- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- AMP for endpoint can't block the packered WannaCry.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2018 04:13 AM - edited 02-20-2020 09:05 PM
AMP for endpoint seems to be not able to block the wannacry which is encrypted with packer tool.
Are there any workaround?
Repro-steps:
1. get a wannacry from ThreatGrid or any other service
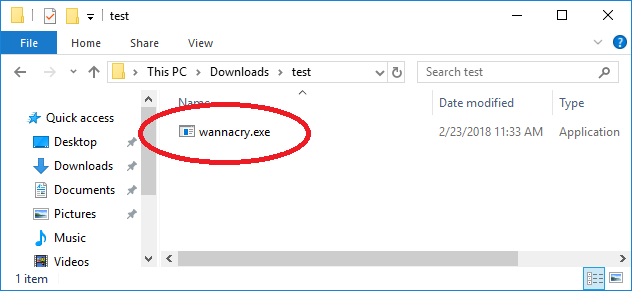
2. encrypt it with packer tool such as upx
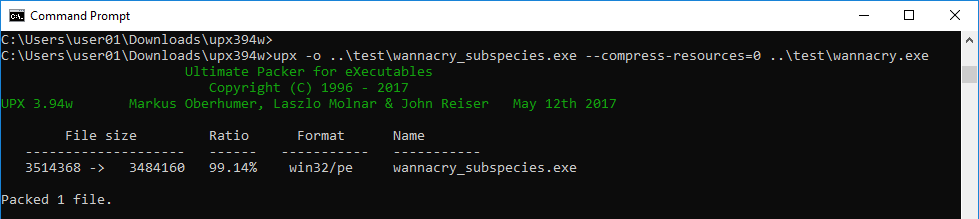
3. open AMP console and enable TETRA feature.
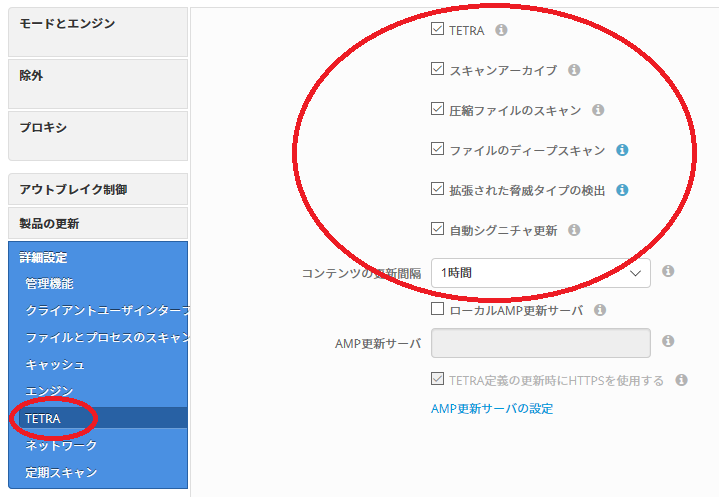
4. Install the Connector.
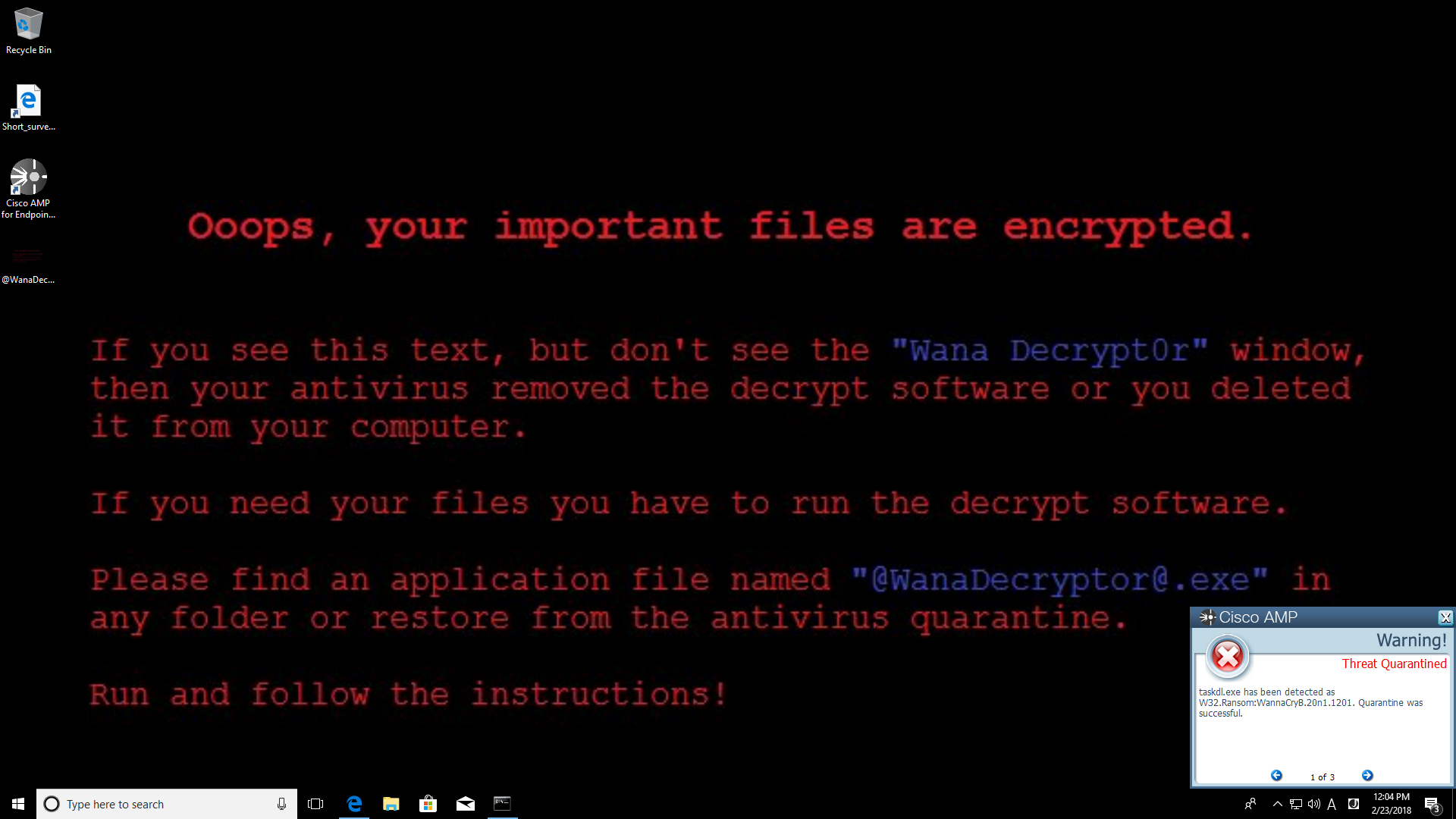
5. Scan the wannacry with AMP for endpoint. It is judged as no problem.
6. Run the wannacry. It works. Some programs such as WannaDecrypter are blocked. But encryption of user data complete.
Solved! Go to Solution.
- Labels:
-
Endpoint Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 06:00 AM
Hi Takahiro,
Thank you for sharing further details of your testing. Did you see a Cloud IOC fire in the AMP Console? I would expect that to happen as the minimum and in a realistic scenario, the infection could be prevented by one of the "new" engines, that are a part of this connector version. For real-time ransomware blocking, there's going to be a beta of one more component available soon, that is highly effective at addressing the problem of ransomware generically (file encryption behavior observed, initiating process blocked; with an ability to exclude benign processes). A notification about the Beta will be posted to the AMP Console and you would receive an email notification if that's enabled on your console.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2018 11:49 AM
Hello Takahiro Tsunoda,
Thank you for your screenshots and the repro-steps.
What version of the AMP for Endpoints connector are you running in this testing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 07:30 PM
Hi Evgeny,
Thank you for your reply.
The version of connector I tested is 6.0.7.10670.
Best regards,
Takahiro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2018 06:00 AM
Hi Takahiro,
Thank you for sharing further details of your testing. Did you see a Cloud IOC fire in the AMP Console? I would expect that to happen as the minimum and in a realistic scenario, the infection could be prevented by one of the "new" engines, that are a part of this connector version. For real-time ransomware blocking, there's going to be a beta of one more component available soon, that is highly effective at addressing the problem of ransomware generically (file encryption behavior observed, initiating process blocked; with an ability to exclude benign processes). A notification about the Beta will be posted to the AMP Console and you would receive an email notification if that's enabled on your console.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
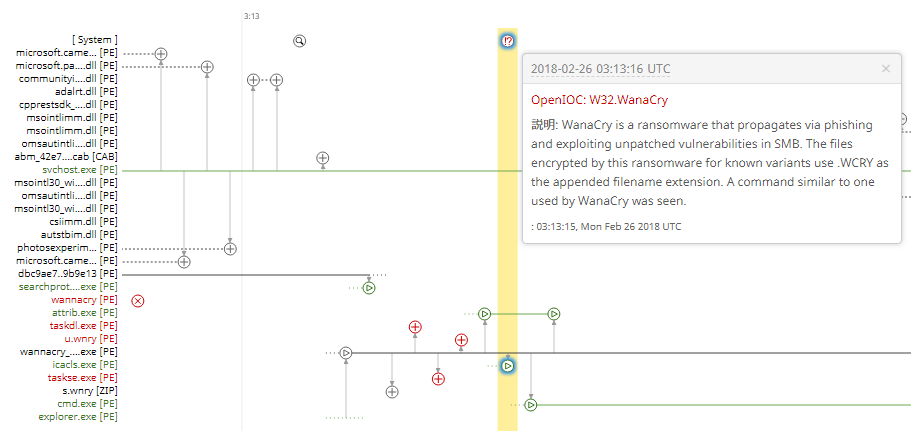
02-26-2018 08:43 AM
Hi Evgeny,
I checked the trajectry. IOC have been fired. But wannacry main file was not quarantined.
I was not able to find the information about beta. How can I use it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2018 11:47 PM
Hi Takahiro,
Apologies for the delay to respond. You can enroll in the Beta program using your AMP for Endpoints console by navigating to Management > Beta > Enroll.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2018 02:54 AM
Thank you for your answer. My question was cleared. ![]()
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide