- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- Re: Should you always be able to login using fallback domain?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2021 10:15 AM
Hey folks!
I think I got this wrong, when I read through the Documentation I thought that you can always login using the fallback domain.
I have a local admin user configed for the ACI Fabric and had the impression that I can always login with User apic:fallback\\admin on APIC GUI and with apic#fallback\\admin on APIC and Switch CLI ..
But I seem to be wrong, since I don't manage to use this as login after I configured TACACS+ login as default Realm.
Is this assumption right, or did I mess up my config?
TACACS+ Login works fine.
BR
Jules
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2021 03:07 AM
By default, the fallback login domain is the local realm. If you haven't change it, then first step is passed.
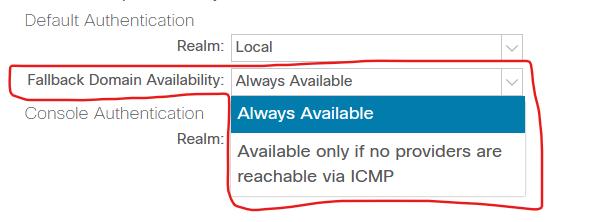
Second thing which is important, is the setting of "Fallback domain availability" which modify the activation of the fallback domain:
-
Active if ICMP health check fails—The fallback domain becomes active only when all AAA providers in the Default Authentication Realm fail the ICMP health check.
-
Always Active—The fallback domain is always active.
The default setting is Active if ICMP health check fails.
I would suggest you enable the "always available". It is a safe mechanism in case of problems with AAA providers.
To access the fallback domain, indeed you have to manually invoked to be utilized. It can be done so with the following syntax:
-
From the GUI, use apic:fallback\\username.
-
From the REST API, use apic#fallback\\username
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 09:43 PM
Hi @julian.bendix,
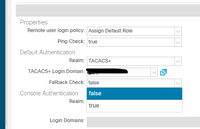
when you configure the authentication on the APIC there is a selection for "fallback check".
If you select false: the APIC will not check if your TACACS server(s) is reachable but always allow to login in with the fallback domain.
If you select true: the APIC will check if your TACACS server(s) is reachable and only if it's not reachable allow to use the fallback domain.
Christoph
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-13-2021 03:07 AM
By default, the fallback login domain is the local realm. If you haven't change it, then first step is passed.
Second thing which is important, is the setting of "Fallback domain availability" which modify the activation of the fallback domain:
-
Active if ICMP health check fails—The fallback domain becomes active only when all AAA providers in the Default Authentication Realm fail the ICMP health check.
-
Always Active—The fallback domain is always active.
The default setting is Active if ICMP health check fails.
I would suggest you enable the "always available". It is a safe mechanism in case of problems with AAA providers.
To access the fallback domain, indeed you have to manually invoked to be utilized. It can be done so with the following syntax:
-
From the GUI, use apic:fallback\\username.
-
From the REST API, use apic#fallback\\username
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 02:12 PM - edited 11-14-2021 02:13 PM
Hi Sergiu,
thanks a lot for all the info. Makes sense to me.
I just seem to run a older version of ACI I guess, I only have the menu "fallback check" which gives me the options "true" or "false".
If i open the help page, I just get explanations for the options you posted as well, not the options that I have ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2021 09:43 PM
Hi @julian.bendix,
when you configure the authentication on the APIC there is a selection for "fallback check".
If you select false: the APIC will not check if your TACACS server(s) is reachable but always allow to login in with the fallback domain.
If you select true: the APIC will check if your TACACS server(s) is reachable and only if it's not reachable allow to use the fallback domain.
Christoph
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide