- Cisco Community
- Technology and Support
- Security
- VPN
- IPSec tunnel encrypt packts but no decrypt
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPSec tunnel encrypt packts but no decrypt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 01:38 AM - edited 04-05-2024 02:34 AM
Hi Community,
We have a newly established IKEV 1 tunnel from Cisco ASA to AWS. This tunnel is currently at up state but the traffic is not passing through the tunnel. When we enter the show command "show crypto ipsec sa peer X.X.X.X" output have encaps decaps correctly but the encrypt and decrypts are not correct.
#pkts encaps: 929, #pkts encrypt: 929, #pkts digest: 929
#pkts decaps: 929, #pkts decrypt: 0, #pkts verify: 0
Also we are checking this by sending ICMP from Local LAN 10.215.130.19 to Remote LAN 172.31.14.115 and we are getting following log on ASA,
4 Mar 27 2024 14:49:59 402116 3.109.169.254 223.224.12.4 IPSEC: Received an ESP packet (SPI= 0x5967E486, sequence number= 0x46) from 3.109.169.254 (user= 3.109.169.254) to 223.224.12.4. The decapsulated inner packet doesn't match the negotiated policy in the SA. The packet specifies its destination as 172.31.14.115, its source as 10.215.130.19, and its protocol as icmp. The SA specifies its local proxy as 10.192.0.0/255.224.0.0/ip/0 and its remote_proxy as 172.31.14.115/255.255.255.255/ip/0.
VPN config
object-group network Shemaroo_LOCAL_LAN_NEW_3_PROD_VPN
network-object 10.192.0.0 255.224.0.0
object-group network Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
network-object host 172.31.14.115
access-list Shemaroo_New_Production extended permit ip object-group Shemaroo_LOCAL_LAN_NEW_3_PROD_VPN object-group Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
tunnel-group xxxxxx type ipsec-l2l
tunnel-group xxxxxx ipsec-attributes
ikev1 pre-shared-key ****
tunnel-group xxxxxx type ipsec-l2l
tunnel-group xxxxxx ipsec-attributes
ikev1 pre-shared-key *****
crypto map Airtel-CRYPTO-MAP 2937 match address Shemaroo_New_Production
crypto map Airtel-CRYPTO-MAP 2937 set pfs group2
crypto map Airtel-CRYPTO-MAP 2937 set peer xxxxx
crypto map Airtel-CRYPTO-MAP 2937 set peer xxxxx
crypto map Airtel-CRYPTO-MAP 2937 set ikev1 transform-set ESP-AES-128-SHA
crypto map Airtel-CRYPTO-MAP 2937 set security-association lifetime seconds 3600
crypto ikev1 policy 4
authentication pre-share
encryption aes
hash sha
group 2
lifetime 28800
Can anyone support on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 01:46 AM
Can you do
Packet-tracer for vpn traffic lan to lan
Also share
Show crypto ipsec sa
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 01:55 AM
Hi MHM,
Kindly find the output
packet-tracer input asA-JuniperVC tcp 10.215.130.19 123 172.31.14.115 8001 ?
bypass-checks Bypass all security checks for simulated packet
decrypted Treat simulated packet as IPsec/SSL VPN decrypted
detailed Dump more detailed information
persist Enable long term tracing and follow tracing in cluster
transmit Allow simulated packet to transmit from device
vxlan-inner Specify inner packet using VLXN encapsulation
xml Output in xml format
| Output modifiers
<cr>
FW-MALI-EXT/pri/act# packet-tracer input asA-JuniperVC tcp 10.215.130.19 123 172.31.14.115 8001 de
FW-MALI-EXT/pri/act# packet-tracer input asA-JuniperVC tcp 10.215.130.19 123 172.31.14.115 8001 det
FW-MALI-EXT/pri/act# packet-tracer input asA-JuniperVC tcp 10.215.130.19 123 172.31.14.115 8001 detailed
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01ccbebc20, priority=13, domain=capture, deny=false
hits=163766504, user_data=0x7f01cda6ad80, cs_id=0x0, l3_type=0x0
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
input_ifc=ASA-JuniperVC, output_ifc=any
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024c8c6d50, priority=1, domain=permit, deny=false
hits=643500579642, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=ASA-JuniperVC, output_ifc=any
Phase: 3
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 223.224.12.3 using egress ifc INTERNET_ZONE
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group ASA-JuniperVC_access_in in interface ASA-JuniperVC
access-list ASA-JuniperVC_access_in remark ISP-2024-March-ISP-3090
access-list ASA-JuniperVC_access_in extended permit object-group DM_INLINE_SERVICE_2153 object-group DM_INLINE_NETWORK_2149 object-group DM_INLINE_NETWORK_2153
object-group service DM_INLINE_SERVICE_2153
service-object icmp
service-object object TCP_8001
object-group network DM_INLINE_NETWORK_2149
network-object host 10.215.130.16
network-object host 10.215.130.17
network-object host 10.215.130.18
network-object host 10.215.130.19
network-object host 10.215.130.38
object-group network DM_INLINE_NETWORK_2153
group-object Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
network-object object obj-10.200.167.232
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01a84a39d0, priority=13, domain=permit, deny=false
hits=5, user_data=0x7f02243f9c00, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=10.215.130.19, mask=255.255.255.255, port=0, tag=any
dst ip/id=172.31.14.115, mask=255.255.255.255, port=8001, tag=any, dscp=0x0
input_ifc=ASA-JuniperVC, output_ifc=any
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01c20927f0, priority=0, domain=nat-per-session, deny=false
hits=2350903612, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024c940f60, priority=0, domain=inspect-ip-options, deny=true
hits=1500502753, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=ASA-JuniperVC, output_ifc=any
Phase: 7
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group ASA-JuniperVC_access_in in interface ASA-JuniperVC
access-list ASA-JuniperVC_access_in remark ISP-2024-March-ISP-3090
access-list ASA-JuniperVC_access_in extended permit object-group DM_INLINE_SERVICE_2153 object-group DM_INLINE_NETWORK_2149 object-group DM_INLINE_NETWORK_2153
object-group service DM_INLINE_SERVICE_2153
service-object icmp
service-object object TCP_8001
object-group network DM_INLINE_NETWORK_2149
network-object host 10.215.130.16
network-object host 10.215.130.17
network-object host 10.215.130.18
network-object host 10.215.130.19
network-object host 10.215.130.38
object-group network DM_INLINE_NETWORK_2153
group-object Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
network-object object obj-10.200.167.232
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01a84a39d0, priority=13, domain=permit, deny=false
hits=6, user_data=0x7f02243f9c00, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=10.215.130.19, mask=255.255.255.255, port=0, tag=any
dst ip/id=172.31.14.115, mask=255.255.255.255, port=8001, tag=any, dscp=0x0
input_ifc=ASA-JuniperVC, output_ifc=any
Phase: 8
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01c20927f0, priority=0, domain=nat-per-session, deny=false
hits=2350903612, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 9
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024c940f60, priority=0, domain=inspect-ip-options, deny=true
hits=1500502753, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=ASA-JuniperVC, output_ifc=any
Phase: 10
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024cc98c50, priority=20, domain=lu, deny=false
hits=190502541, user_data=0x0, cs_id=0x0, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=ASA-JuniperVC, output_ifc=any
Phase: 11
Type: VPN
Subtype: encrypt
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f01b0ef2940, priority=70, domain=encrypt, deny=false
hits=2, user_data=0x75a0e82c, cs_id=0x7f01ca2a62e0, reverse, flags=0x0, protocol=0
src ip/id=10.192.0.0, mask=255.224.0.0, port=0, tag=any
dst ip/id=172.31.14.115, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=INTERNET_ZONE
Phase: 12
Type:
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f01d6ba4a40, priority=13, domain=dynamic-filter, deny=false
hits=1855556950, user_data=0x7f01d6ba44e0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=INTERNET_ZONE
Phase: 13
Type: NAT
Subtype: rpf-check
Result: DROP
Config:
nat (INTERNET_ZONE,ASA-JuniperVC) source static Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN obj-10.200.167.232 destination static DM_INLINE_NETWORK_2146 DM_INLINE_NETWORK_2146
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f01cab1aee0, priority=6, domain=nat-reverse, deny=false
hits=7, user_data=0x7f01b0369400, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=10.215.130.19, mask=255.255.255.255, port=0, tag=any
dst ip/id=172.31.14.115, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=ASA-JuniperVC, output_ifc=INTERNET_ZONE
Result:
input-interface: ASA-JuniperVC
input-status: up
input-line-status: up
output-interface: INTERNET_ZONE
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
FW-MALI-EXT/pri/act#
t# show crypto ipsec sa peer 3.111.106.37
peer address: 3.111.106.37
Crypto map tag: Airtel-CRYPTO-MAP, seq num: 2101, local addr: 223.224.12.4
access-list Shemaroo_New_Production extended permit ip 10.192.0.0 255.224.0.0 host 172.31.14.115
local ident (addr/mask/prot/port): (10.192.0.0/255.224.0.0/0/0)
remote ident (addr/mask/prot/port): (172.31.14.115/255.255.255.255/0/0)
current_peer: 3.111.106.37
#pkts encaps: 267, #pkts encrypt: 267, #pkts digest: 267
#pkts decaps: 247, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 267, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 247
local crypto endpt.: 223.224.12.4/4500, remote crypto endpt.: 3.111.106.37/4500
path mtu 1500, ipsec overhead 82(52), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: CD53F1E7
current inbound spi : FB2CD048
inbound esp sas:
spi: 0xFB2CD048 (4214018120)
SA State: active
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, PFS Group 2, IKEv1, }
slot: 0, conn_id: 404579, crypto-map: Airtel-CRYPTO-MAP
sa timing: remaining key lifetime (kB/sec): (4374000/3332)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0xCD53F1E7 (3444830695)
SA State: active
transform: esp-aes esp-sha-hmac no compression
in use settings ={L2L, Tunnel, NAT-T-Encaps, PFS Group 2, IKEv1, }
slot: 0, conn_id: 404579, crypto-map: Airtel-CRYPTO-MAP
sa timing: remaining key lifetime (kB/sec): (4373978/3332)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
FW-MALI-EXT/pri/act#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 02:04 AM
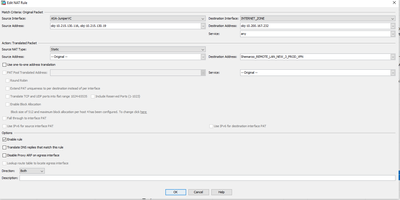
Swapping the interface and object in no-NAT you use for VPN traffic
nat (ASA-JuniperVC,INTERNET_ZONE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 02:24 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 03:20 AM
Can you do packet tracer one more time share result here
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2024 03:22 AM
One more point
You use in packet trace subnet start with 172.x.x.x and this not same use in no-NAT?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2024 01:14 AM
Hi MHM,
Sorry for the delay. I do not understand this question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2024 06:58 AM - edited 03-31-2024 07:00 AM
object-group network Shemaroo_LOCAL_LAN_NEW_3_PROD_VPN
network-object 10.192.0.0 255.224.0.0
object-group network Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
network-object host 172.31.14.115
access-list Shemaroo_New_Production extended permit ip object-group Shemaroo_LOCAL_LAN_NEW_3_PROD_VPN object-group Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
The NAT (we called it no-NAT or exception NAT) is not match the secure traffic?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2024 11:54 PM
Hi MHM,
To troubleshoot this issue we have changed the VPN to IKEV 2 and we are now using a LOCAL_LAN that is connected to firewall with no nat involved. Still we are getting the same error.
4 Apr 01 2024 12:21:36 402116 3.109.169.254 223.224.12.4 IPSEC: Received an ESP packet (SPI= 0x5525197C, sequence number= 0x71) from 3.109.169.254 (user= 3.109.169.254) to 223.224.12.4. The decapsulated inner packet doesn't match the negotiated policy in the SA. The packet specifies its destination as 172.31.14.115, its source as 10.200.190.12, and its protocol as icmp. The SA specifies its local proxy as 10.200.190.12/255.255.255.255/ip/0 and its remote_proxy as 172.31.14.115/255.255.255.255/ip/0.
access-list Shemaroo_New_Production line 1 extended permit ip object-group Shemaroo_LOCAL_LAN_NEW_3_PROD_VPN object-group Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN (hitcnt=6) 0x90632134
FW-MALI-EXT/pri/act#
FW-MALI-EXT/pri/act# show object-group id Shemaroo_LOCAL_LAN_NEW_3_PROD_VPN
object-group network Shemaroo_LOCAL_LAN_NEW_3_PROD_VPN
network-object host 10.200.190.12
FW-MALI-EXT/pri/act#
FW-MALI-EXT/pri/act# show object-group id Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
object-group network Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
network-object host 172.31.14.115
FW-MALI-EXT/pri/act#
packet tracer result...
FW-MALI-EXT/pri/act# packet-tracer input MGMT_SERVERS_ZONE TCP 10.200.190.12 123 172.31.14.115 8001 detailed
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024d7403e0, priority=1, domain=permit, deny=false
hits=2497126106, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=MGMT_SERVERS_ZONE, output_ifc=any
Phase: 2
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 223.224.12.3 using egress ifc INTERNET_ZONE
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group MGMT_SERVERS_Inbound in interface MGMT_SERVERS_ZONE
access-list MGMT_SERVERS_Inbound remark test
access-list MGMT_SERVERS_Inbound extended permit ip object-group MGMT_SERVERS_SUBNET object-group Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
object-group network MGMT_SERVERS_SUBNET
network-object object obj-10.200.190.10
network-object object obj-10.200.190.11
network-object object obj-10.200.190.12
network-object object obj-10.200.190.13
network-object object obj-10.200.190.14
network-object object obj-10.200.190.15
network-object object obj-10.200.190.9
object-group network Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
network-object host 172.31.14.115
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01a8ee0f00, priority=13, domain=permit, deny=false
hits=1, user_data=0x7f02243f9e40, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=10.200.190.12, mask=255.255.255.255, port=0, tag=any
dst ip/id=172.31.14.115, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=MGMT_SERVERS_ZONE, output_ifc=any
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
object network obj-10.200.190.8
nat (MGMT_SERVERS_ZONE,INTERNET_ZONE) static 10.200.190.8
Additional Information:
Static translate 10.200.190.12/123 to 10.200.190.12/123
Forward Flow based lookup yields rule:
in id=0x7f01a86cf050, priority=6, domain=nat, deny=false
hits=2345, user_data=0x7f01a86ce390, cs_id=0x0, flags=0x0, protocol=0
src ip/id=10.200.190.8, mask=255.255.255.248, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=MGMT_SERVERS_ZONE, output_ifc=INTERNET_ZONE
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01c20927f0, priority=0, domain=nat-per-session, deny=false
hits=2378778012, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024d747400, priority=0, domain=inspect-ip-options, deny=true
hits=78998446, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=MGMT_SERVERS_ZONE, output_ifc=any
Phase: 7
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group MGMT_SERVERS_Inbound in interface MGMT_SERVERS_ZONE
access-list MGMT_SERVERS_Inbound remark test
access-list MGMT_SERVERS_Inbound extended permit ip object-group MGMT_SERVERS_SUBNET object-group Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
object-group network MGMT_SERVERS_SUBNET
network-object object obj-10.200.190.10
network-object object obj-10.200.190.11
network-object object obj-10.200.190.12
network-object object obj-10.200.190.13
network-object object obj-10.200.190.14
network-object object obj-10.200.190.15
network-object object obj-10.200.190.9
object-group network Shemaroo_REMOTE_LAN_NEW_3_PROD_VPN
network-object host 172.31.14.115
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01a8ee0f00, priority=13, domain=permit, deny=false
hits=2, user_data=0x7f02243f9e40, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=10.200.190.12, mask=255.255.255.255, port=0, tag=any
dst ip/id=172.31.14.115, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=MGMT_SERVERS_ZONE, output_ifc=any
Phase: 8
Type: NAT
Subtype:
Result: ALLOW
Config:
object network obj-10.200.190.8
nat (MGMT_SERVERS_ZONE,INTERNET_ZONE) static 10.200.190.8
Additional Information:
Static translate 10.200.190.12/123 to 10.200.190.12/123
Forward Flow based lookup yields rule:
in id=0x7f01a86cf050, priority=6, domain=nat, deny=false
hits=2345, user_data=0x7f01a86ce390, cs_id=0x0, flags=0x0, protocol=0
src ip/id=10.200.190.8, mask=255.255.255.248, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=MGMT_SERVERS_ZONE, output_ifc=INTERNET_ZONE
Phase: 9
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f01c20927f0, priority=0, domain=nat-per-session, deny=false
hits=2378778012, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 10
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024d747400, priority=0, domain=inspect-ip-options, deny=true
hits=78998446, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=MGMT_SERVERS_ZONE, output_ifc=any
Phase: 11
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f024d73ba90, priority=20, domain=lu, deny=false
hits=21476, user_data=0x0, cs_id=0x0, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=MGMT_SERVERS_ZONE, output_ifc=any
Phase: 12
Type: VPN
Subtype: encrypt
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f01cc648c40, priority=70, domain=encrypt, deny=false
hits=76, user_data=0x4ecd306c, cs_id=0x7f01cc6147a0, reverse, flags=0x0, protocol=0
src ip/id=10.200.190.12, mask=255.255.255.255, port=0, tag=any
dst ip/id=172.31.14.115, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=INTERNET_ZONE
Phase: 13
Type:
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f01d6ba4a40, priority=13, domain=dynamic-filter, deny=false
hits=1872935297, user_data=0x7f01d6ba44e0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=INTERNET_ZONE
Phase: 14
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f01d70e7b10, priority=0, domain=user-statistics, deny=false
hits=5283879235, user_data=0x7f01d6dd4ab0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=INTERNET_ZONE
Phase: 15
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f01a88efba0, priority=70, domain=ipsec-tunnel-flow, deny=false
hits=76, user_data=0x505f58cc, cs_id=0x7f01cc6147a0, reverse, flags=0x0, protocol=0
src ip/id=172.31.14.115, mask=255.255.255.255, port=0, tag=any
dst ip/id=10.200.190.12, mask=255.255.255.255, port=0, tag=any, dscp=0x0
input_ifc=INTERNET_ZONE, output_ifc=any
Phase: 16
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f01c20927f0, priority=0, domain=nat-per-session, deny=false
hits=2378778014, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 17
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f01ca31bc00, priority=0, domain=inspect-ip-options, deny=true
hits=4134551911, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=INTERNET_ZONE, output_ifc=any
Phase: 18
Type: USER-STATISTICS
Subtype: user-statistics
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
out id=0x7f01d70ea9f0, priority=0, domain=user-statistics, deny=false
hits=95269653, user_data=0x7f01d6dd4ab0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=MGMT_SERVERS_ZONE
Phase: 19
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 2565679808, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_encrypt
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
snp_fp_translate
Result:
input-interface: MGMT_SERVERS_ZONE
input-status: up
input-line-status: up
output-interface: INTERNET_ZONE
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2024 10:27 AM
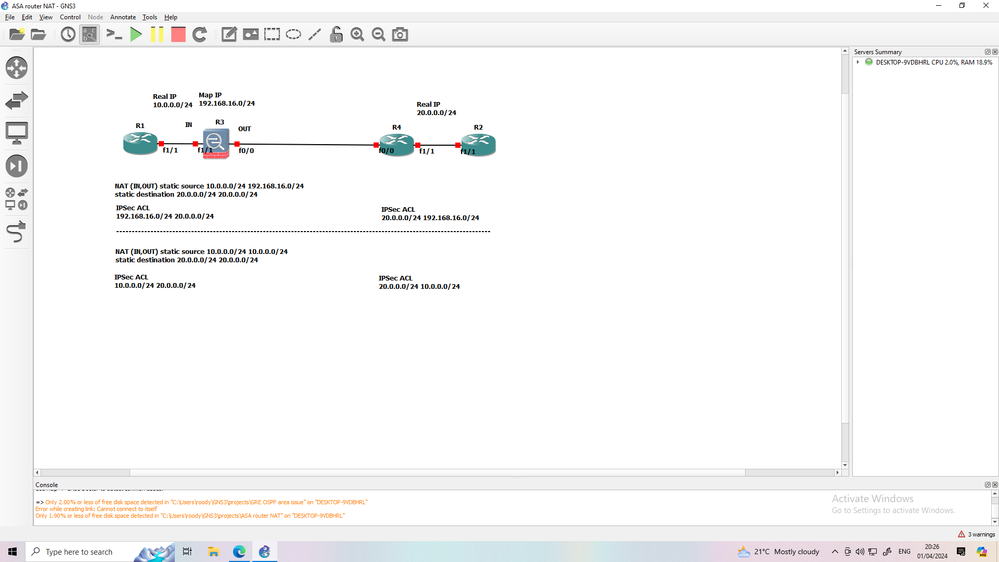
this is what you need in case you used mapped IP or case use real IP in ACL of IPsec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2024 04:54 AM
your configuration look fine as you can see from your output that yours firewall is doing the encap but in regards to decrypt not much. which lead me to think that firewall is doing encap and sending the traffic to AWS. but seem that could be an issue at AWS. did you sent up the connection on AWS as policy based vpn or route based vpn? I think issue is more likely at the AWS side not you.
#pkts encaps: 267, #pkts encrypt: 267, #pkts digest: 267
#pkts decaps: 247, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 267, #pkts comp failed: 0, #pkts decomp failed: 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2024 08:36 AM
Hi Sheraz,
AWS side configurations done by outside party. We are currently checking the issue with them. Also we have observed a strange behavior, when they sent and ICMP request from AWS vPC 172.31.14.115 to our local lan IP 10.215.130.116 that icmp request is going through the tunnel and reaching the our local server, replay also coming upto the peer firewall. And we are getting the same log on firewall for the reply packet mentioning The decapsulated inner packet doesn't match the negotiated policy in the SA. Can you explain this behavior?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2024 09:12 AM
As I understand you NATing traffic before it encrypt by IPSec' if yes check note I share above.
You need to adjust acl in aws to match what you config in ASA (real or mapped ip) also one more note you need to check if AWS have route for noth real and mapped IP toward your ASA or through Interface encrypt traffic.
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide