- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Control Device admin users login location using IP address
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 06:00 AM - edited 02-21-2020 11:11 AM
Hi,
Can ISE (device administration) controls device admin users location (IP address) so that user can login NAD (router/switch) from specific IP address?
As per my understanding, ISE can't restrict device admin users based on IP Address as ISE communicates with NAD (as TACACS+ client) and not endpoint. Second point, AAA client (NAD) sends only user name to TACACS+ server.
Kindly confirm my understanding.
Solved! Go to Solution.
- Labels:
-
Device Admin
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 12:12 AM
Hi @dngore
yes this is very straightforward
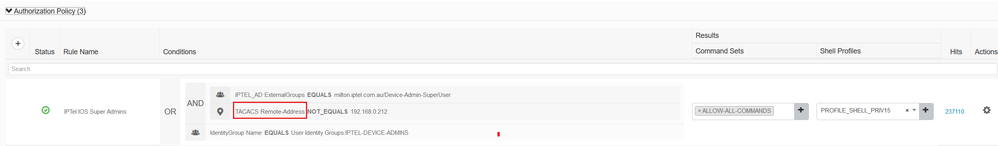
I have modified my lab as follows. I included a check to ensure that the user may not come from IP address 192.168.0.212 or else he will be dropped into read-only mode. If the user comes from any other address, then he will be in privilege level 15 (super admin). The key thing is that the attribute TACACS: Remote-Address is what you're after.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 07:10 AM
In TACACS Live Logs, you can open the details of an authentication/authorization event and see if you have any attribute that you can use to determine the location. In my system, I just checked and see an attribute called "Remote Address" that appears to be the originating client's IP address. But that is a Cisco IOS device using TACACS. Results may be different with different device types, IOS levels, etc.
For a more reliable/secure way of controlling admin access to network devices, use infrastructure ACL's or management plane ACL's on the device to control what subnets can SSH, SNMP, etc. to the device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 08:01 AM
Thx for reply.
But this is not deployed solution. We are proposing it. Customer has below query. Hence want to confirm on same.
So if remote client IP address is seen in log then does that mean we can control device admin user based on IP address in ISE?
We are aware of access list restriction on NAD devices but customer is specifically asking for this feature support in ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2019 11:53 AM
You would need to figure out which Radius/TACACS+ AVP holds that information and test it out. But again, different hardware, IOS, protocol, etc could provide different results. I wouldn't trust it for all devices unless you test each use case in the lab first. Key is to test extensively first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 12:12 AM
Hi @dngore
yes this is very straightforward
I have modified my lab as follows. I included a check to ensure that the user may not come from IP address 192.168.0.212 or else he will be dropped into read-only mode. If the user comes from any other address, then he will be in privilege level 15 (super admin). The key thing is that the attribute TACACS: Remote-Address is what you're after.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide