Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center and Cloud Blogs
- Gaining valuable insights from Intersight Audit Logs
678
Views
0
Helpful
0
Comments
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-25-2023
07:30 PM

I had been using Intersight for months before I realized Intersight maintained persistent records of every action taken within Intersight. These records are kept in the Audit Logs. These records include the create, update, and delete operations for every policy, pool, profile, role... essentially every managed object. In this blog, I'll describe some interesting use cases for querying this information and show you how to perform your own queries.
Use case description
These are just a few scenarios with which you might be able to relate.
-
I left my computer unattended (shame on me) and someone may have accessed Intersight from my computer while I was gone. What (if anything) was done in Intersight using my credentials?
-
In our lab, we have a lot of policies with non-descriptive names. Who created that policy so I can ask them about its intended purpose?
-
Someone accidentally changed a production policy. What were the original settings for that policy so I can fix it?
-
What has been deleted from Intersight in the last X days? Perhaps I want to generate a weekly report of all the managed objects that have been deleted in the last week. In a production environment, you would hope to see a very short list!
-
Who is accessing Intersight? Sometimes you need a list of everyone who has accessed Intersight in the last week or who is accessing Intersight most often.
Keep reading to see how I solve each of these use cases. I'll use various filters to retrieve the desired data from the Audit Logs.
Accessing the Audit Logs
If you would like to follow along with this blog, you can do so in your own Intersight account or use Cisco dCloud's instant demo called "Cisco Intersight - A New Look" located here.
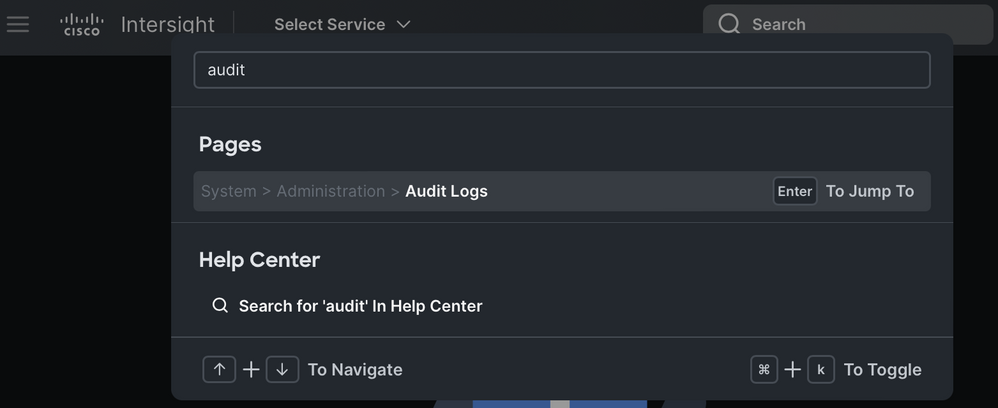
The Audit Logs table is easy to find with Intersight's command palette. Simply press Ctrl+K (Windows/Linux) or Command+K (Mac) to pull up the search and type the word "audit" as shown below. Note that you can only view the audit log if you have the Account Administrator or Audit Log Viewer role.
The audit log is comprehensive. By default, it stores 48 months of history (events older than 48 months are removed automatically), but the Account Administrator can change that to a shorter time window.
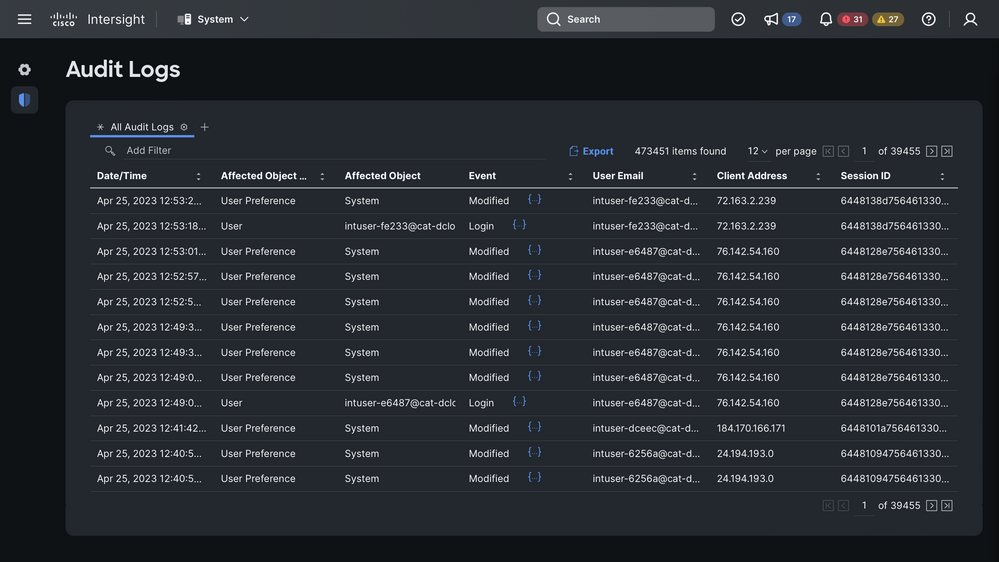
As you can see in the screenshot above, the log can easily get to tens of thousands of pages full of records in 48 months!
Use case 1
I accidentally left my computer unattended with my browser logged into Intersight. Did anyone make changes in Intersight while I was away? Despite the Audit Logs containing tens of thousands of pages of records, it is still easy for me to figure this out with a simple filter. Directly above the table is a magnifying glass with the words "Add Filter". Clicking on the words "Add Filter" provides me with a dropdown list of attributes I can use to filter the table. User Email is one of those filters, and my account email is intuser-52a7d@cat-dcloud.com.
I don't really need it in this case, but I added a second filter to illustrate that multiple filters can be used as seen below.
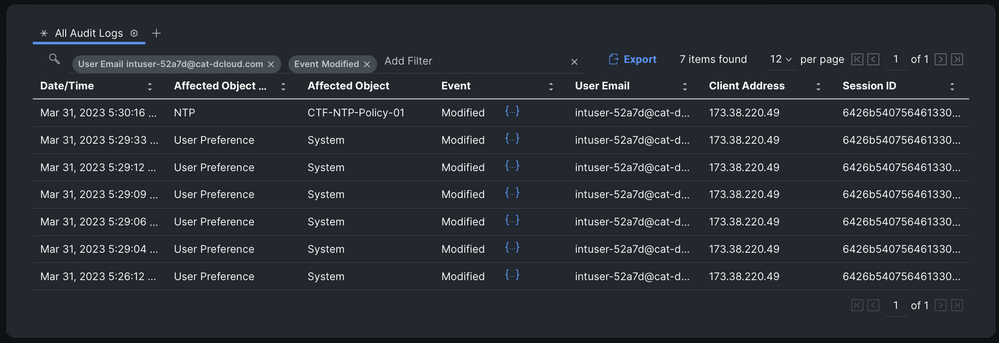
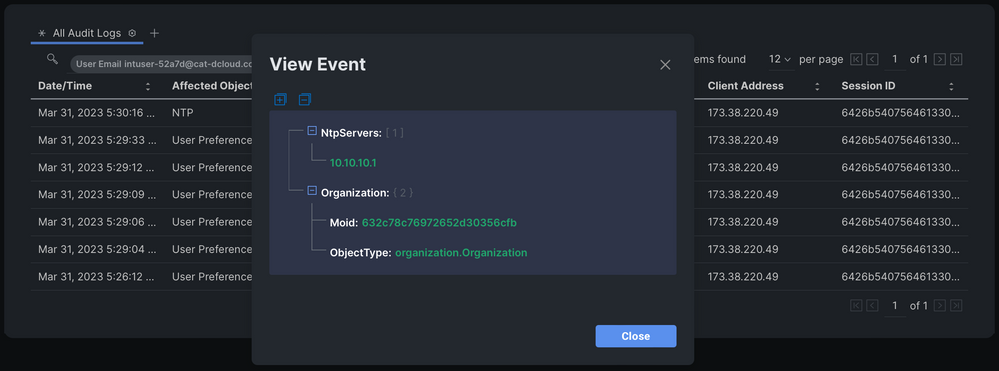
The table is already sorted by most recent events, and the first entry indicates that my user account modified an NTP policy. I know I didn't make the change, so that is proof that someone used my computer to make changes in Intersight while I was away. Clicking on the blue curly braces in that row shows me exactly what was changed: the NtpServers setting was changed to 10.10.10.1.
Use case 2
Now that the audit log has shown that someone used my computer to alter the NTP policy called CTF-NTP-Policy-01, I need to find who originally created the policy so we can fix it. When I browse to the policy in Intersight, this is the URL:
That means that the Moid (managed object ID) of the policy is 6425b04062757230016def13. I'll use the API browser to perform a simple query for that Moid. If you haven't read my blog about the API browser, take a look here. In short, the API browser is a graphical tool for running API calls to Intersight without having to write any code. It's a great tool for exploring and learning the API, but you can also use it for real scenarios where you don't want to write any code.
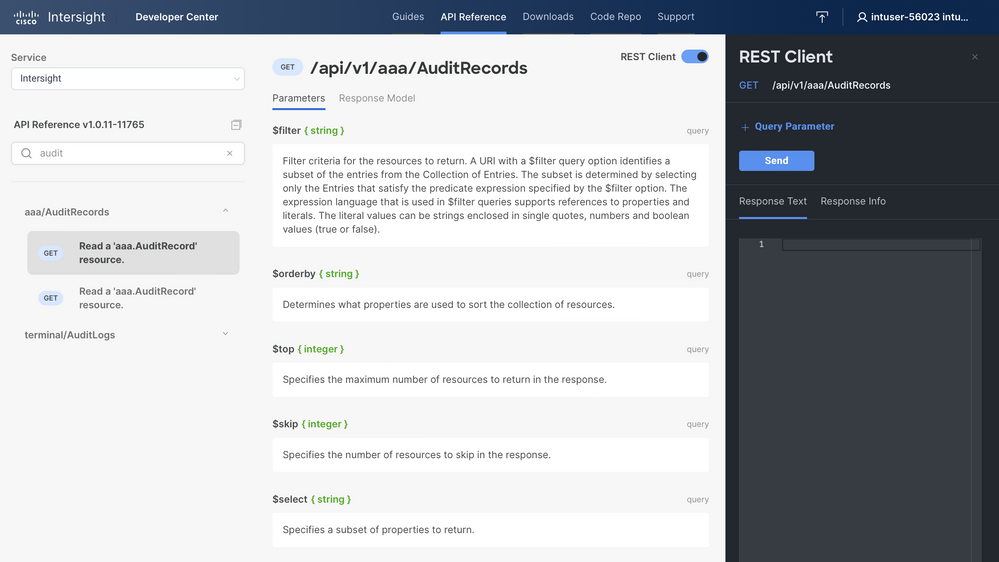
I'll perform the following steps to access the API browser:
-
Browse to intersight.com/apidocs/apiref
-
Use the search box to look for for "audit"
-
Click on aaa/AuditRecords
-
Click on the first GET method
If the above steps are confusing in any way, read my blog about the API browser where I go into more detail about accessing and using the browser. Those steps will take me to the following screen, where I am ready to execute an API call to the AuditRecords endpoint to query the many thousands of records.
Before I hit Send, I need to apply a filter. I don't want to scroll through thousands of records. In my previous blog, I mentioned that the middle part of the screen contains documentation for the various query parameters I can apply. I need a filter, and there is query parameter called $filter. The documentation says it "identifies a subset of the entries"... well, that's perfect.
To add a query parameter, I just click the blue + Query Parameter above the Send button. The Key is $filter and the Value is:
ObjectMoid eq '6425b04062757230016def13'Remember that I pulled the obtained the Moid for the NTP policy at the beginning of this section. This $filter will tell Intersight only to return audit records where the Moid of the affected object is 6425b04062757230016def13. Interestingly, the audit record itself has a Moid, but I need to search for the Moid of the affected object.
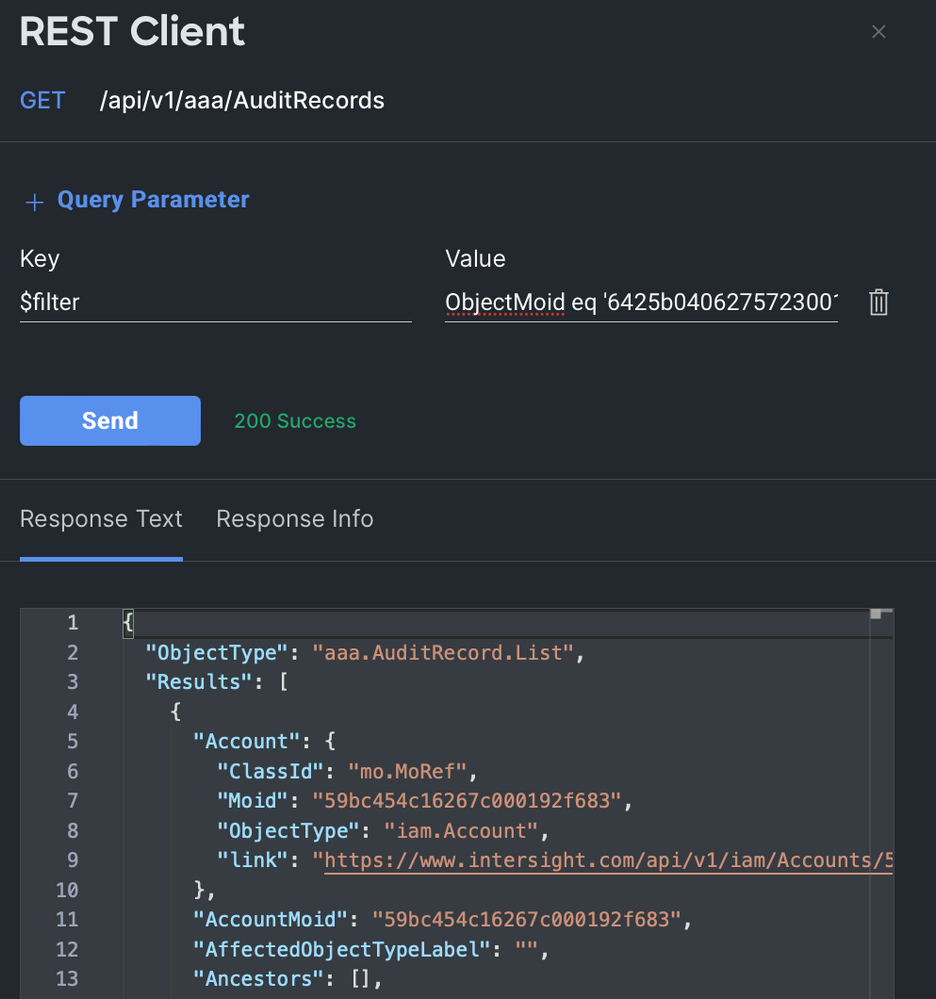
If you're following along, you might notice that the response actually contains two entries: one where the NTP policy was created and one where it was modified. That makes sense, but what if the policy had been modified many times? It could be annoying to scroll through a long list of records where the policy was modified when I only care about when it was created. I can update $filter to filter out some noise:
$filter = ObjectMoid eq '6425b04062757230016def13' and Event eq CreatedScrolling through the response, I see a line showing
"Email": "intuser-54ffd@cat-dcloud.com"Now I've found what I was looking for (the email of the person who created the policy). I can work with that individual to restore the policy that had been modified.
Use Case 3
In this use case, I'm looking for the original settings for a policy that has been modified. In the previous use case, I identified who created the policy. It turns out that that same audit record that shows me who created the policy also contains the original settings used to create the NTP policy! Without modifying any of the query parameters I used in the previous API call, I can see the following data in the response in the API browser:
"Request": {
"Description": "Demo CTF Policy",
"Enabled": true,
"Name": "CTF-NTP-Policy-01",
"NtpServers": [
"198.19.255.137"
],
"Organization": {
"Moid": "632c78c76972652d30356cfb",
"ObjectType": "organization.Organization"
},
"Tags": [],
"Timezone": "Etc/GMT"
}The original value for NtpServers is 198.19.255.137, so now I can fix the policy myself!
Use case 4
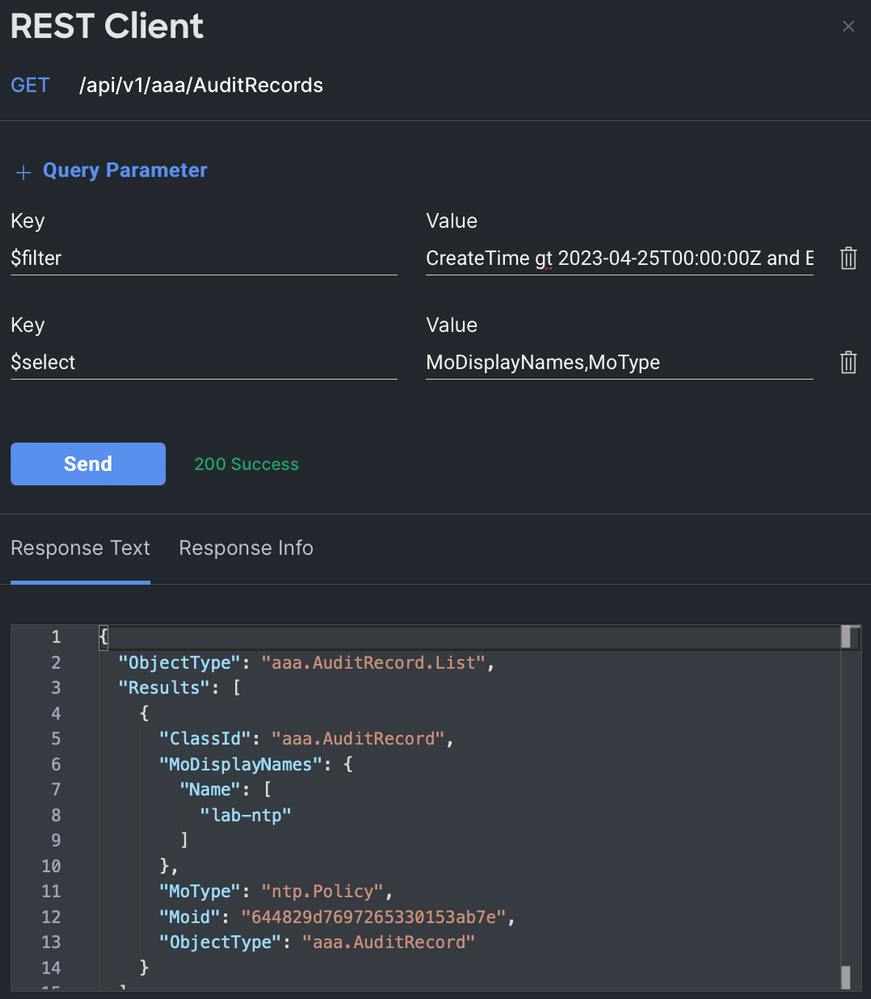
What has been deleted from Intersight in the last X number of days? I will again use $filter. I need to apply two filters: one for the date and one for Event=Deleted. That makes my filter:
CreateTime gt 2023-04-25T00:00:00Z and Event eq DeletedIn the above $filter, gt is interpreted by Intersight as "greater than." In other words, I've told Intersight to return records that are newer than the specified date and time. Less than and greater than operators can be used to compare dates and numbers.
It's really that easy, but I'll make things a little fancier. Looking through the response, I see a lot of parameters that I don't care about. I can use the $select query parameter to clean up the response.
$select = MoDisplayNames,MoTypeIn the image below, I can see that an NTP policy named "lab-ntp" was deleted without having to scroll through lots of other properties related to this audit record.
Use case 5
Who has been logging into Intersight? I'll use the same API browser to perform the same GET operation against the same method. There is a pattern to all these use cases. I just need apply a different filter. Just like the last use case, I need two filters: one for date and one for Event=Login.
$filter = CreateTime gt 2023-03-25T00:00:00Z and Event eq LoginThis returns the information I need (who has been logging in), but the payload is a little messy for me. If a user had logged in eight times, there would be eight records displayed in that payload. What I really want is a list showing each user who has logged in and how many times they have logged in.
The Intersight API has the ability to perform advanced aggregation functions, so counting the number of times each user appears is easy. The Intersight documentation (https://us-east-1.intersight.com/apidocs/introduction/query/#apply-query-option) contains some more interesting and complex aggregation examples than I'll be doing here. Those familiar with database queries will find this syntax familiar.
$apply = groupby((Email), aggregate($count as Logins))If it doesn't look familiar, this query parameter tells Intersight to group the records by Email (all records with the same email will be grouped together) and then to aggregate the results by counting how many records are in each group. The response will look something like this:
{
"Email": "intuser-6f07c@cat-dcloud.com",
"Logins": 6
},
{
"Email": "intuser-9069e@cat-dcloud.com",
"Logins": 8
},
{
"Email": "intuser-1bb2b@cat-dcloud.com",
"Logins": 2
}If I wanted to take things one step further, I could sort the results in descending order (using the keyword "desc") by number of logins (to see who is the most active user of Intersight) by applying one more query parameter.
$orderby = Logins desc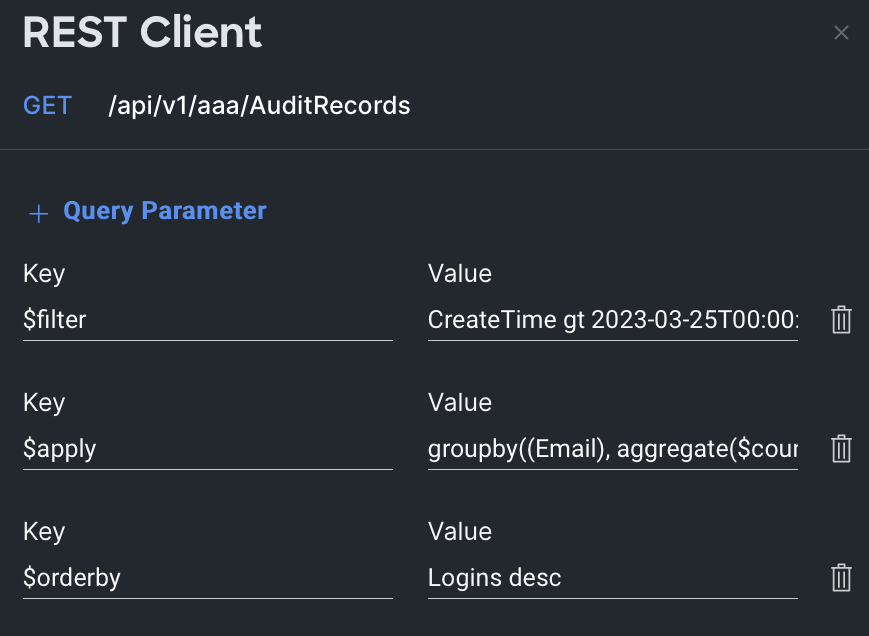
Conclusion
The Intersight Audit Logs contain very valuable information that can be mined with some very simple filters. Audit Logs are free to use with every Intersight license tier. I provided just a few examples of situations where Audit Logs would be invaluable. How will you use this feature?
Labels:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Getting Started
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
Customers Also Viewed These Support Documents