- Cisco Community
- Technology and Support
- Security
- Security Blogs
- What's New in NGFW FTD 6.7, ASA 9.15.1, FXOS 2.9
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Cisco is happy to announce their Fall release, FTD 6.7/ASA 9.15.1/FXOS 2.9, which consists of 104 features across 24 initiatives, addressing technical debt while staying true to our five core investment areas: Ease of Use and Deployment, Unified Policy and Threat Visibility, World-Class Security and Control, Deploy Everywhere, and Bring Customers to the Next Era.
Let’s take a deeper look into some of the new features, capabilities, and improvements that make 6.7 such a solid release, delivering quality and value for customers and partners.
Release Highlights
- Improved health monitoring across data plane and Snort.
- FTD configuration rollback to last working state in FMC.
- Separation of NetOps (access policy) and SecOps (IPS policy) tasks during configuration deployment.
- Detailed audit log with per-user change tracking.
- Copying rules between pre-filter and main access policies to simplify post-migration configuration optimization.
- SAML 2.0 authentication for FMC and RAVPN.
- TLS Server Identity Discovery without full decryption for AVC and URL functions.
- Linking same-forest domains in identity policies for better user mobility at large enterprises.
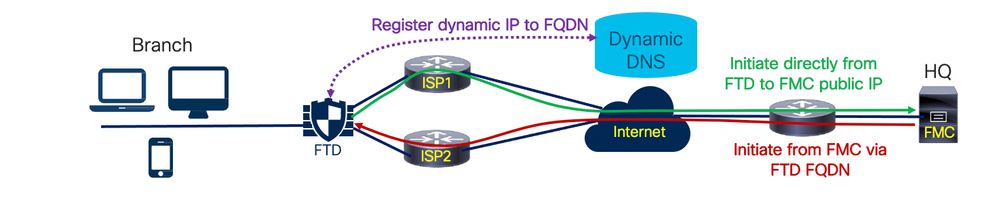
- Over-data-interface management and bi-directional FMC connection establishment with dynamic DNS for simplified branch deployments.
- Static VTI for route-based VPN connectivity.
- GCP and OCI support for both ASAv and FTDv
- Improved distributed PAT operation in clustering for large-scale service providers.
For FMC 6.7 features and demonstration videos, see Firepower 6.7 Release Demonstration and Cisco NetSec YouTube channels.
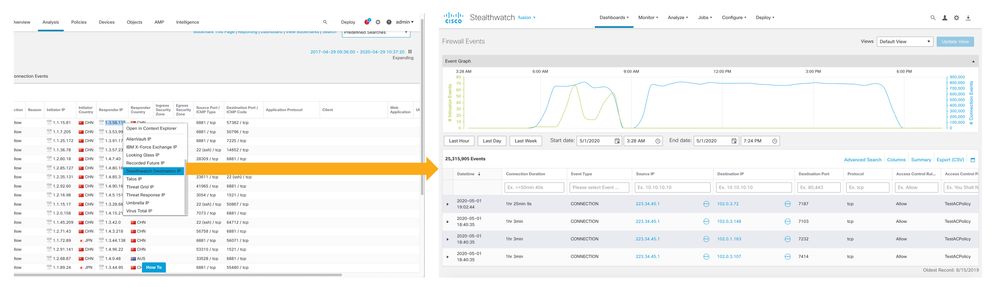
Scalable Eventing & Logging Improvements
Large SMB, midmarket, and commercial customers will delight in the ability to finally integrate the two, right-click, and pivot filter on menus like web, server, and client applications, port, protocol (source and destination), IP address (source and destination), ACP rule, file or username. Network admins can filter further back than ever before on historical data. Another advantage is that customers have a single place to view Snort and LINA side logs; the days of scouring myriad places to find these logs are over!
The catalyst for numerous TAC cases and the number one contributor to scaling problems with FMC, the introduction of this capability increases the FMC's performance. The customer also realizes improved log retention times with the additional storage capacity.
This capability addresses the RFP pain point; now, customers can retain logs for a much longer duration.
SWE as a syslog target with contextual cross-launch support
Threat Efficacy Investment + Latest Web Standard Support
Pure play security personas, IPS, and threat-focused customers are sure to love this release. A modernization of the venerable Snort security tool, Snort 3 leverages a multithread architecture for improved performance and simplified detection. Customers will see improved resource utilization on their systems, enabling greater inspection. The Snort language is getting an update with simplified rule writing and flexible expansion capabilities. Alongside, acceleration of additional protocol support. Further, a rearchitected IPS engine includes multithreaded design, new rules-language, modularity, fixes for efficacy issues without negative impact on performance, with phase one including support for CDO and FDM-managed FTD devices.
Those who live and breathe security discovers a chance to expand their detection capabilities, simplify their rule writing, and learn to do a lot more with greater ease. For the network security manager, Snort 3 makes its security appliance more resource-efficient, allowing more expanded coverage than before. With a more efficient resource usage model, customers can enable additional rules before hitting system capacity trade-off points.
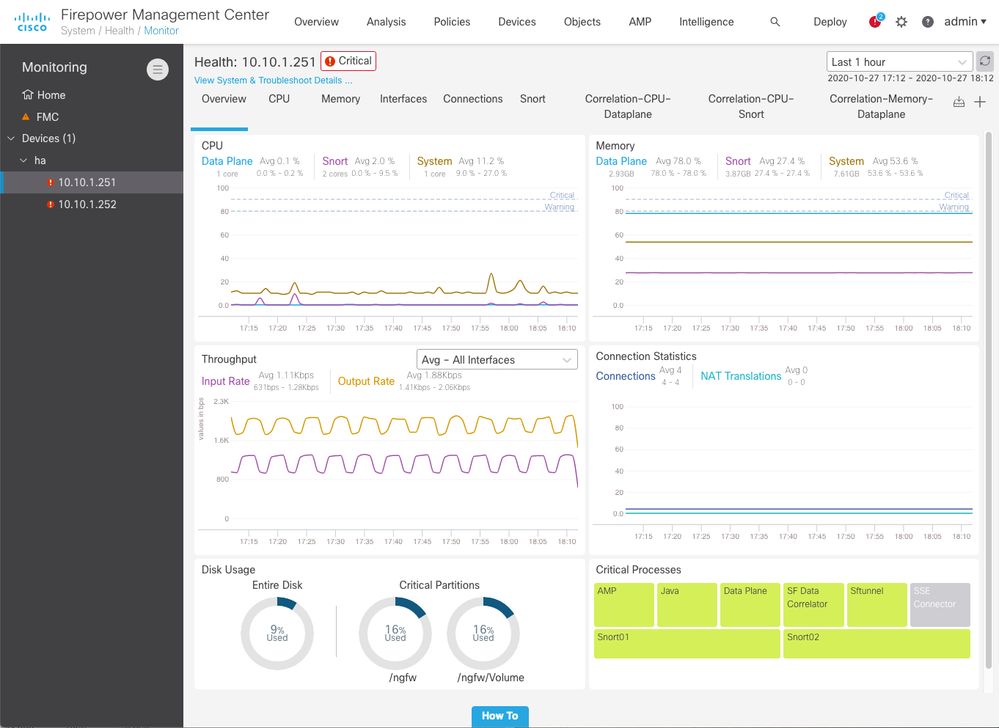
Device Health Monitoring
Customers can now troubleshoot, diagnose, and self-solve network problems by pinpointing the cause of bad health or ruling out the NGFW as the cause. This ability to narrow in on problem specifics should reduce the number of related TAC cases and help solve them faster. As part of Unified Health monitoring support on the device, we’re introducing a new architecture using Prometheus on FMC and a new health monitoring dashboard to report a single set of metrics across the entire FTD device. New snort metrics will be added to SNMP and UI as well. SNMP access for LINA and Snort has been unified for Non-SSP platforms, and unification with FXOS is planned for a future release.
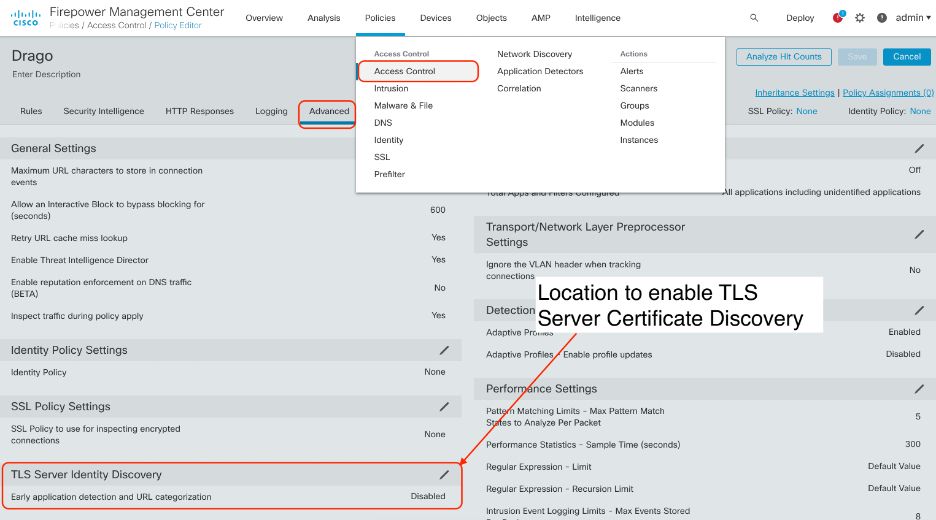
Application & URL Visibility in TLS 1.3
Any customer performing Application ID and URL Filtering will be interested in this unique feature. TLS 1.3 encrypts TLS certificates. This is new behaviour for Transport Layer Security introduced with TLS 1.3. Certificates are no longer usable by a firewall in policy rule matching. An attacker can circumvent the Access Control and SSL policy enforcement based on Application (AppID) or URL categories with TLS 1.3 connection coupled with spoofed SNI.
TLS Server Identity Discovery allows the firewall to “learn” the TLS certificates from servers that support TLS 1.3 and earlier TLS versions, helping the firewall:
- Overcome the inherent challenge of encrypted server certificates in TLS 1.3.
- Effectively enforce the policy.
- Overcome ambiguity about whether the TLS decryption should occur.
When TLS Server Identity Discovery is enabled, customers can perform policy rule matching without performing full decryption of the TLS 1.3 traffic and avoid the large decryption performance penalty.
Important technical details about TLS Server Identity Discovery:
- First available in the 6.7 release, though disabled by default.
- Available for Snort 2 (restarts Snort) and Snort 3 (no restart) only on FTD platforms.
- Supported in routed, transparent, and inline set mode.
- Supported for standalone, high availability (HA), and cluster deployments.
- Configured by the FMC, FDM, FTD Device REST API. Cisco Defense Orchestrator (CDO) is not supported with 6.7.
- Not supported for FTD Inline Tap or Passive Mode deployments.
- Does not require a special license.
RA VPN Functionality Gaps for FTD
Commercial and enterprise customers, particularly those looking for a one-box solution for RAVPN and NGFW, will appreciate the continued expansion of RA VPN features on FTD:
- Basic API support for DAP/hostscan.
- LDAP-based authorization maps.
- Deployment of AnyConnect optional modules and associated profile configurations (not editable).
- SAML 2.0 authentication (SAML authorization – attribute handling with DAP coming in 7.0).
With 6.7, we take a significant step toward RAVPN parity with ASA, removing a barrier to FTD migration and enabling more customers to migrate from ASA to FTD. Eliminating the need for a two-box solution reduces TCO and complexity. It opens opportunities for NGFW sales and renewals to customers looking for an integrated solution, including VPN only customers.
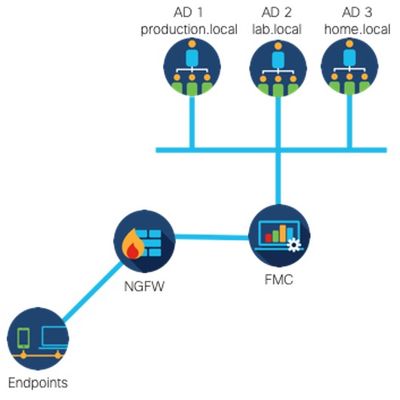
Identity Firewall – Multi-Domain Support
Enterprise customers with large environments often have users from different domains from the same/overlapping network segment. 6.7 provides the ability to passively identify users and groups from the multiple Active Directory / LDAP domains coming from a single network. How does it work? Each Active Directory / LDAP Domain is represented by a Realm. To achieve the lookup of identities from multiple domains, the FMC/FDM UI has a new element, Realm Sequence, which allows multiple Realms to be added into one object and referenced in the identity rule. This provides system lookups of user identities from one or more networks against multiple Active Directory / AD domains.
Identity: Cisco Firepower Remediation with ISE using ANC over PxGrid 2.0
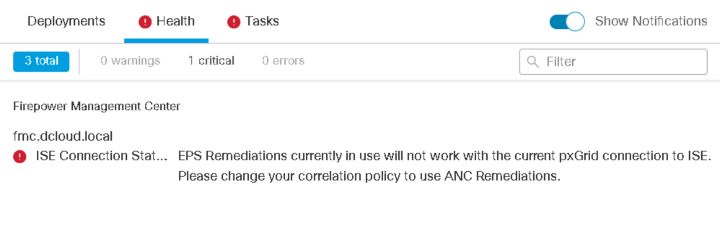
This new feature surges scaling capability deployments and allows administrators to directly connect the ISE system with multiple FMC systems and/or FTDs managed locally by FDM. FMC uses PxGrid 1.0 protocol for integration with ISE. FMC obtains information from User-IP mappings, User-SGT/IP-SGT mappings, SXP mappings, and endpoint profiles using this communication channel. Starting with 6.7, we’ve updated the communication protocol for this integration from PxGrid 1.0 to PxGrid 2.0. The new version offers additional scale benefits for ISE.
Most importantly, from a Firepower perspective, it enhances high-availability connectivity to ISE. With PxGrid 2.0, our FMC solution supports true active/active HA connectivity. PxGrid 1.0 uses EPS (Endpoint Protection Services) and is being replaced by ANC (Adaptive Network Control) remediation module used for Firepower integration with ISE.
PxGrid 2.0 support provides:
- Improved and a secured communication channel between ISE and Firepower Systems (FMC and FTD/FDM) which is used for integrating these two components.
- Increased positive effect on user experience! The PxGrid 1.0, which uses the certificate-based connection between ISE and Firepower, was replaced with PxGrid 2.0, and uses WebSockets (REST) based connection.
- Expanded scaling capability for the number of clients supported behind the PxGrid connection, increasing from 10-25 clients to up to 400 clients (FTD/FMC or other clients to ISE).
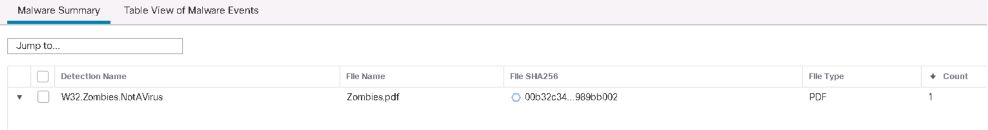
Successful quarantine of source host using ANC remediation module, after the client downloading the malware file that violates the administrator’s policy.
Network administrators who had already configured EPS remediation in pre-6.7 releases and upgraded to the 6.7 release will be notified about EPS replacement with ANC remediation and system suggestions to make necessary configuration changes.
Site-To-Site VPN
With organizations moving workloads to the Cloud, FTD customers need a Site-to-Site VPN as a secure tunnel to ensure all traffic between source and destination is encrypted to reduce threats and unauthorized traffic. With 6.7, FTD will enable branches to effectively connect with VPN gateways in the Cloud with features including:
- Support for route-based VPN.
- Configuration support for static virtual tunnel interface (VTI).
- Ability to efficiently migrate from crypto-map based VPN configuration to VTI based VPN.
FMC Change Management - Workflow & Audit
FMC 6.7 continues the phased delivery of change management capabilities with additional configs to Preview Delta and Manual Rollback to previous known good configs. Customers can consult the audit log to determine what’s new, what’s changed, and who changed it. Improvements to audit log support extend to the following policies/objects and help limit mistakes leading to outages or unexpected network behaviour with the option to rollback in case of a deploy issue:
- Network
- Port
- URL
- VLAN object/Group
- Routing
- DHCP
- NGFW Platform Settings
- VPN
- NAT
- QoS and Prefilter
Simple Remote Branch Deployment
Distributed enterprises with branch deployments will appreciate the value of simplification. Remote branch deployments are troublesome, especially if FMC loses connectivity to the FTD. It’s not uncommon for the IT person at the branch to lack the skills necessary to troubleshoot, and the deployment cost is huge in such cases. For this multi-phased initiative, we are enabling management via data interfaces for FMC-managed devices. Should there be a connectivity failure between FMC and FTD, a manual rollback option is available via CLI. In the future, we’ll add multiple WAN interfaces and HA support.
Cloud Management Enablement - Edge & Branch <1000 users
Custom IPS policies (based on Snort 3) are now enabled in CDO. Commercial customers with edge and branch deployments will find a new, more approachable experience when creating custom policies based on TALOS rules, grouped with themes. This functionality delivers on the long tails of FTD features to be surfaced in CDO (EIGRP, more flexible upgrades capabilities, and URL filtering), along with better APIs for CDO developers and customers to work on, like backward compatibility and better documentation.
Port Address Translation Improvements
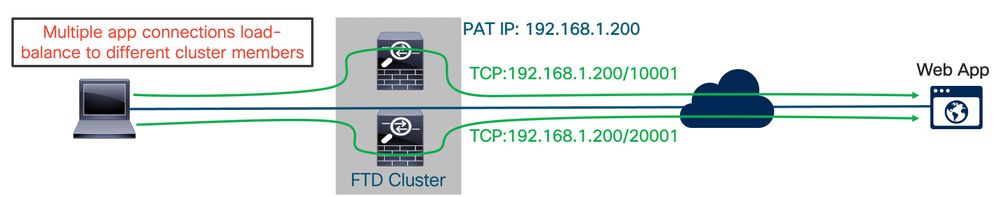
Enterprise, Internet Edge, and customers using PAT on clustered devices will appreciate this improvement. Originally, the PAT pool was uniformly distributed to all cluster members at the IP level. Customers were forced to provision as many PAT IP addresses as members in the cluster, increasing the chances of allocating the same PAT IP address for different connections from a single inside local host. With 6.7, each PAT pool IP will be distributed at the port block level saving public IP addresses and eliminating failure of multisession applications (e.g. social networks or webmail) if individual connections are load-balanced to different cluster members. The ASA/FTD cluster becomes more flexible to the architect as the limitation of the IP address requirement is lifted. The cluster members can be added to expand throughput capacity without needing to provision IP resources first.
FMCv Expansion
Without FMCv high availability, customers using virtual were fearful of the inability to make changes if they lost their virtual FMC. With the introduction of FMCv300 managing a large number of devices, this capability has become extremely critical as customers transition from hardware to virtual. The high availability feature allows the designation of a redundant virtual FMC to manage devices to ensure operational continuity.
Policy & Event Usability Improvements
In this release, we continue improving the usability to help customers optimize their large configurations, reduce time to troubleshoot, and save on operational costs. We now support Bulk Upload of the network, port, VLAN, and URL objects via text file, Search/Filter on comments in AC Policy, Search/Filter on FTD NAT Rules, and the ability to Copy or Move rules between Pre-filter and Access Policy for an improved policy configuration experience.
Device Upgrade Improvements
Improving the stability, reliability, and user-experience of our upgrades continues across releases. It’s possible to automatically or manually cancel upgrades (in case of failure for major upgrades), validate FXOS information in FMC/FDM for 9300/4100 FPR platforms, and improved reliability and error messaging for upgrade failures.
Config Deploy Time Reduction & Optimization
Deployment performance and optimization have been improving over the last several releases. In the 6.7 release, the cluster deploy time has been improved by ~20%. We’ve optimized the device configuration package for ‘LINA Only’ configurations so that non-LINA configurations aren’t included if nothing has changed. The addition of Native Security Zone support for AC Policy brings customers stability with a small rule basis.
FTD 6.6.1 is now the Suggested Release for NGFWs
You can upgrade directly from any version in 6.2.3+ (no more having to upgrade to 6.6.0 and then upgrade to 6.6.1). This is expected to make quite an impact as customers on older releases can make the jump to this 3-digit release in a single hop. It includes all the new features, usability, performance improvements of FTD 6.6. The 3-digit MRs show tremendous customer adoption, quality, and reliability.
Read the 6.7 Release Notes for more information, including a complete list of features available.
See the NGFW Community Page for documentation.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: