- Cisco Community
- Technology and Support
- DevNet Hub
- DevNet Services
- Services Discussions
- Querying openVuln API using Date Ranges
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2017 10:26 AM
You can now query advisories (CVRF) and OVAL definitions using a "first published" date range, as shown below:
https://api.cisco.com/security/advisories/cvrf/all/firstpublished?startDate=2017-01-01&endDate=2017-02-15
https://api.cisco.com/security/advisories/oval/all/firstpublished?startDate=2017-01-01&endDate=2017-02-15
You can also query using the advisories that were updated in a given date range, as demonstrated below:
https://api.cisco.com/security/advisories/cvrf/all/lastpublished?startDate=2017-01-01&endDate=2017-02-15 https://api.cisco.com/security/advisories/oval/all/lastpublished?startDate=2017-01-01&endDate=2017-02-15
The same concept applies when querying advisories that have a given security impact rating:
https://api.cisco.com/security/advisories/cvrf/severity/critical/lastpublished?startDate=2017-01-01&endDate=2017-02-15
https://api.cisco.com/security/advisories/cvrf/severity/high/firstpublished?startDate=2017-01-01&endDate=2017-02-15
This is also documented at: https://developer.cisco.com/site/PSIRT/get-started/getting-started.gsp
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2017 03:13 PM
Hi Walter,
QQ: Are you using Postman? You should definitely not be seeing a 500 back. I also just tested with Postman. The only difference when you use postman is that you need to specify .json in the URL, as I include in the screenshot below.
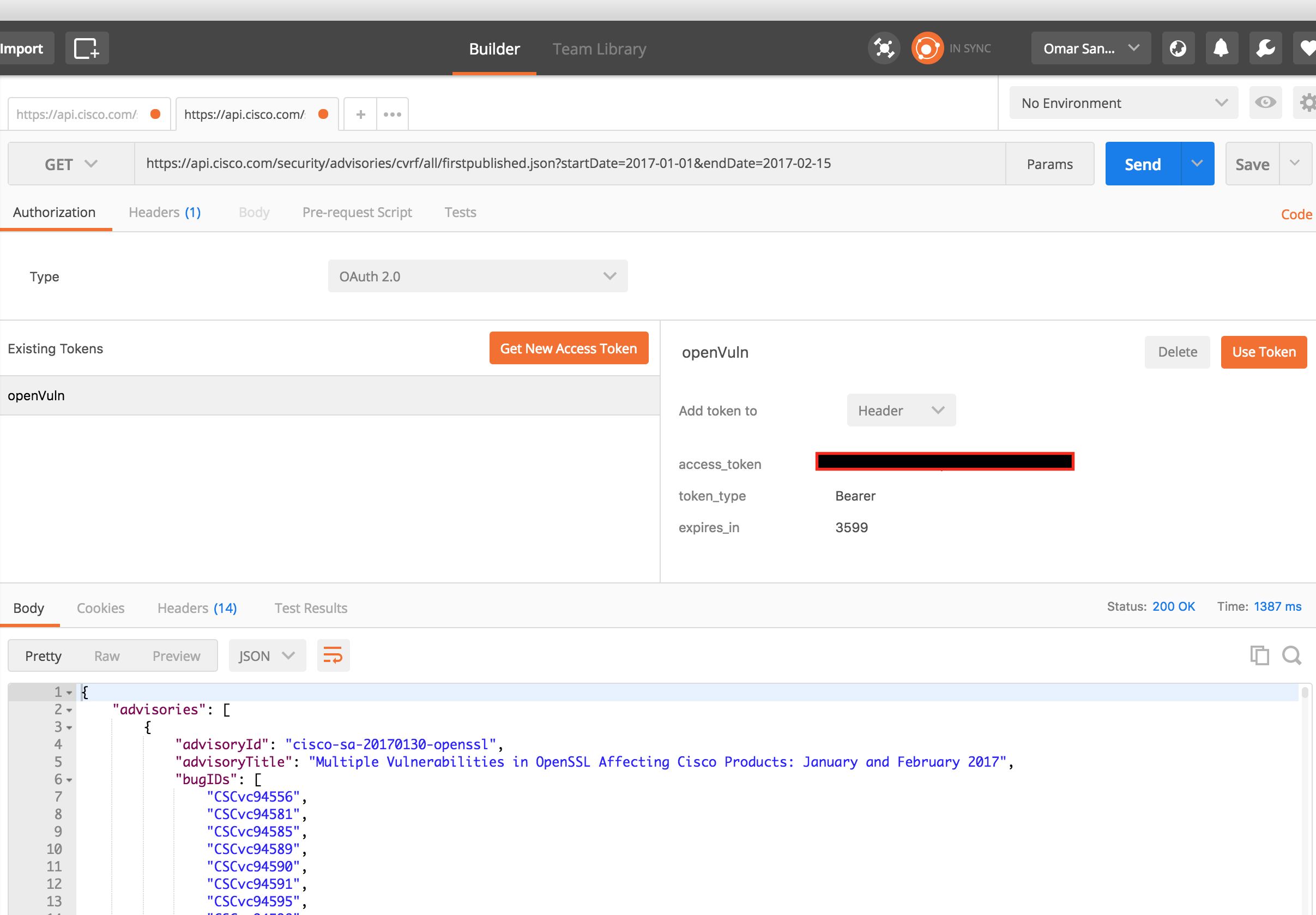
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2017 01:46 PM
I was attempting to specify a date range, as described on https://developer.cisco.com/site/PSIRT/get-started/getting-started.gsp under “Querying Using a Date Range”, I ran into some issues. It seems the only response to any date-range query is a web page referencing “internal error” (see below).
HTTP Status 500 - org.apache.cxf.interceptor.Fault
type Exception report
message org.apache.cxf.interceptor.Fault
description The server encountered an internal error that prevented it from fulfilling this request.
exception
java.lang.RuntimeException: org.apache.cxf.interceptor.Fault org.apache.cxf.interceptor.AbstractFaultChainInitiatorObserver.onMessage(AbstractFaultChainInitiatorObserver.java:116) org.apache.cxf.phase.PhaseInterceptorChain.doIntercept(PhaseInterceptorChain.java:371) org.apache.cxf.transport.ChainInitiationObserver.onMessage(ChainInitiationObserver.java:121) org.apache.cxf.transport.http.AbstractHTTPDestination.invoke(AbstractHTTPDestination.java:243) org.apache.cxf.transport.servlet.ServletController.invokeDestination(ServletController.java:223) org.apache.cxf.transport.servlet.ServletController.invoke(ServletController.java:197) org.apache.cxf.transport.servlet.ServletController.invoke(ServletController.java:149) org.apache.cxf.transport.servlet.CXFNonSpringServlet.invoke(CXFNonSpringServlet.java:171) org.apache.cxf.transport.servlet.AbstractHTTPServlet.handleRequest(AbstractHTTPServlet.java:286) org.apache.cxf.transport.servlet.AbstractHTTPServlet.doGet(AbstractHTTPServlet.java:211) javax.servlet.http.HttpServlet.service(HttpServlet.java:620) org.apache.cxf.transport.servlet.AbstractHTTPServlet.service(AbstractHTTPServlet.java:262) org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
root cause
org.apache.cxf.interceptor.Fault org.apache.cxf.service.invoker.AbstractInvoker.createFault(AbstractInvoker.java:163) org.apache.cxf.service.invoker.AbstractInvoker.invoke(AbstractInvoker.java:129) org.apache.cxf.jaxrs.JAXRSInvoker.invoke(JAXRSInvoker.java:211) org.apache.cxf.jaxrs.JAXRSInvoker.invoke(JAXRSInvoker.java:99) org.apache.cxf.interceptor.ServiceInvokerInterceptor$1.run(ServiceInvokerInterceptor.java:59) org.apache.cxf.interceptor.ServiceInvokerInterceptor.handleMessage(ServiceInvokerInterceptor.java:96) org.apache.cxf.phase.PhaseInterceptorChain.doIntercept(PhaseInterceptorChain.java:307) org.apache.cxf.transport.ChainInitiationObserver.onMessage(ChainInitiationObserver.java:121) org.apache.cxf.transport.http.AbstractHTTPDestination.invoke(AbstractHTTPDestination.java:243) org.apache.cxf.transport.servlet.ServletController.invokeDestination(ServletController.java:223) org.apache.cxf.transport.servlet.ServletController.invoke(ServletController.java:197) org.apache.cxf.transport.servlet.ServletController.invoke(ServletController.java:149) org.apache.cxf.transport.servlet.CXFNonSpringServlet.invoke(CXFNonSpringServlet.java:171) org.apache.cxf.transport.servlet.AbstractHTTPServlet.handleRequest(AbstractHTTPServlet.java:286) org.apache.cxf.transport.servlet.AbstractHTTPServlet.doGet(AbstractHTTPServlet.java:211) javax.servlet.http.HttpServlet.service(HttpServlet.java:620) org.apache.cxf.transport.servlet.AbstractHTTPServlet.service(AbstractHTTPServlet.java:262) org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
root cause
java.lang.NullPointerException com.cisco.csc.rest.util.DateHandler.checkDateFormat(DateHandler.java:27) com.cisco.csc.rest.controller.OpenVulServiceEndpointImpl.getAdvisoriesByFirstPublishedIncvrfFormat(OpenVulServiceEndpointImpl.java:356) sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method) sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:57) sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) java.lang.reflect.Method.invoke(Method.java:606) org.apache.cxf.service.invoker.AbstractInvoker.performInvocation(AbstractInvoker.java:181) org.apache.cxf.service.invoker.AbstractInvoker.invoke(AbstractInvoker.java:97) org.apache.cxf.jaxrs.JAXRSInvoker.invoke(JAXRSInvoker.java:211) org.apache.cxf.jaxrs.JAXRSInvoker.invoke(JAXRSInvoker.java:99) org.apache.cxf.interceptor.ServiceInvokerInterceptor$1.run(ServiceInvokerInterceptor.java:59) org.apache.cxf.interceptor.ServiceInvokerInterceptor.handleMessage(ServiceInvokerInterceptor.java:96) org.apache.cxf.phase.PhaseInterceptorChain.doIntercept(PhaseInterceptorChain.java:307) org.apache.cxf.transport.ChainInitiationObserver.onMessage(ChainInitiationObserver.java:121) org.apache.cxf.transport.http.AbstractHTTPDestination.invoke(AbstractHTTPDestination.java:243) org.apache.cxf.transport.servlet.ServletController.invokeDestination(ServletController.java:223) org.apache.cxf.transport.servlet.ServletController.invoke(ServletController.java:197) org.apache.cxf.transport.servlet.ServletController.invoke(ServletController.java:149) org.apache.cxf.transport.servlet.CXFNonSpringServlet.invoke(CXFNonSpringServlet.java:171) org.apache.cxf.transport.servlet.AbstractHTTPServlet.handleRequest(AbstractHTTPServlet.java:286) org.apache.cxf.transport.servlet.AbstractHTTPServlet.doGet(AbstractHTTPServlet.java:211) javax.servlet.http.HttpServlet.service(HttpServlet.java:620) org.apache.cxf.transport.servlet.AbstractHTTPServlet.service(AbstractHTTPServlet.java:262) org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
note The full stack trace of the root cause is available in the Apache Tomcat/7.0.54 logs.
Apache Tomcat/7.0.54
Current question: Is there an alternative method to obtain a date-range query, or is this no longer supported?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2017 01:57 PM
Hi Walter,
Thank you for reaching out. I am not able to reproduce that problem. I also tested it using the openVulnQuery client as follows:
bash-3.2$ openVulnQuery --cvrf --severity critical --first_published 2017-01-01:2017-10-01
[
{
"advisory_id": "cisco-sa-20170315-ap1800",
"advisory_title": "Cisco Mobility Express 1800 Access Point Series Authentication Bypass Vulnerability",
"bug_ids": [
"CSCuy68219"
],
"cves": [
"CVE-2017-3831"
],
"cvss_base_score": "9.8",
"cwe": [
"CWE-264"
],
"first_published": "2017-03-15T16:00:00-0500",
"last_updated": "2017-10-06T14:32:50-0500",
"product_names": [
"Cisco Mobility Express "
],
"publication_url": "https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170315-ap1800",
"sir": "Critical",
"summary": "A vulnerability in the web-based GUI of Cisco Mobility Express 1800 Series Access Points could allow an unauthenticated, remote attacker to bypass authentication. The attacker could be granted full administrator privileges.<br />\n<br />\nThe vulnerability is due to improper implementation of authentication for accessing certain web pages using the GUI interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to the web interface of the affected system. A successful exploit could allow the attacker to bypass authentication and perform unauthorized configuration changes or issue control commands to the affected device.<br />\n<br />\nCisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.<br />\n<br />\nThis advisory is available at the following link:<br />\n<a href=\"https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170315-ap1800\">https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170315-ap1800</a>"
},
{
"advisory_id": "cisco-sa-20170419-cimc3",
"advisory_title": "Cisco Integrated Management Controller Remote Code Execution Vulnerability",
"bug_ids": [
"CSCvd14578",
"CSCve48833"
],
"cves": [
"CVE-2017-6616"
],
"cvrf_url": "https://tools.cisco.com/security/center/contentxml/CiscoSecurityAdvisory/cisco-sa-20170419-cimc3/cvrf/cisco-sa-20170419-cimc3_cvrf.xml",
"cvss_base_score": "9.8",
"cwe": [
"CWE-20"
],
"first_published": "2017-04-19T16:00:00-0500",
"last_updated": "2017-10-03T20:37:11-0500",
"product_names": [
"Cisco Unified Computing System (Management Software) "
],
"publication_url": "https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170419-cimc3",
"sir": "Critical",
"summary": "A vulnerability in the web-based GUI of Cisco Integrated Management Controller (IMC) could allow an unauthenticated, remote attacker to perform unauthorized remote command execution on the affected device.<br />\n<br />\nThe vulnerability exists because the affected software does not sufficiently sanitize specific values that are received as part of a user-supplied HTTP request. An attacker could exploit this vulnerability by sending a crafted HTTP request to the affected software. Successful exploitation could allow an unauthenticated attacker to execute system commands with <em>root</em>-level privileges.<br />\n<br />\nThere are no workarounds that address this vulnerability.<br />\n<br />\nThis advisory is available at the following link:<br />\n<a href=\"https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170419-cimc3\">https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170419-cimc3</a>"
},
{
"advisory_id": "cisco-sa-20170907-struts2",
"advisory_title": "Multiple Vulnerabilities in Apache Struts 2 Affecting Cisco Products: September 2017",
"bug_ids": [
"NA"
],
"cves": [
"CVE-2017-9793",
"CVE-2017-9804",
"CVE-2017-9805"
],
"cvss_base_score": "NA",
"cwe": [
"CWE-20",
"CWE-399"
],
"first_published": "2017-09-07T21:00:00-0500",
"last_updated": "2017-10-03T19:43:29-0500",
"product_names": [
"NA"
],
"publication_url": "https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170907-struts2",
"sir": "Critical",
"summary": "On September 5, 2017, the Apache Software Foundation released security bulletins that disclosed three vulnerabilities in the Apache Struts 2 package. Of these vulnerabilities, the Apache Software Foundation classifies one as <em>Critical Severity</em>, one as <em>Medium Severity</em>, and one as <em>Low Severity</em>. For more information about the vulnerabilities, refer to the <a href=\"#details\">Details</a> section of this advisory.<br />\n<br />\nMultiple Cisco products incorporate a version of the Apache Struts 2 package that is affected by these vulnerabilities. <br />\n<br />\nThe following Snort rule can be used to detect possible exploitation of this vulnerability: Snort SIDs 44315 and 44327 through 44330.\n<br />\n<br />\nThis advisory is available at the following link:<br />\n<a href=\"https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170907-struts2\">https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170907-struts2</a>"
},
{
"advisory_id": "cisco-sa-20170909-struts2-rce",
"advisory_title": "Apache Struts 2 Remote Code Execution Vulnerability Affecting Multiple Cisco Products: September 2017",
"bug_ids": [
"NA"
],
"cves": [
"CVE-2017-12611"
],
"cvss_base_score": "NA",
"cwe": [
"CWE-20"
],
<<output omitted for brevity>>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2017 03:08 PM
Thank you for the quick reply. Glad to know it is working as expected. What do you think would be the reason for the 500 error I am getting in response to the date range query?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2017 03:13 PM
Hi Walter,
QQ: Are you using Postman? You should definitely not be seeing a 500 back. I also just tested with Postman. The only difference when you use postman is that you need to specify .json in the URL, as I include in the screenshot below.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2017 10:01 AM
I neglected to take into account I was working from a Unix shell prompt. When I re-examined the date range specification, I realized that the “&” character was being interpreted by the shell, causing the problem. Escaping this character eliminated the issue, and I’m now receiving date-range data.
I sincerely appreciate all your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2017 02:36 PM
Awesome!!! Glad that it's working for you!!
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2017 10:09 AM - edited 06-09-2023 02:44 AM
The Cisco PSIRT openVuln API can be accessed via Cisco’s API Console. Cisco’s to access and consume Cisco data in the cloud in a simple, secure and scalable manner. The console provides a simplified, guided experience, through which partners and customers can easily learn about these services and integrate them within their internal tools, systems and applications; secure data and credentials using industry standard authentication and role-based authorization; and scalability to support diverse data consumption scenarios, like mobile apps, smart devices and Web applications.
The Cisco API Console Documentation explains the steps necessary to obtain oAuth2 credentials and using Cisco's API Console for the registration of a client application that will call the Cisco PSIRT openVuln API.
Check double times your true date range from https://calculator.date/
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: