- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Failed Radius requests increase possible?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Failed Radius requests increase possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2015 07:53 AM - edited 07-05-2021 03:18 AM
Hello
We have a Cisco WLC 7.0.240.0 based infrastructure with Radius servers and a Windows domain. Some clients are joined, some are BYOD. Our SSID is protected with WPA2-Enterprise PEAP-MSCHAPv2 username/password authentication. No certificate and no machine authentication.
Now Windows default behavior, for devices joined to some domain, is to send the machine name as username when connecting the first few tries and only later the logged in username/password.
My WLC will block the client because of excessive, wrong authentication tries for a few seconds. This makes it impossible to join the client automatically, without manually creating the wifi-profile and disabling the "automatic machine or user authentication" option.
It looks like the WLC will block the client after 3 unsuccessful authentication tries.
Is there a way to increase those 3 to maybe 5 or 10? I have the hope that this is enough for Windows to change to the username/password combo instead of machine name.
Thanks
Patrick
- Labels:
-
Other Wireless Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2015 08:24 AM
You can adjust the number of attempts a client makes before it gets excluded...
HTH,
Steve
Steve
------------------------------------------------------------------------------------------------
Please remember to rate useful posts, and mark questions as answered
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2015 10:40 PM
Hmm based on your link:
So the maximum seems to be only 3 :(
Oh and that command is not available for 7.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2015 01:55 AM
Hi,
Yes config wps client-exclusion 802.1x-auth max-1x-aaa-fail-attempts is not available in 7.0 code.
Using the GUI to Configure Client Exclusion Policies
To configure client exclusion policies using the controller GUI, follow these steps:
Step 1 ![]() Choose Security > Wireless Protection Policies > Client Exclusion Policies
Choose Security > Wireless Protection Policies > Client Exclusion Policies
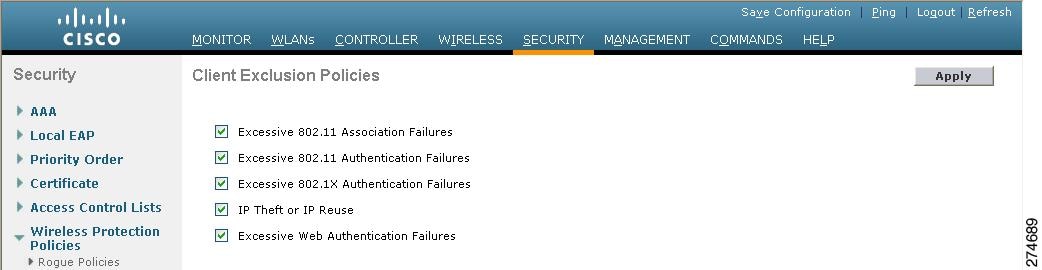
Step 2 ![]() Select any of these check boxes if you want the controller to exclude clients for the condition specified. The default value for each exclusion policy is enabled.
Select any of these check boxes if you want the controller to exclude clients for the condition specified. The default value for each exclusion policy is enabled.
•![]() Excessive 802.11 Association Failures—Clients are excluded on the sixth 802.11 association attempt, after five consecutive failures.
Excessive 802.11 Association Failures—Clients are excluded on the sixth 802.11 association attempt, after five consecutive failures.
•![]() Excessive 802.11 Authentication Failures—Clients are excluded on the sixth 802.11 authentication attempt, after five consecutive failures.
Excessive 802.11 Authentication Failures—Clients are excluded on the sixth 802.11 authentication attempt, after five consecutive failures.
•![]() Excessive 802.1X Authentication Failures—Clients are excluded on the fourth 802.1X authentication attempt, after three consecutive failures.
Excessive 802.1X Authentication Failures—Clients are excluded on the fourth 802.1X authentication attempt, after three consecutive failures.
•![]() IP Theft or IP Reuse—Clients are excluded if the IP address is already assigned to another device.
IP Theft or IP Reuse—Clients are excluded if the IP address is already assigned to another device.
•![]() Excessive Web Authentication Failures—Clients are excluded on the fourth web authentication attempt, after three consecutive failures.
Excessive Web Authentication Failures—Clients are excluded on the fourth web authentication attempt, after three consecutive failures.
Step 3 ![]() Click Apply to commit your changes.
Click Apply to commit your changes.
Step 4 ![]() Click Save Configuration to save your changes.
Click Save Configuration to save your changes.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
