security Outside
BORDER(config-sec-zone)# description Outside network
Step 2: Define Traffic Classes
BORDER(config)# class-map type inspect match-all ICMP
BORDER(config-cmap)# match protocol icmp
BORDER(config-cmap)# exit
Step 3: Define Firewall Policies
BORDER(config)# policy-map type inspect POLICY1
BORDER(config-pmap)# class type inspect ICMP
BORDER(config-pmap-c)# inspect
Step 4: Assign Policy Maps to Zone Pairs
BORDER(config)# zone-pair security IN-TO-OUT source Inside destination Outside
BORDER(config-sec-zone-pair)# description Internet Access
BORDER(config-sec-zone-pair)# service-policy type inspect POLICY1
Step5: Assign Router interfaces to the zones
BORDER(config)# interface F0/0
BORDER(config-if)# zone-member security Inside
BORDER(config-if)#exit
BORDER(config-if)# interface fa1/0
BORDER(config-if)# zone-member security Outside
BORDER(config-if)#exit
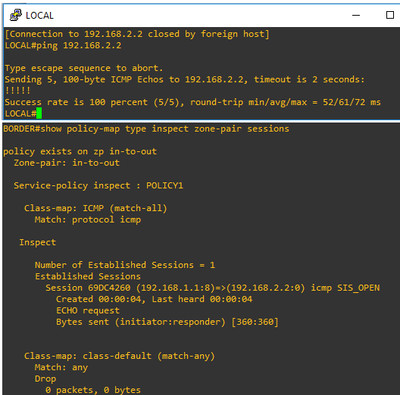
Verification:-
BORDER# show policy-map type inspect zone-pair sessions
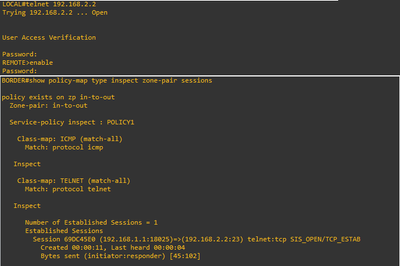
To allow Telnet Traffic
BORDER(config)# class-map type inspect match-all TELNET
BORDER(config-cmap)# match protocol telnet
BORDER(config-cmap)#exit
BORDER(config)# policy-map type inspect POLICY1
BORDER(config-pmap)# class type inspect TELNET
BORDER(config-pmap-c)# inspect
BORDER(config-pmap-c)# end
Verification
Thank You Verymuch...!!
----------------------------------------------- The End --------------------------------------------
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: