- Cisco Community
- Technology and Support
- Security
- Network Access Control
- 15024 PAP is not allowed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 07:08 AM
Hi,
I'm getting this error whenever I log into the client Windows 11 machine. Any ideas what might be causing this?
Steps
| 11001 | Received RADIUS Access-Request | |
| 11017 | RADIUS created a new session | |
| 11027 | Detected Host Lookup UseCase (Service-Type = Call Check (10)) | |
| 15049 | Evaluating Policy Group | |
| 15008 | Evaluating Service Selection Policy | |
| 15048 | Queried PIP - DEVICE.Device Type | |
| 11034 | Process Host Lookup is disabled. (Service-Type = Call Check (10) cannot be applied) | |
| 15024 | PAP is not allowed | |
| 11003 | Returned RADIUS Access-Reject |
I don't have PAP enabled in the authentication allowed screen as I want to use EAP-TLS. If I enable PAP/ASCII and try again I get a different error:
| Event | 5400 Authentication failed |
| Failure Reason | 22056 Subject not found in the applicable identity store(s) |
It looks like it's trying to find the MAC address in AD and not the username...
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2024 02:54 AM
@alliasneo1 that explains why is fails over to MAB then.
A normal user (none administrator) has access to their own certificate store, you should have a user certificate here:-
If you do not have a user certificate probably the GPO to auto enroll for user certificate is not configured correctly or applied to this user/machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 07:35 AM
Call back is for MAB and your SW use PAP for username and password
if you can not change the behave of SW change the host lookup in ISE policy
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 07:48 AM
Hi, Could you explain a little more about this please?
So the switch uses PAP for username and password? -But it's the PC that is authenticating?
How do I change the behavior of the switch? or where would I change the host lookup option?
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 07:54 AM
sure friend
I am here to help other
check this
Solved: ISE MAB Host Lookup - PAP or EAP-MD5 - Cisco Community
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 08:00 AM
Thanks. The thing is though, I don't want the authentication to fall back to MAB. I want the user to use the certificate from the machine to authenticate against ISE.
I have a Machine certificate (which is working correctly) and I have a user certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 08:16 AM
share the config of SW port
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 08:37 AM
The switchport config is:
int g1/0/23
switchport access vlan xx
switchport mode access
authentication host-mode multi-auth
authentication port-control auto
authentication event fail action next-method
authentication order dot1x mab
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 08:15 AM
@alliasneo1 so you've not got MAB enabled as an allowed protocol (as per the output above). Assuming the switch is setup to allow 802.1X and fall over to MAB then I assume the client is not configured to use 802.1X for user authentication? What is the configuration of the client windows supplicant? Do the users have a user certificate in the user cert store?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 08:42 AM
The certificate is installed on the PC via Group Policy.
If I got to adapter settings on the PC I can see that dot1x is enabled and this is being pushed via GP. 802.1x enabled, use smartcard of certificate.
These are ticked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 09:00 AM
@alliasneo1 so there is a certificate in the user certificate store?
If there wasn't that would explain why it's failed over to attempt MAB.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2024 02:49 AM
Hi,
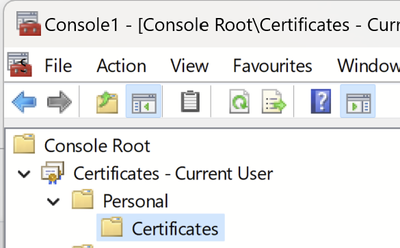
I've checked the certmgr console and added the certificates - current user snap in. When I click on Personal, it says 'there are no items to show in this view' and at the bottom it says 'Personal Store contains no certificates'.
Is this a Group Policy thing that isn't showing me the certs or does that mean it is actually empty and the cert hasn't been pushed to the machine? Is there any other way of looking at user certs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2024 02:54 AM
@alliasneo1 that explains why is fails over to MAB then.
A normal user (none administrator) has access to their own certificate store, you should have a user certificate here:-
If you do not have a user certificate probably the GPO to auto enroll for user certificate is not configured correctly or applied to this user/machine.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide