- Cisco Community
- Technology and Support
- Security
- VPN
- Re: cisco ISR4351 ipsec transport peer-to-peer SA tcp checksum errors
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
cisco ISR4351 ipsec transport peer-to-peer SA tcp checksum errors
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2023 08:55 AM
I am configuring an IPSEC transport so that the ISR can send messages to a host which is behind NAT. Mainly for syslog messaging and reporting. I am able to get the SA to establish and from the show crypto commands everything looks great. I can ping form the host or from the ISR and it works. However, I can't ssh in either direction. I see messages sent but the TCP connection does not establish.
When I do show tcp statistics on the ISR, it does show incrementing tcp checksum errors, so I believe the tcp packet is discarded after esp decapsulation. I cannot find a setting on the ISR to configure how checksum is handled. In RFC 3948 there are different methods for handling this. Is anyone aware of how to solve this?
I have read in some posts to disable checksum, but I can't find a way to do that.
Thanks
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2023 09:21 AM
Try use ip tcp window size
Also the traffic originate from ISR ipsec interface not pass via IPsec tunnel'
You need to specify other interface to connect to server
Note:- the interface ip must within sunbet you use in policy based vpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2023 10:19 AM
I appreciate the response.
Let me try to clarify, I am using the ipsec SA to communicate between two host machines; i.e from my host to the ISR. It isn't a tunnel. So the encrypted traffic is terminated at the ISR. I am using transport mode, not tunnel mode. I can tell using the monitor capture that it gets the packets. Since they are encrypted, I can't tell anything other than that.
I do not believe tcp window size is an issue yet, since I do not believe the TCP connection completes, I do not see a login prompt from the ISR when I try to login.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2023 11:15 AM
Let me see the config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2023 02:51 PM
This is the basic configuration I am using:
crypto ikev2 proposal ucdprop
encryption aes-cbc-128
integrity sha1
group 14
!
crypto ikev2 policy ucdpolicy
match fvrf any
match address local 192.168.21.147
proposal ucdprop
!
crypto ipsec transform-set isrucdset esp-aes esp-sha-hmac
mode transport
!
crypto ikev2 keyring ipsec-b-ring1
peer ipsec-b-nat
address 192.168.21.73
identity address 192.168.21.73
pre-shared-key hello
exit
exit
!
!
crypto ikev2 profile ipsec-nat-prof
match fvrf any
match address local 192.168.21.147
match identity remote address 3.255.1.5 255.255.255.255
identity local address 192.168.21.147
authentication remote pre-share
authentication local pre-share
keyring local ipsec-b-ring1
exit
!
crypto map ipsec-b-nat 30 ipsec-isakmp
set peer 192.168.21.73
set transform-set isrucdset
set ikev2-profile ipsec-nat-prof
match address 121
exit
!
access-list 121 permit ip host 192.168.21.147 host 192.168.21.73
interface GigabitEthernet0/0/0
crypto map ipsec-b-nat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2023 08:42 AM
access-list 121 permit ip host 192.168.21.147 host 192.168.21.73
!
crypto map ipsec-b-nat 30 ipsec-isakmp
set peer 192.168.21.73
How ipsec work th traffic must hit the acl of s2s vpn then traffic encrypt.
Here you use local and remote host is same as set peer of vpn' so traffic not hit acl of vpn.
You need to use lo in one side and use server ip in other side then permit this lo+server ip in acl of vpn s2s.
Can you config lo ?
Note:- Lo need to route to other peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 06:13 AM
Thank you again for helping.
I believe the ACL is okay. I believe my only problem is the tcp errors.
The 192.168.21.73 is the IP address the ISR will receive for SA and for traffic.
The SA establishes with this configuration and afterwards I can ping from the host to the ISR using the ipsec transport that is established. So both the IKE exchange and the data path works. My problem is that tcp does not work. This would point to an issue at that layer, not the IP layer.
Thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 06:20 AM
Ok' did you check crypto ipsec sa
encrypt and decrypt counter when you ping are the counter increase?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 06:50 AM
Yes I saw encap/decaps increment.
I couldn't figure out how to get the logging to display the tcp checksum errors with the ip addresses. I am reasonably sure that is my issue because the counters increment when I try ssh to the ISR but I couldn't see the logging. Not sure if that is possible. The error will occur
Thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 06:55 AM
Good that excellant'
The counter increase of ipsec sa but you failed to ssh
Then there is issue in nat'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 07:48 AM
also you can show ip tcp <<- see if the tcp session is UP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 07:58 AM
The tcp connection never established.
I tried to do a packet capture using monitor capture, but of course it was encrypted. So all I could really see is packets being sent/received but not content.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 08:00 AM
esp-aes esp-sha-hmac <<- I dont try before but change the ESP to AH, the packet with AH not encrypt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2023 08:55 AM
I have read that AH will not pass through NAT because the integrity check will fail. NAT will modify the IP header.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
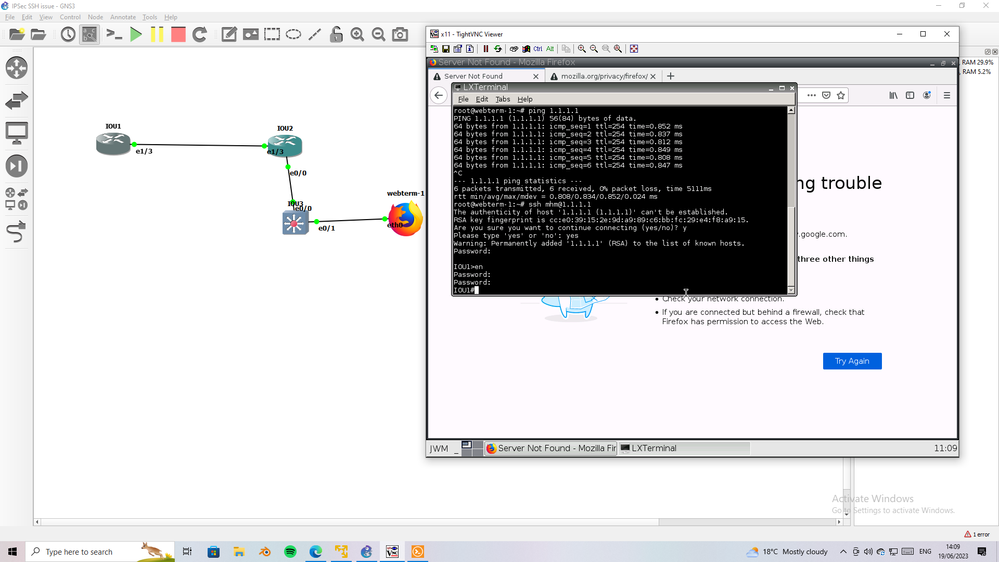
06-19-2023 04:11 AM - edited 07-01-2023 01:58 AM
IOU1(config-line)#
IOU1(config-line)#exit
IOU1(config)#
IOU1(config)#exit
IOU1#
IOU1#
IOU1#show
*Jun 19 11:09:37.623: %SYS-5-CONFIG_I: Configured from console by console
IOU1#show run
IOU1#show running-config
Building configuration...
Current configuration : 2426 bytes
!
! Last configuration change at 11:09:37 UTC Mon Jun 19 2023
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname IOU1
!
boot-start-marker
boot-end-marker
!
!
enable password mhm
!
no aaa new-model
!
!
!
bsd-client server url https://cloudsso.cisco.com/as/token.oauth2
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
!
!
!
!
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
!
!
!
!
!
no ip domain lookup
ip domain name mhm
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
cts logging verbose
!
!
username mhm password 0 mhm
!
redundancy
!
!
ip tcp synwait-time 5
!
!
!
!
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key mhm address 0.0.0.0
!
!
crypto ipsec transform-set mhm esp-des
mode tunnel
!
!
!
crypto map mhm 10 ipsec-isakmp
set peer 100.0.0.2
set transform-set mhm
match address 100
!
!
!
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.255
!
interface Ethernet0/0
no ip address
shutdown
!
interface Ethernet0/1
no ip address
shutdown
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
no ip address
shutdown
!
interface Ethernet1/0
no ip address
shutdown
!
interface Ethernet1/1
no ip address
shutdown
!
interface Ethernet1/2
no ip address
shutdown
!
interface Ethernet1/3
ip address 100.0.0.1 255.255.255.0
crypto map mhm
!
interface Serial2/0
no ip address
shutdown
serial restart-delay 0
!
interface Serial2/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial2/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial2/3
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/0
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/1
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/2
no ip address
shutdown
serial restart-delay 0
!
interface Serial3/3
no ip address
shutdown
serial restart-delay 0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 100.0.0.2
!
!
!
access-list 100 permit ip host 1.1.1.1 20.0.0.0 0.0.0.255
!
control-plane
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login local
transport input ssh
!
!
end
IOU1#
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide