- Cisco Community
- Technology and Support
- Security
- VPN
- Re: cisco ISR4351 ipsec transport peer-to-peer SA tcp checksum errors
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
cisco ISR4351 ipsec transport peer-to-peer SA tcp checksum errors
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2023 08:55 AM
I am configuring an IPSEC transport so that the ISR can send messages to a host which is behind NAT. Mainly for syslog messaging and reporting. I am able to get the SA to establish and from the show crypto commands everything looks great. I can ping form the host or from the ISR and it works. However, I can't ssh in either direction. I see messages sent but the TCP connection does not establish.
When I do show tcp statistics on the ISR, it does show incrementing tcp checksum errors, so I believe the tcp packet is discarded after esp decapsulation. I cannot find a setting on the ISR to configure how checksum is handled. In RFC 3948 there are different methods for handling this. Is anyone aware of how to solve this?
I have read in some posts to disable checksum, but I can't find a way to do that.
Thanks
- Labels:
-
IPSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2023 04:19 AM
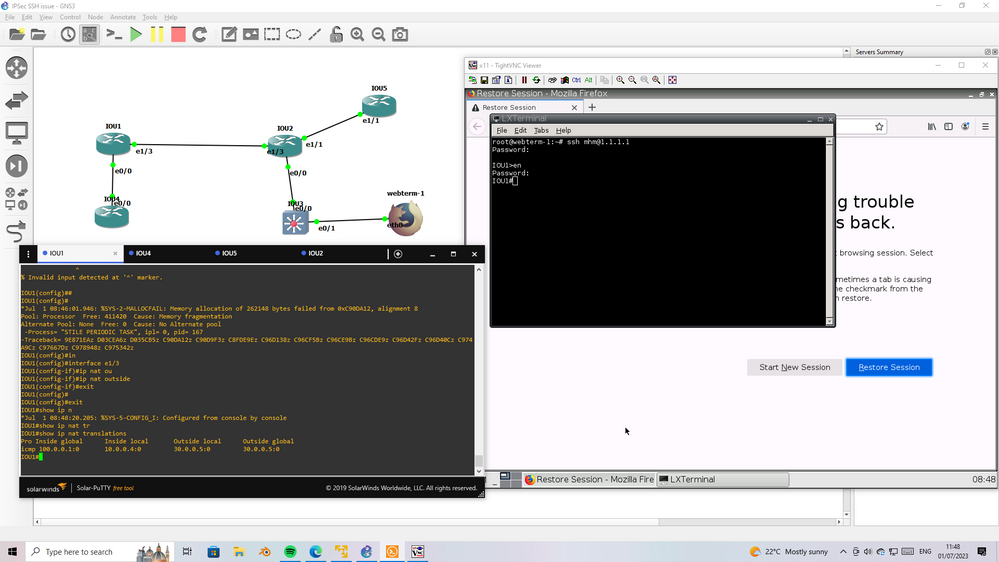
Lab above' you can see I sucess ssh to iou through ipsec tunnel
But I use lo in iou1 not interface I already use as tunnel end.
That point I want to clear to you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2023 09:19 AM
Thanks for the reply. I was out of town last week and could not follow up.
Just to be clear, ssh works fine without NAT using transport mode. My only issue is transport mode with NAT. So are you saying that there is no fix for transport mode and NAT-T? I have to use tunnel mode with NAT?
Is your example working with NAT? I do not understand the peer setting of 100.0.0.2? It would seem like there is no nat?
I am trying to understand how tunnel mode might work for my overall solution. I have syslog and radius configured to my host from the ISR. I believe the source address will be the interface IP. Will tunnel mode work with the interface IP as the inner and outer IP or you are saying it has to use a different interface IP.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2023 01:57 AM
sorry for late reply
it work even if there is NATing in IOU1
the trick here I dont use IP of interface is use for crypto map for access via SSH
I use LO IP to access SSH this SSH traffic pass through tunnel IPsec (use different IP)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2023 01:31 PM
After some trial and error I am able to get tunnel mode to work with and without nat. I can ping and ssh so I believe it will all work for the deployment.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2023 01:49 PM - edited 07-04-2023 01:59 PM
You are so welcome friend
Glad this issue solve in end
By the way did you use LO to access via ssh?
MHM
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide