- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE Admin Certificate - Browsers still happy with certs > 398 days
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 05:57 PM
Hello,
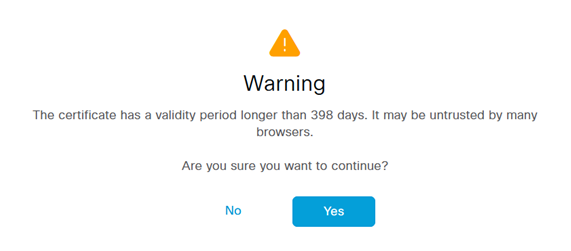
ISE 3.1 displays a great warning when trying to import an Admin certificate with a lifetime of greater than 398 days. It's well known that Apple started this trend, and I have not tested whether Safari enforces this yet. But I can confirm that I was able to install a 5 year certificate, and neither Firefox, Chrome nor Edge had any complaints about it. I have to add, that the cert was created by internal PKI, and not from a public CA (I assume public CAs no longer issue certs >12 months)
Has anyone had a bad experience with a cert that is valid for such a long lifetime?
Below is the message in ISE 3.1 when trying to import such a certificate.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 06:01 PM - edited 07-13-2022 06:02 PM
Was the cert you installed a private PKI certificate? The change was specific to publicly trusted certificates and not internal PKI.
https://www.ssl.com/blogs/398-day-browser-limit-for-ssl-tls-certificates-begins-september-1-2020/
"My company has a privately trusted root CA. Are privately trusted SSL/TLS certificates subject to the new 398-day limit?
No. Apple’s change only extends to publicly trusted root CA certificates pre-installed on its devices, including SSL.com’s roots. Root certificates installed by a user or administrator are not affected by the 398-day restriction."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 06:01 PM - edited 07-13-2022 06:02 PM
Was the cert you installed a private PKI certificate? The change was specific to publicly trusted certificates and not internal PKI.
https://www.ssl.com/blogs/398-day-browser-limit-for-ssl-tls-certificates-begins-september-1-2020/
"My company has a privately trusted root CA. Are privately trusted SSL/TLS certificates subject to the new 398-day limit?
No. Apple’s change only extends to publicly trusted root CA certificates pre-installed on its devices, including SSL.com’s roots. Root certificates installed by a user or administrator are not affected by the 398-day restriction."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 07:32 PM
Wow that's a revelation! I had no idea that it was that subtle. In that case it makes sense to make the cert a bit longer lived to avoid that annual hassle of cert renewals (and application restarts).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2022 04:43 AM
Never had any issues with internal certifcates as @Damien Miller mentioned. For public certificates on guest portal though, I have had guest endpoints not trust the certificate once the 398th day has passed.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide