- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Meeting Server as Adhoc conference for CUCM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 07:34 AM - edited 03-18-2019 12:56 PM
I tried to register cms as conference bridge to CUCM but it doesn't register. my security sip trunk to CMS is up which i can see ping interval time.
I got this message from document
"1. Set up an incoming dial plan on the Meeting Server see the Cisco Meeting Server
Deployment Guide. For adhoc calls the rule should match against spaces."
Is it needed to configure dial plan on CMS? if so how to configure it?
- Labels:
-
Room Endpoints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 07:52 AM
Let me move this post to Telepresence community as Conferencing community is for MeetingPlace and Cisco WebEx Meetings Server products and not for CMS (Cisco Meeting Server).
-Dejan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 08:14 AM
Take a look at section 6.2 of the CMS 2.1 Single Combined Server Deployment Guide, it goes over outbound, inbound, and call forwarding dial plans for the CMS. There are similar sections in the other CMS Deployment Guides as well, if you're running a Single Split or Scalable and Resilient deployment.
Also suggest you take a look at the CMS 2.1 with CUCM Deployment Guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2017 11:28 PM
I configure both incoming and outbound calls and test. I can dial from cucm to cms and vice versa.
It works. But conference bridge is still not registered. Can you guide step-by-step?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2017 01:46 PM
CMS:
Set up an incoming dial plan on the Meeting Server For
Set up an administrator user account with "
Communications Manager to use.
CUCM:
Cisco Unified Communications Manager Administration, select Media Resources >
Conference Bridge. The Find and List Conference Bridges window displays.
Click Add New. The Conference Bridge Configuration window displays.
Select Cisco TelePresence Conductor from the Conference Bridge Type drop-down
list.
Enter a name and description for the Meeting Server in the Device Information pane.
Select a SIP trunk from the SIP Trunk drop-down list.
Enter the HTTP interface information and check the HTTPS check box to create a
secure HTTPS connection between Cisco Unified Communications Manager and
Cisco Meeting Server.
upload the root and intermediate certificates from the CA who signed the Call Bridge's certificate to the CallManager-trust trust store. This step needs to be done regardless of whether you configured a secure or
non-secure SIP trunk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2017 06:58 AM
Dear Sushant,
"Set up an incoming dial plan on the Meeting Server For adhoc calls the rule should match against spaces." - and what does this incoming dial plan look like? Is there any sample?
For example, if we have phones with 5xxx extension numbers on the CUCM cluster and want to set CMS as an CFB for adhoc conferences, what should we write (step-by-step) in the fileds Call mathing of "Call forwarding"? CUCM and CMS both reside in domain test.lab.
The idea of incoming dial plan is a bit bewildering cause CMS in this case is a mediaresource like vTS/Conductor, never needed to provide any dialplans whatsoever.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 12:18 PM
You configure an incoming dial plan by going to Configuration > Incoming calls within CMS. Incoming calls are matched against the domain, in your case would be "test.lab".
The Call matching table will determine if the incoming call will search Spaces, Users, IVRs, Lync, etc. If no rules are present in the Call matching table, it will result in all domains being matched.
The Call forwarding table will apply if a call doesn't match any of the rules in the Call matching table, the call will then be forwarded to the rules configured on the Outbound calls page.
Suggest you take a look at the CMS Deployment Guides, they go over the different aspects of the CMS dial plan.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2017 08:47 AM
To make ad-hoc conference calls, internal CUCM conference bridge can be used, as well as conference bridge registered on CMS.
What is the difference between them? I've tried both of it and it feels like it does not make sence which one to use.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 05:56 AM
Question. Is it absolutely necessary to have a secure trunk between CUCM and CMS for ad hoc conferencing to work? Is it possible to use a non-secure SIP trunk and still have ad hoc conferencing work? Is this the key to making a non-secure trunk work for non-secure SIP trunks to CMS from CUCM (see quote below)?...so, just be sure to upload those certs from CMS to the CUCM and it will work with a non-secure SIP trunk between CUCM and CMS? I ask because it would make my life so much easier if I cna use a non-secure SIP trunk between CUCM/CMS.
"upload the root and intermediate certificates from the CA who signed the Call Bridge's certificate to the CallManager-trust trust store. This step needs to be done regardless of whether you configured a secure ornon-secure SIP trunk"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 02:27 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 02:37 PM - edited 09-01-2018 02:44 PM
Thanks and pardon my ignorance on the subject, but here's what I've done so far. We can generate certs we use internally (a process we have at our company, certs for internal use) and I did generate a server certificate for the CMS and installed that on CMS.
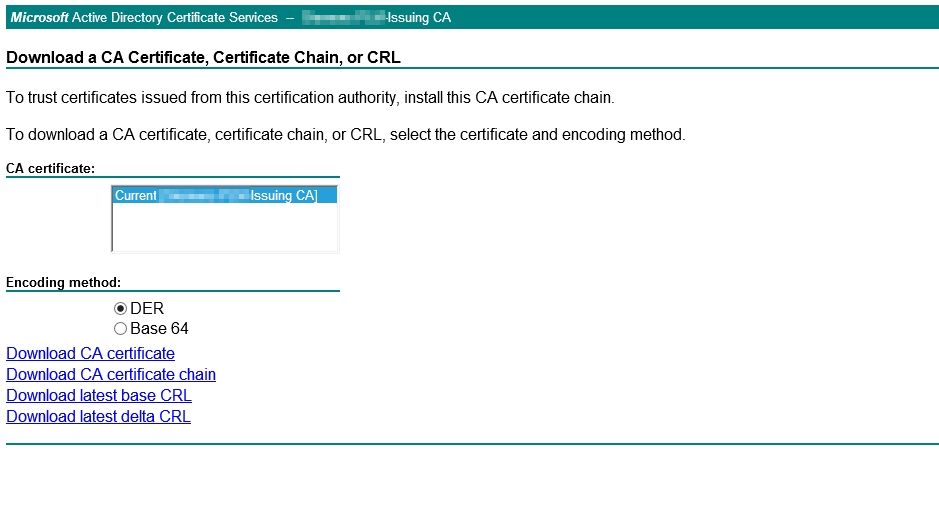
Now for CUCM (and forgive me if I get the terminology wrong because this is not my specialty)....for CUCM would we simply need to install the 'CA certificate chain' from the Trusted CA that created/signed the server certificate we generated for the CMS server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 02:43 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 02:49 PM
Great, so install the chain (p7b file), not the extracted keys from that pb7 file, correct?
Also, if I install that on the CUCM publisher, will it distribute that to the other CUCM Subscribers in the same cluster or would I need to install that chain on all the CUCM servers in the cluster and restart those servers on each cluster?
I just want to be sure I do it correctly and don't break anything.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 02:53 PM
I think you need to upload the CA chain to all of them then restart services on all of them too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 02:59 PM
Ok on uploading to all and restarting all.
Regarding the DER vesus a P7B file for the chain, I see a DER option and a Base64 option but both of them give me a P7B file when I download it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide