- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: Wireless security and scanning
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Wireless security and scanning
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2022 12:46 PM - edited 03-31-2022 02:16 PM
We have deployed our wireless setup - WLC 3504 -> AP3800 series -> Cisco ISE -> CORP-Wireless with Certificate. Everything is working as expected. However, our security engineer has scanned using ''airmon-ng" scanning & logging all access point & client device broadcasts. He is was then able to gather details on the LDAP user and the specific OU where the user resides along with the PKI details -
ldap:///CN=CA,CN=CA,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=xxx,DC=com? Btw, I am using EAP-TLS for the authentication.
Is this normal that such details are in plaintext? What specific security parameter can be configured to mitigate this information sharing via a scan?
- Labels:
-
Wireless Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 01:52 AM
Seems like this is not an issue but it's a normal part of the EAP-Identity Response frame send by Supplicant and this outer identity is in cleartext.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 04:06 AM
There is solution for that but the problem in Wi-Fi network is all the same: Client compatibilty. You can enable MFP (Management Frame protection) and this will cryptographic managements frames between AP and Clients. The problem is that,most probably , your clients does not support MFP and if they dont and you enable it on the WLC, they will all drop from the network cause they will not undestand management frame anymore.
You can also play with wpa3 which is more secure then wpa2 but the same problem, your clients will not support it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 05:32 AM
Hi @Flavio Miranda, thanks for the feedback. I did enable MFP (Management Frame protection) last night and this morning some clients were not able to connect. Windows 10 version 2004 supports WPA3 but I know it is mandatory to support MFP and client and AP has to negotiate it. Will have to do some testing and see.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 05:45 AM
That´s great. Honestly I never dare to enable this feature due clients incompatibility. The same for wpa3.
But, if you had the chance and can handle this situation inside the company, that´s greate and keep we posted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2022 06:21 AM - edited 04-01-2022 06:25 AM
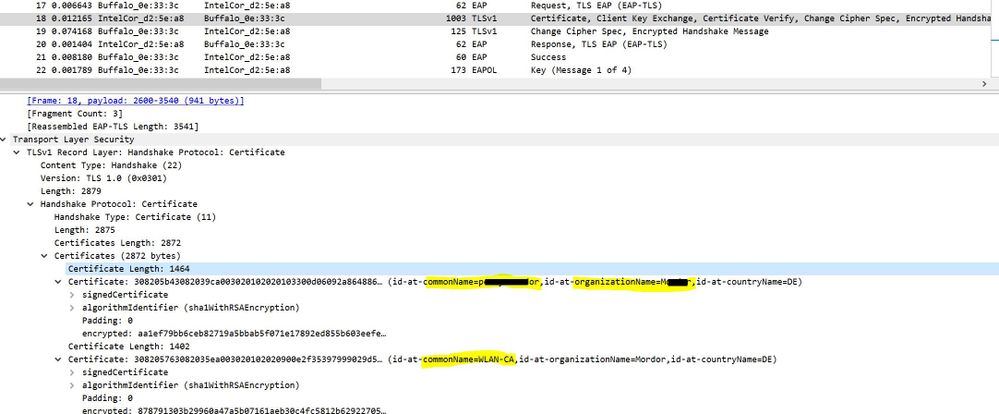
some of this information is also present in client certificate, you can get it simply by wireshark capture over air, see the example enclosed where one can see client information that you mentioned over wireless.
As other mentioned MFP and WPA3 will address some the issues related to protecting management frame exchange.
the information itself can not be used for authentication, but can certainly be useful for reconnaissance
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide