- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE VPN Client-Provisioning-Portal doesn't work with DACL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2016 03:58 PM
On our ASA we have over a 100 group policies and each group policy has their own ACL(vpn-filter). During the unknown or non-compliance stage I am looking to push down a DACL via ISE so that I can control where they are able to go, mainly the ISE servers and remediation servers. If I don't push down a DACL than those users who are connecting and are in non-compliance can still access resources based on the vpn-filter assigned to the group-policy.
Problem:
I am running ISE 2.0 with Cisco ASA 9.5.2(6). When I apply a DACL with anything other than ip any any to my authc profile, my users are not redirected to the provisioning portal. In the Wireshark captures I see that the url-redirect has been sent and I can even copy the url-redirect which has been applied to my session into my browsers and I am able to load the portal.
If I remove the DACL or like I said earlier, use ip any any in the DACL I am properly redirected.
Does anyone else use DACLs in this manner? Am I running into a bug with this version of code?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2016 07:02 PM
To discover ISE, ISE posture module probes ise.cisco.com URL to detect if redirection is needed.
You can also define a specific discovery host in ISE posture agent profile to force the agent to go to some specific website on the intranet. You then have to whitelist the ip address of that host in the DACL. When posture module connects there, the ASA redirects and you go through the posture process.
You can generate the DART bundle and examine ISE posture logs to see the details of what the module is trying to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2016 07:02 PM
To discover ISE, ISE posture module probes ise.cisco.com URL to detect if redirection is needed.
You can also define a specific discovery host in ISE posture agent profile to force the agent to go to some specific website on the intranet. You then have to whitelist the ip address of that host in the DACL. When posture module connects there, the ASA redirects and you go through the posture process.
You can generate the DART bundle and examine ISE posture logs to see the details of what the module is trying to do.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2016 08:05 PM
A small correction to Viktor Bobrov's response. AnyConnect ISE posture will probe enroll.cisco.com by default.
If FireFox on your client machine, you may try the Network Monitor from its developer tools collection to see how the web requests are spending their time.
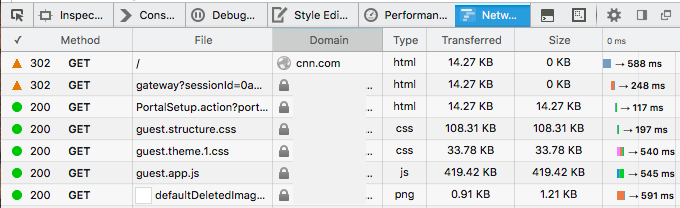
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2016 01:22 PM
That makes perfect sense, Thank you. I have added the rules for both 80 and 443 to the DACL and the redirect is working as expected.
Have you used the redirect with Proxy being set? In doing further testing, I noticed that if we use port 8080 as our proxy port the redirect won't happen as it's a non-standard HTTP port which can't be used for redirect. The obvious choice it to change it from 8080 to 80, but that doesn't seem like the correct path.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2016 08:28 PM
I believe ASA supporting URL redirects on TCP port 80 only. Even if it supports a proxy port, you might need some workaround/non-standard way to set the DiscoveryHost for the ISE posture.
As a better user experience, we usually recommend to have ASA web deploy to install ISE posture module, besides other AnyConnect modules, and then have ISE to deploy the ISE compliance module.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: