- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IPsec_ikev2 not starting up in CIsco IOS XE when router is respond
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPsec_ikev2 not starting up in CIsco IOS XE when router is responder
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2024 09:45 AM
Hello Guys,
We have a IKEv2 VPN between Palo Alto FW and Cisco 1121 IOS XE router and below is the Cisco side config. When I initiate traffic towards Cisco end's LAN gateway 172.22.120.1, the tunnel doesnt come up (Phase 1), while it works in the reverse, sending traffic to Palo.
The Palo here, is not configured in passive mode and other clients with Watchguard, Sonicwall etc are able to connect without any issue.
Is there any setting I can change in Cisco router to establish the connection as responder as well?
crypto ikev2 proposal AzureProp
encryption aes-cbc-256
integrity sha256
group 21
exit
crypto ikev2 policy eclipse_policy
proposal AzureProp
exit
crypto ikev2 profile AzurePROF
match identity remote address X.X.X.X X.X.X.X
authentication remote pre-share key Kqxem1fbR5aZTk0pmUAjsaQtN
authentication local pre-share key Kqxem1fbR5aZTk0pmUAjsaQtN
lifetime 28800
exit
crypto ipsec transform-set NEW-TS esp-aes 256 esp-sha256-hmac
mode tunnel
crypto map RTPCLIENT 10 ipsec-isakmp
set peer X.X.X.X
set security-association lifetime seconds 3600
set transform-set NEW-TS
set pfs group14
set ikev2-profile AzurePROF
match address AzureACL
exit
- Labels:
-
IPSEC
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2024 07:12 AM
disable config-exchange request
And check again
Update me when you apply command
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 12:46 PM
Hello @MHM Cisco World ,
Sorry for the late response. I tried it today and generated traffic from Palo End, but it didnt come up. No signs of Phase 1 coming up.
crypto ikev2 profile AzurePROF
match identity remote address 1.1.1.1 255.255.255.255
authentication remote pre-share key XX
authentication local pre-share key XX
lifetime 28800
no config-exchange request
This is the error msg I am seeing in Palo.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 01:00 PM
Show crypto session peer x.x.x.x
Share this
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 01:09 PM
Session status: DOWN
Peer: 1.1.1.1 port 500 fvrf: (none) ivrf: (none)
Desc: (none)
Phase1_id: (none)
IPSEC FLOW: permit ip 172.22.120.0/255.255.255.0 10.54.4.64/255.255.255.240
Active SAs: 0, origin: crypto map
Inbound: #pkts dec'ed 0 drop 0 life (KB/Sec) 0/0
Outbound: #pkts enc'ed 0 drop 0 life (KB/Sec) 0/0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2024 01:40 PM
Ip access-list extended ikev2
Permit udp host <router IP> eq 500 host <peer ip>
Permit udp host <router IP> host <peer ip> eq 500
Debup ip packet ikev2 detail
Check if IOS XE router recieve or not the phase1 ikev2.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2024 01:54 PM
Hello @MHM Cisco World ,
I have allowed port 500 in the access list applied to the WAN interface but I did not see any logs when I ran a debug for IKEv2. Below is my config
interface GigabitEthernet5
description WAN interface
ip address 1.1.1.1 255.255.255.0
ip access-group fromoutside in
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip inspect in2out out
ip virtual-reassembly in
no ip route-cache
duplex auto
speed auto
crypt map RTPCLIENT
end
Extended IP access list fromoutside
------------------
truncated output
------------------
200 permit icmp any any (32688 matches)
210 permit esp any host 1.1.1.1 (81856 matches)
220 permit udp any host 1.1.1.1 eq isakmp (17799 matches)
230 permit gre any host 1.1.1.1 (1 match)
240 permit udp any host 1.1.1.1 eq non500-isakmp (4 matches)
crypt map RTPCLIENT 10 ipsec-isakmp
description Azure - 10.54.4.64/28
set peer 2.2.2.2
set transform-set NEW-TS
set pfs group14
set ikev2-profile AzurePROF
match address AzureACL
Extended IP access list AzureACL
10 permit ip 172.22.120.0 0.0.0.255 10.54.4.64 0.0.0.15
sh debug
IKEV2:
IKEv2 error debugging is on
IKEv2 default debugging is on
IKEv2 packet debugging is on
IKEv2 internal debugging is on
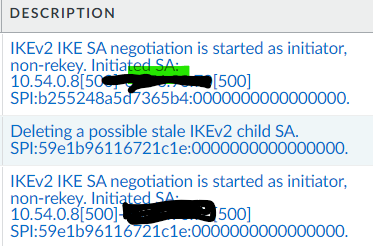
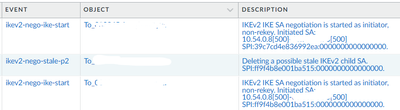
Palo Alto logs:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2024 01:41 AM
I know it, that there is some kind of statefull acl drop incoming.
So can you please do debug I mention before
Debug ikev2 dont show anything if the traffic is drop in ingress interface' i.e. it drop before it reach cpu for analysis.
There is two command
Access group IN and inspection can drop ikev2 packet
But let make sure bu debug I share
And also add
Deny ip any any log
To end of acl and check the log message of deny packet' is it include any packet of ikev2 or not
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 12:15 PM
any update
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide